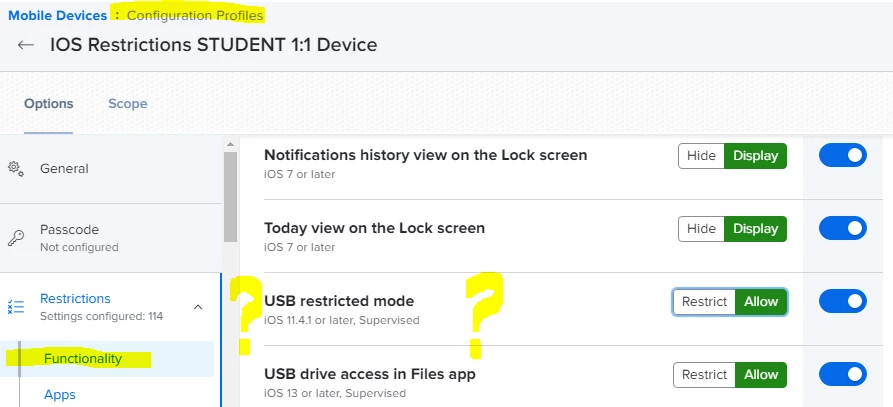
iPads that sit on lock screen for a few hours, go to partial sleep mode which disconnects from WiFi. The only way to connect them to WiFi is to wake it up and go to home screen. If an iPad is locked with passcode and not connected to WiFi, how will it complete the "Clear passcode" command through Jamf? There is literally no way to connect back to the internet using the same WiFi, Ethernet or Internet Sharing. In the past, people claimed that Ethernet to lightning adapters worked, but since iOS 11.4.1, USB restricted mode disabled the use of dongles at the lock screen.
We have a lot of iPads for staff that are simply added to Jamf without any configuration policies applied to them. I know there is an option to enable/disable USB restricted mode under configuration policies, but the problem is that we are not applying any policies to these iPads. So by default, USB restricted mode is Enabled which prevents use of dongles while at the lock screen.
The only way to solve this matter is to Wipe through iTunes or Configurator. However, all data will be gone and that is not good at all.
Does anyone have a better solution to this problem? Is there a way to apply Apple's default policies through Jamf and only modify the USB restricted mode policy? Of course, this will not fix the problem for currently locked iPads, but it could prevent in the future.