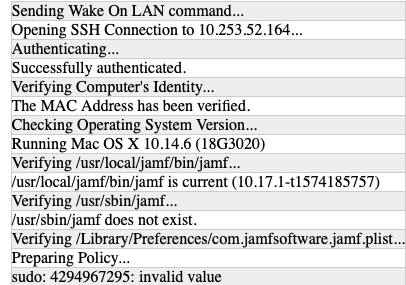
A random number of Macs in my environment have lost the ability to use sudo from a terminal. I have tried local admin user, ARD send Unix command as root, and JAMF Remote. I am trying a simple jamf recon and the result is:
sudo: 4294967295: invalid value.
Google turns up a few articles:
https://www.sudo.ws/alerts/minus_1_uid.html
https://news.ycombinator.com/item?id=21366177
I am not a Unix or Linux expert to understand why this is occurring or how to fix it. I do know that I have not edited the sudoers file, I can log into a local admin account and run normally if I don't use terminal requiring sudo, I can log in as an AD admin and get the same error message sending terminal commands using sudo, and logging in as a standard AD user I can su to a local admin account, but can't run commands using sudo.
These are computers that were installed with a fresh 10.14. OS and apps from our JAMF server and worked normally until I noticed sudo failing Wednesday. They were not imaged, they all work as expected with this exception.
I looked at permissions of the sudoers file on a working Mac. Admin and wheel are read only, everyone is no access. On the non working Macs, Fetching is in place of admin, wheel is read only, and everyone is no access. My conclusion is that the permissions are wrong and that's why sudo fails, but I know nothing of why this has happened or if this is the only anomaly regarding these permissions and how to repair it.
Sorry for the long winded post, but no one in my organization knows what to do. Thanks.