CIS 1 Allow Touch ID to unlock your mac what needs to be deactivated?
Hi Hope you can help, how do we allow users to use Touch ID rather than the full password each time sleep is activated. What needs to be unticked in the list of Managed Rules in compliance?
Thanks
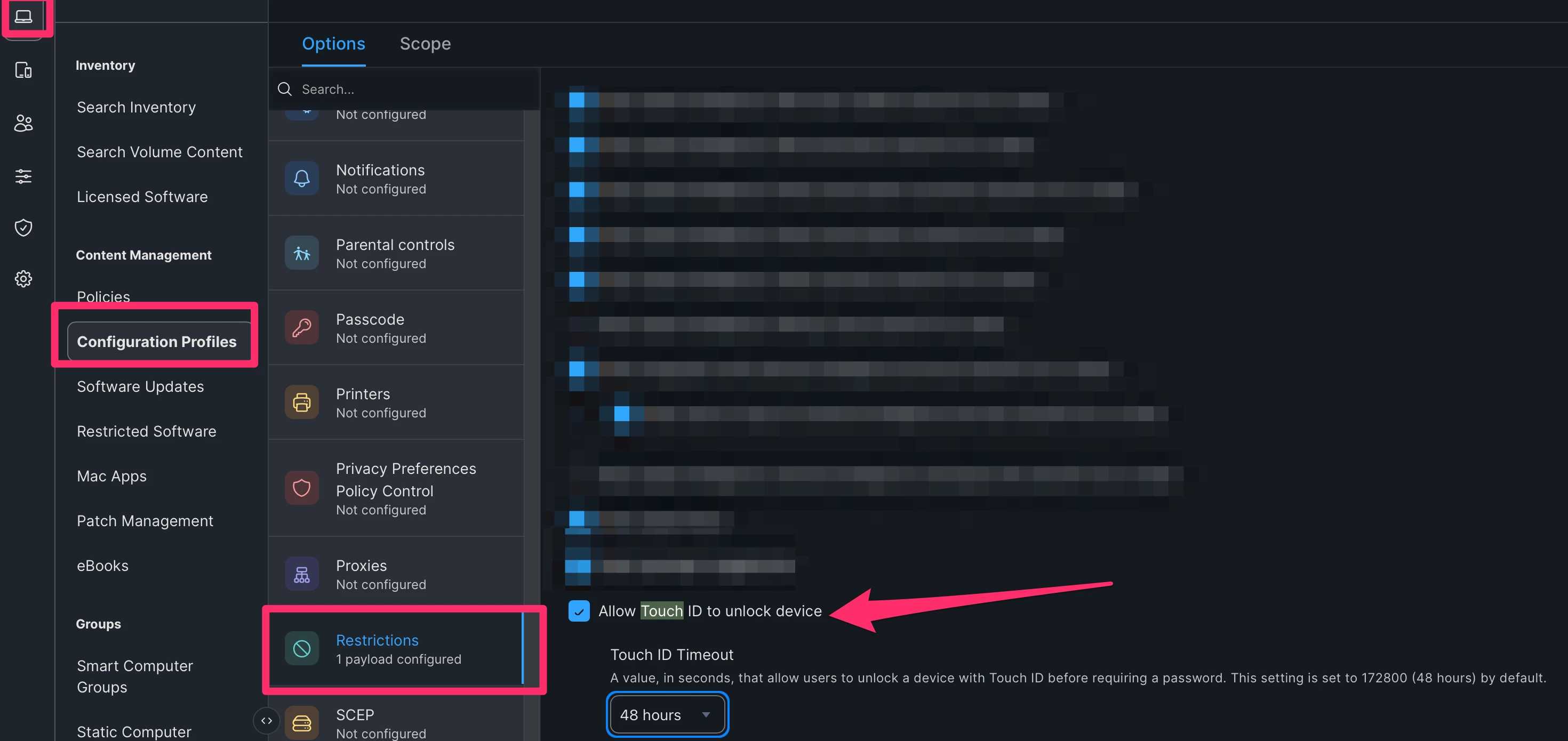
Do you have a Restrictions payload that doesn’t “Allow Touch ID to unlock device?”
I found this on either the security or regulatory-compliance slack channels. Here’s the plist for com.apple.loginwindow
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>screenUnlockMode</key>
<integer>1</integer>
</dict>
</plist>
Thanks for the replies.. As this is being pushed out via the Compliance Rules under CIS Level 1, I think I will need to disable the rule ideally that controls the Touch ID, so it doesn’t conflict with other policies or profiles.
Thanks
Hi
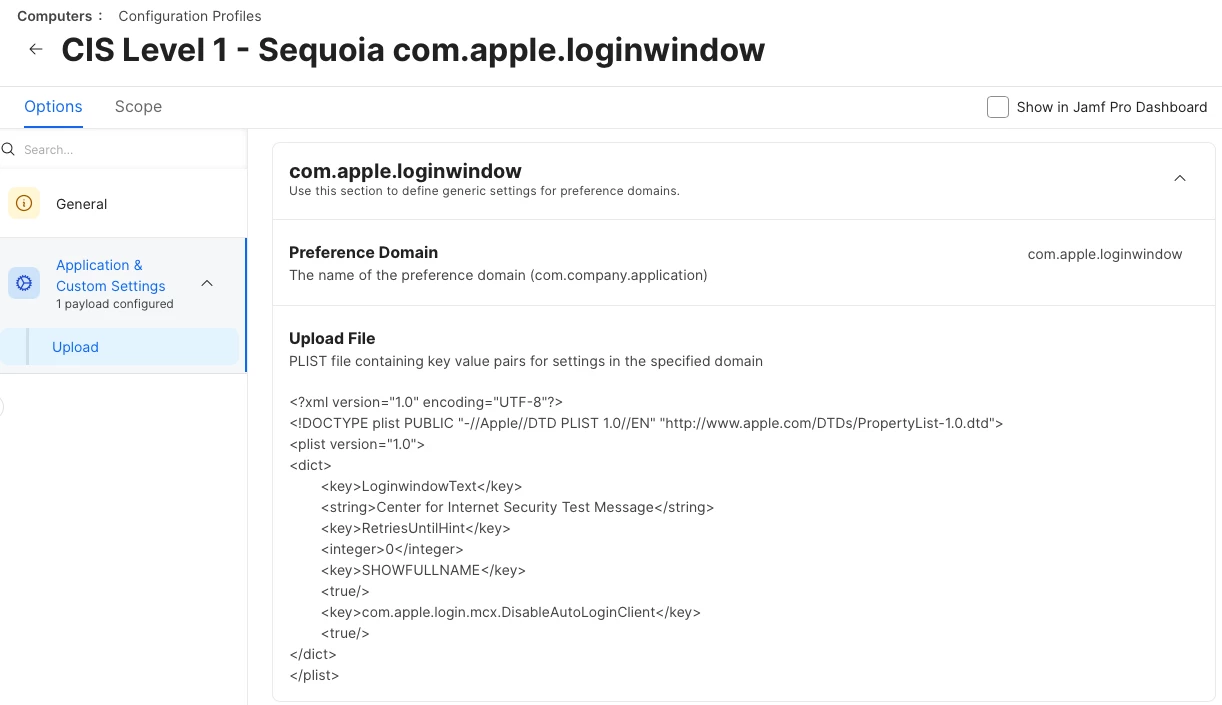
Looking at the config profile generated by the Compliance rules in Jamf Pro, I see the below plist.
Not sure if that helps to solve your problem - I haven’t found any CIS rule that would control login using Touch ID.
Hi JanVozenilek85
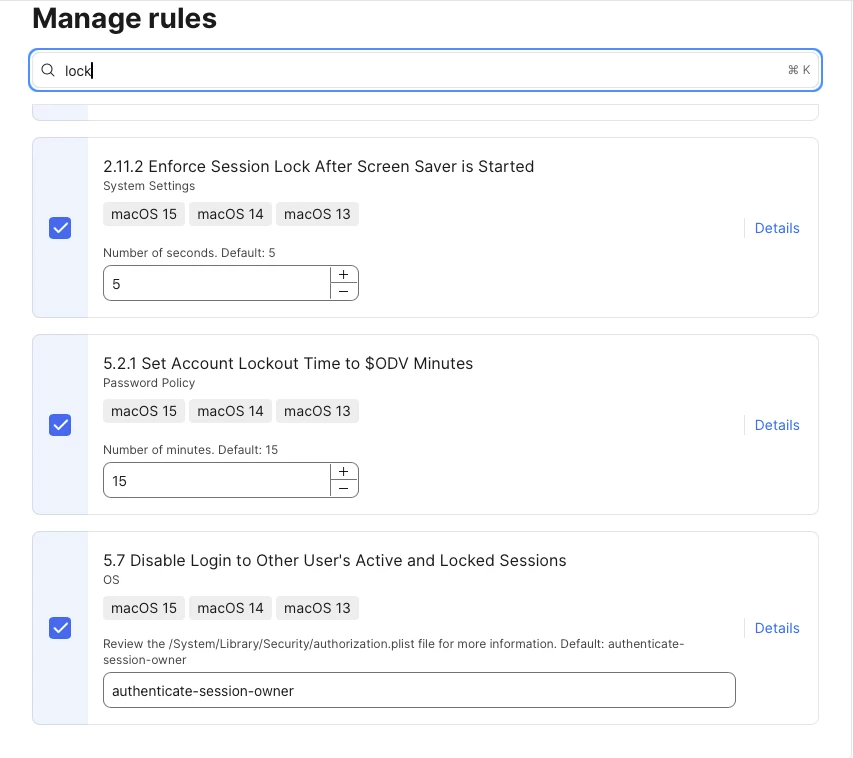
Thanks for this I'll keep looking into this, as these are the rules which I have disabled already. 2.11.3 & 2.11.4
Only as we use connect and didn’t need the ‘Centre for Internet Security Test Message’ appearing as well.
The issue is outlined in rule 5.7 right in the CIS GUI in Jamf. It’s also outlined here:
5.7 Disable Login to Other User's Active and Locked Sessionsos_unlock_active_user_session_disable
Discussion
The ability to log in to another user’s active or locked session MUST be disabled.
macOS has a privilege that can be granted to any user that will allow that user to unlock active user’s sessions. Disabling the admins and/or user’s ability to log into another user’s active and locked session prevents unauthorized persons from viewing potentially sensitive and/or personal information.
| NOTE | Configuring this setting will change the user experience and disable TouchID from unlocking the screensaver. To restore the user experience and allow TouchID to unlock the screensaver, you can run /usr/bin/sudo /usr/bin/defaults write /Library/Preferences/com.apple.loginwindow screenUnlockMode -int 1. This setting can also be deployed with a configuration profile. |
| WARNING | This rule may cause issues when platformSSO is configured. |
Organization defined value
Review the /System/Library/Security/authorization.plist file for more information.
authenticate-session-owner
Great thanks daniel_behan, I will do some testing and hopefully get this sorted out.
Check out the macOS Security Project, it’s a much simpler process for dealing with CIS.
https://github.com/usnistgov/macos_security
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.
