If I'm not mistaken, you can do this in Configuration Profiles, where you can only allow connection to recognized Wi Fi networks.
What section of config profiles?
Looks like a Configuration Profile with a Network payload containing the correct Wi Fi network information, with Auto Join enabled, should do this.
I think that will automatically have the iPad or Mac join the correct WiFi network, I do not think it will prevent the user from joining a different WiFi network
You could use JAMF to pull a report for all School-owned airport MAC addresses and then have your networking team blacklist them from getting an IP on the "Guest" network, if that's something they're willing to do.
That sounds like it would work but also sounds like a huge amount of work. I was hoping that there was some way within Jamf to do this
Here's what I was looking for.
https://www.jamf.com/jamf-nation/feature-requests/4961/lock-ipad-to-ssid
This was, at least previously, possible.
This will work with one big caveat that makes it a non-starter for us. I do want users to be able to join other wifi networks when the iPad or Mac is off campus. I just want the ability to restrict them from joining one particular wifi network when on campus
Found it... so it's for-sure you'll be able to do this on iOS.
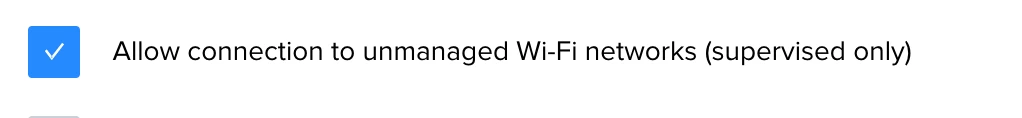
If I uncheck this option and an iPad or Mac is taken off campus to a coffee shop with a wide open wifi network, I am thinking it will not be able to join it. Is that correct? That would be a problem
Right. You might need a different solution, then. Sorry!
One thing you can try. Deploy a profile with the SSID of the guest network, but with the WRONG password (in this case, ANY password).
If I have already deployed a WiFi profile that works in joining the device to the proper secure wifi network, will the new wifi profile I push out just keep attempting to join my VCSguest wifi network over and over when of course it cannot since I have provided the incorrect password?
I left out an important detail, uncheck the "auto join" with that guest network profile.
You can have multiple profiles for multiple SSID payloads. In fact you should keep them separated for simplicity and troubleshooting.
Have you considered getting the networks team (if you have such a thing) to look at it from the other side.
Why not have the WiFi network refuse (or divert to an information page) connections from a list of owned devices, you could probably generate the list (or have it pulled automatically) from JAMF if it didn't exist.
This would mean you didn't need to lock the devices down so people could still use them at home etc...

