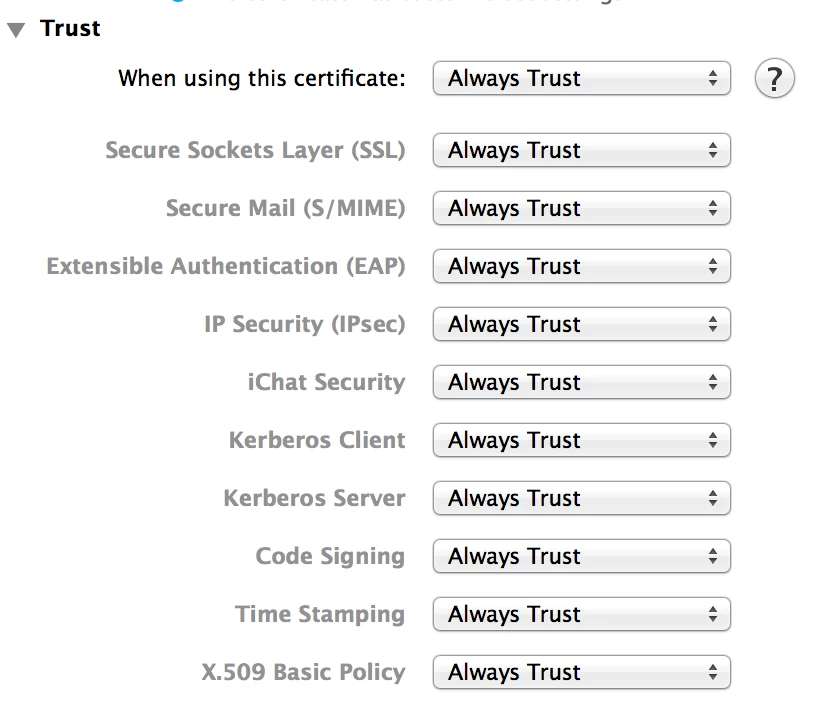
I'm deploying an 802.1x certificate to some of our endpoints using a config profile, and it's landing and appears to be trusted, but only using the system defaults. I've not been able to figure out a way to change these trust settings (Always trust) while still using a config profile (did find a link that described how to package it and manually trust it, but would rather not do it manually).
How are you guys doing this in your environments? If it helps, we're on 9.72.