Working on revamping all the EAs for Code42 CrashPlan to be compatible in 2020 version 8.2+
@jamf is there a way we can get the CrashPlan (now Code42) Templates all updated with these revised EAs?
I will be updating this post in the next 24-48 hours as I get them worked through the rest of the way. If anyone has ideas on how to simplify the code down short, I'm all ears :) I prefer to do Python looking at the JSON returned values to get the correct Key-value vs. grep/awk/sed (bs) as it makes the code more easily read and it ensures that even if the location of the keypair gets moved, we're still okay.
Remember to keep your Code42 account limited to the lowest Roles possible to do its required job, which in this case is Cross Org Security Viewer: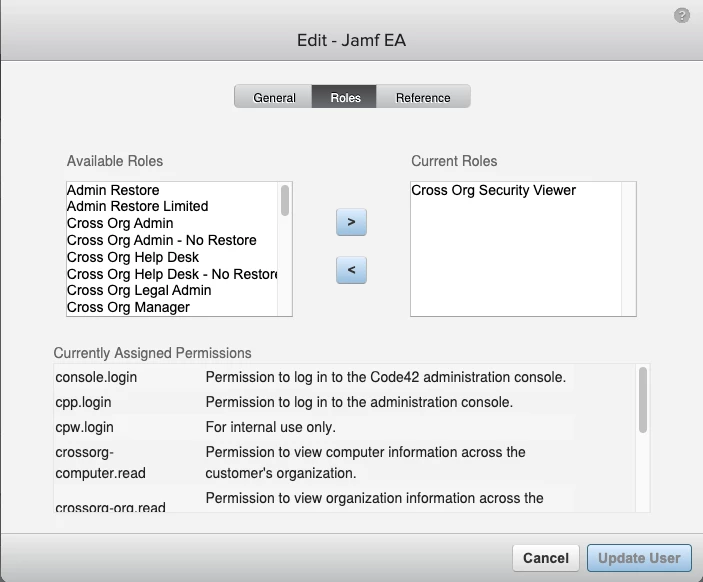
.
.
.
.
To download the EAs: Github - Code42 EAs
.
.
.
LAST CONNECTED
#!/bin/sh
####################################################
### INFO ###
#Revamped by: Rhio
#Revamped on: August, 4th, 2020
#Display Name: Code42 - Last Connected
#Description: This attribute displays the last time Code42 established a connection with the server.
#Data Type: Date
#Input Type: Script
####################################################
####################################################
### VARIABLES ###
#use the server address utilized to log into a fresh client installed manual deployment
CP_ServerAddress="central.crashplan.com"
#This port should work for everyone, it may be different if you have an on-prem install and have altered your ports from the default ports
CP_ServerPort="4285"
#Configure an API account with the minimum roles possible, for cloud customers, this would be Cross Org Security Viewer and must be a LOCAL account within the console, this will allow READ access ONLY. If you are a cloud customer, this is also required to be a full email address.
CP_AdminUsername="yourAPIacct@yourorg.com"
#Configure to your API account PW. If desired, you could encrypt this with base 64 or a keypair stored in a separate file or config profile elsewhere on the machine to avoid having it in plaintext. Since you should have limited the rights of this account, the vulnerability will be reduced.
CP_AdminPassword=""
####################################################
####################################################
### LOGIC ###
if [ "$CP_ServerAddress" == "" ] || [ "$CP_ServerPort" == "" ] || [ "$CP_AdminUsername" == "" ] || [ "$CP_AdminPassword" == "" ];then
echo "Please ensure all variables are set in the extension attribute script."
else
if [ -f /Library/Application Support/CrashPlan/.identity ];then
#Checks the Unique Code42 Identifier to the currently running backup; the directory may need to be updated if they ever change the name of their cached settings directory
GUID=`/bin/cat /Library/Application Support/CrashPlan/.identity | grep guid | sed s/guid=//g`
#Queries API of your Code42 instance then uses Python to parse the JSON that's returned for the nested key pair (under "data") of lastConnected
value=`/usr/bin/curl -u "$CP_AdminUsername":"$CP_AdminPassword" -k "https://"$CP_ServerAddress":"$CP_ServerPort"/api/Computer/"$GUID"?idType=guid" | python -c 'import json,sys;print json.load(sys.stdin)["data"]["lastConnected"]'`
#Converts the time format from the resulting JSON to the Jamf Smart Group compatible format
result=`/bin/date -j -f "%Y-%m-%dT%H:%M:%S" "$value" "+%Y-%m-%d %H:%M:%S"`
echo "<result>$result</result>"
else
echo "<result>Not installed</result>"
fi
fi
####################################################.
.
.
ALERT STATUS
.
#!/bin/sh
####################################################
### INFO ####Revamped by: Rhio
#Revamped on: August, 8th, 2020
#Display Name: Code42 - Alert Status
#Description: This attribute displays the Alert Status of Code42.
#Data Type: String
#Input Type: Script
####################################################
####################################################
### VARIABLES ###
#use the server address utilized to log into a fresh client installed manual deployment
CP_ServerAddress="central.crashplan.com"
#This port should work for everyone, it may be different if you have an on-prem install and have altered your ports from the default ports
CP_ServerPort="4285"
#Configure an API account with the minimum roles possible, for cloud customers, this would be an Org Admin or All Org Admin, and must be a LOCAL account within the console. If you are a cloud customer, this is also required to be a full email address.
CP_AdminUsername="yourAPIacct@yourorg.com"
#If desired you could encrypt this with base 64 or a keypair stored in a separate file or config profile elsewhere on the machine to avoid having it in plaintext. Since you should have limited the rights of this account, the vulnerability should be reduced.
CP_AdminPassword=""
####################################################
####################################################
### LOGIC ###
if [ "$CP_ServerAddress" == "" ] || [ "$CP_ServerPort" == "" ] || [ "$CP_AdminUsername" == "" ] || [ "$CP_AdminPassword" == "" ];then
echo "Please ensure all variables are set in the extension attribute script."
else
if [ -f /Library/Application Support/CrashPlan/.identity ];then
#Checks the Unique Code42 Identifier to the currently running backup; the directory may need to be updated if they ever change the name of their cached settings directory
GUID=`/bin/cat /Library/Application Support/CrashPlan/.identity | grep guid | sed s/guid=//g`
#Queries API of your Code42 instance then uses Python to parse the JSON that's returned for the nested key pair that's in an array (under "data") of alertStates
value=`/usr/bin/curl -u "$CP_AdminUsername":"$CP_AdminPassword" -k "https://"$CP_ServerAddress":"$CP_ServerPort"/api/Computer/"$GUID"?idType=guid" | python -c 'import json,sys;print json.load(sys.stdin)["data"]["alertStates"]'`
#Filters off unwanted parts of the value due to the results being in an array
result=`echo "$value" | sed 's/...(.*)/1/' | sed 's/(.*)../1/'`
echo "<result>$result</result>"
else
echo "<result>Not installed</result>"
fi
fi
####################################################.
.
.
BACKUP COMPLETE PERCENTAGE
.
#!/bin/sh
####################################################
### INFO ###
#Found at: https://github.com/RHI0/Code42-EAs
#Revamped by: Rhio
#Revamped on: August, 4th, 2020
#Display Name: Code42 - Percent Complete
#Description: This attribute displays the last percentage completion of the first archive of the GUID.
#Data Type: Integer
#Input Type: Script
####################################################
####################################################
### VARIABLES ###
#use the server address utilized to log into a fresh client installed manual deployment
CP_ServerAddress="central.crashplan.com"
#This port should work for everyone, it may be different if you have an on-prem install and have altered your ports from the default ports
CP_ServerPort="4285"
#Configure an API account with the minimum roles possible, for cloud customers, this would be an Org Admin or All Org Admin, and must be a LOCAL account within the console. If you are a cloud customer, this is also required to be a full email address.
CP_AdminUsername="yourAPIacct@yourorg.com"
#If desired you could encrypt this with base 64 or a keypair stored in a separate file or config profile elsewhere on the machine to avoid having it in plaintext. Since you should have limited the rights of this account, the vulnerability should be reduced.
CP_AdminPassword=""
####################################################
####################################################
### LOGIC ###
if [ "$CP_ServerAddress" == "" ] || [ "$CP_ServerPort" == "" ] || [ "$CP_AdminUsername" == "" ] || [ "$CP_AdminPassword" == "" ];then
echo "Please ensure all variables are set in the extension attribute script."
else
if [ -f /Library/Application Support/CrashPlan/.identity ];then
#Checks the Unique Code42 Identifier to the currently running backup; the directory may need to be updated if they ever change the name of their cached settings directory
GUID=`/bin/cat /Library/Application Support/CrashPlan/.identity | grep guid | sed s/guid=//g`
#Queries API of your Code42 instance then uses Python to parse the JSON that's returned for the nested arrayed key pair (under "data" > "backupUsage") of percentComplete for the first archive. If a client is backing up to more than one physical location you will need to add a loop to iterate over the array
value=`/usr/bin/curl -u "$CP_AdminUsername":"$CP_AdminPassword" -k "https://"$CP_ServerAddress":"$CP_ServerPort"/api/Computer/"$GUID"?idType=guid&incBackupUsage=true" | python -c 'import json,sys;print json.load(sys.stdin)["data"]["backupUsage"][0]["percentComplete"]'`
echo "<result>$value</result>"
else
echo "<result>Not installed</result>"
fi
fi
####################################################





