Hey @sdiver , we currently used machine based authentication with EAP-FAST but I also had EAP-TLS working for wired as well.
Basically what I found out is that in order for EAP-TLS to work, your certificate template from AD must use the UPN name for the SAN in the certificate. If you use the DNS name, it will not connect on EAP-TLS. DNS will work for SAN on EAP-FAST though.
Also just verify your trust chain with your certs are all correct. We drop our ethernet configuration profile with our AD information (CA server, certificate template) and network payload. If no other profile is delivering your certs, you can add your certs to that same profile for ethernet. But if they are already on the Mac via another profile, from wireless for example, it's not needed.
Also, if you can, for ethernet at least make your profile in profile manager, sign it and upload it to the JSS. There was a bug that if you made a brand new ethernet payload configuration in the JSS and deployed it, it would ignore system mode and put the configuration profile in user mode, forcing credentials to be put in. I was told by JAMF that it was resolved in 9.96 but I haven't tested it yet.
Hopefully this helps you out.
@sdiver
@perrycj is spot on, Did you confirm those settings. We are on EAP-TLS. At the bottom of the link below are the settings for our profile.
link
Specs:
OS X 10.11.6
JSS 9.65
hth
Larry
We just rolled this out using a linux radius server & external CA. Pushed out the root & intermediate CA certs with a configuration policy beforehand. Then used a script to download, import & assign the unique certs to the target SSID. Used the serial number as the common name.
I'm assuming that you're bound to AD as well?
We use this setup, and I had to make sure that the "servicePrincipalName" attribute for the Computer Object in AD was set correctly for each device. This should be in the format of "host/[FQDN of device]".
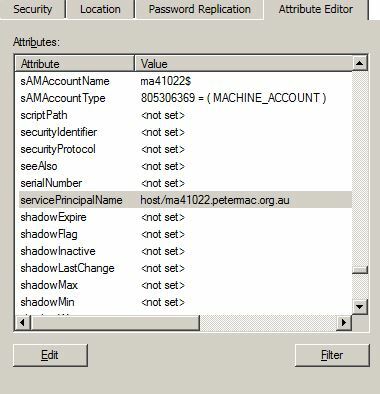
I also had to set up a script to run on the Mac itself for a kerberos service, otherwise it clears out this attribute everytime it authenticates:
1dscl . -create Computers/localhost kerberosServices host
@perrycj Thanks...we haven't even gotten to ethernet yet. Working our way through WiFi connectivity first. We can get the necessary certificates to the Mac via a Configuration Profile with Certificate, AD Certificate, and Network payloads. It's just the certificate having the correct Common Name or Subject Alternative Name information to authenticate properly.
@LSinNY Your link looks like you're using PEAP for machine authentication, correct? We did get that working, and will probably move forward with that if we cannot get machine-based EAP-TLS authentication working.
@Aaron Interesting...perhaps that would explain why I cannot get the correct information in the certificate. Something I will definitely try when I am back in the office next week. How did you implement that script, and how often are you running it?
@sdiver I normally only have to run it once, so I have it as part of my initial setup script. There are some random moments where something will get changed on the client, and it will update the AD record, and then the Mac can't connect anymore, so there's not much point in having it as a policy (unless you have a BYOD section to your network which can access your JSS). When that happens, I just run the command manually - I'm yet to determine what causes it, but it doesn't happen terribly often, so it's not a big priority for me.
When I was doing this, I found that everything worked better if I handrolled and manually signed the config profile before uploading it to the JSS, as there were bugs which were mangling the profile. Can't say if that's been fixed in recent versions.
@perrycj if we make changes in the certificate template from AD to use UPN name for the SAN in certificate, is it going to impact other windows machine's authentication on the same wifi.
@Tusharma Yup, if using the same certificate template. You should be able to create another certificate template just for using UPN names, if you want.
But anything using the same template will be affected.







