Has anyone had any experience in deploying Fortinet's FortiClient to computers? I get a DMG from our on-prem controller but that doesn't install when I use Jamf Pro to install onto client machines
- Home
- Community
- Get Support
- General Discussions
- Deploying FortiClient
Deploying FortiClient
- June 4, 2020
- 49 replies
- 615 views
49 replies
- Valued Contributor
- April 23, 2021
@JonWVC You´re welcome. Just let me know, if it worked for you. I´ve also created a solution for future updates of FortiClient - to deploy it to users who already have Forti installed. The client blocks repeated installation. If you also need this, I start the translation of the instructions :-)
 +3
+3- New Contributor
- April 25, 2021
@mickl089, I would like that. Hopefully it will set the configuration right for the already deployed machines.
- Valued Contributor
- April 26, 2021
@jeroenkahle If a kill process script is placed in front of it, this should work even for FortiClients that have already been rolled out.
- Valued Contributor
- April 26, 2021
Step by Step:
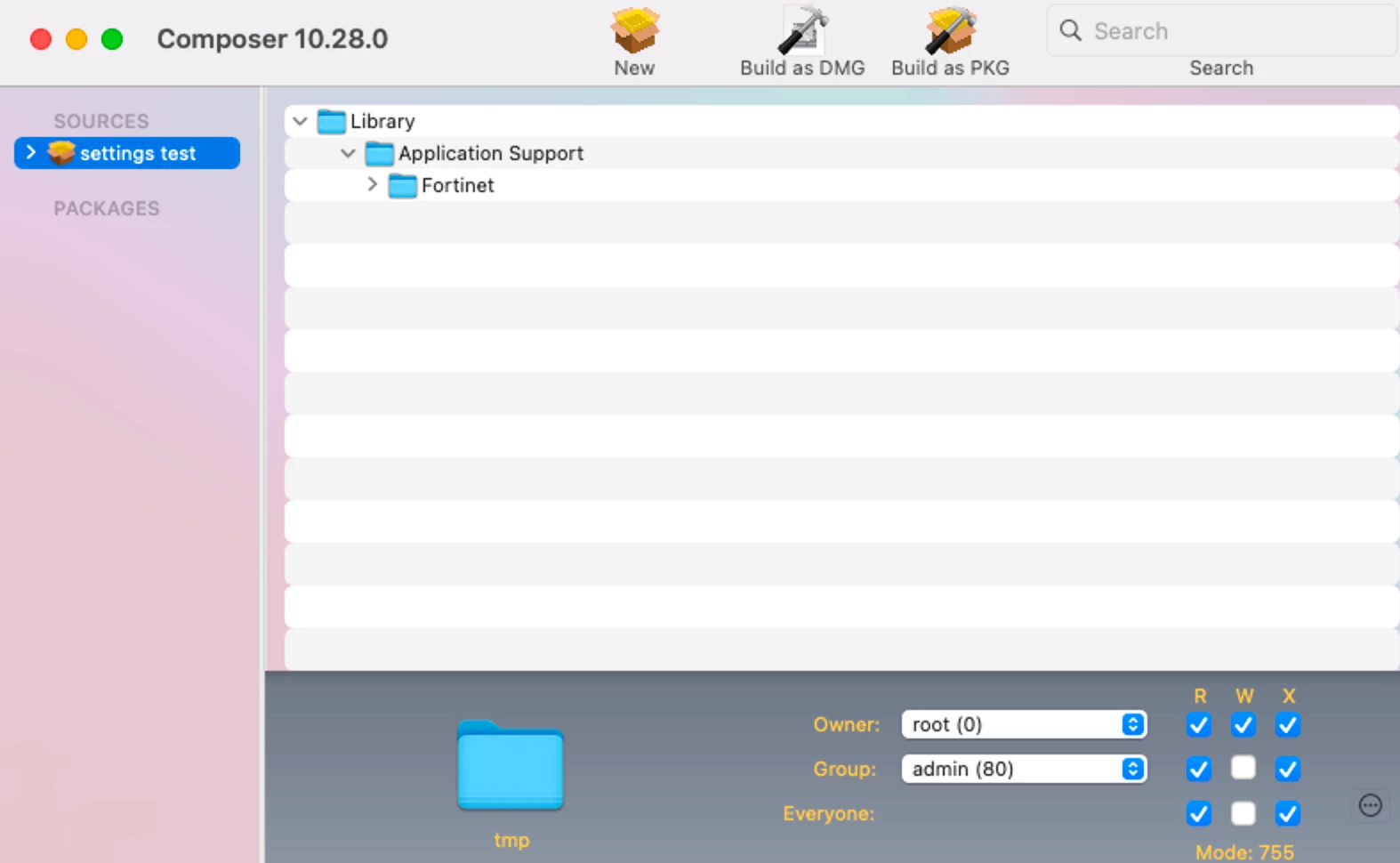
The packaging basically consists of two parts. On the one hand there is an install.mpkg in the DMG file of the manufacturer, this can be pulled separately and uploaded unprocessed in Jamf.
This works either with the tool "Jamf Admin", which is available for download in the Jamf Nation with a registered account, or directly via the Jamf interface in the settings under "Computer Management" and then "Packages".
Basically, the FortiClient policies are now configured so that the settings are installed in a first step. Otherwise the smooth connect will not work.
The packaging for this is best done in a test environment by installing the FortiClient including settings from the DMG and then separating the settings via Jamf Composer (with the snapshot function before and after).
For this purpose, the following files and folders must be packed into a PKG: Picture 1
Updating the client
If a new version of the client is announced, one takes the DMG file, opens this and pulls out the "install.mpkg".
This file is then uploaded to the Jamf server using the method described above and overwrites the old installer.
The policy now looks like this: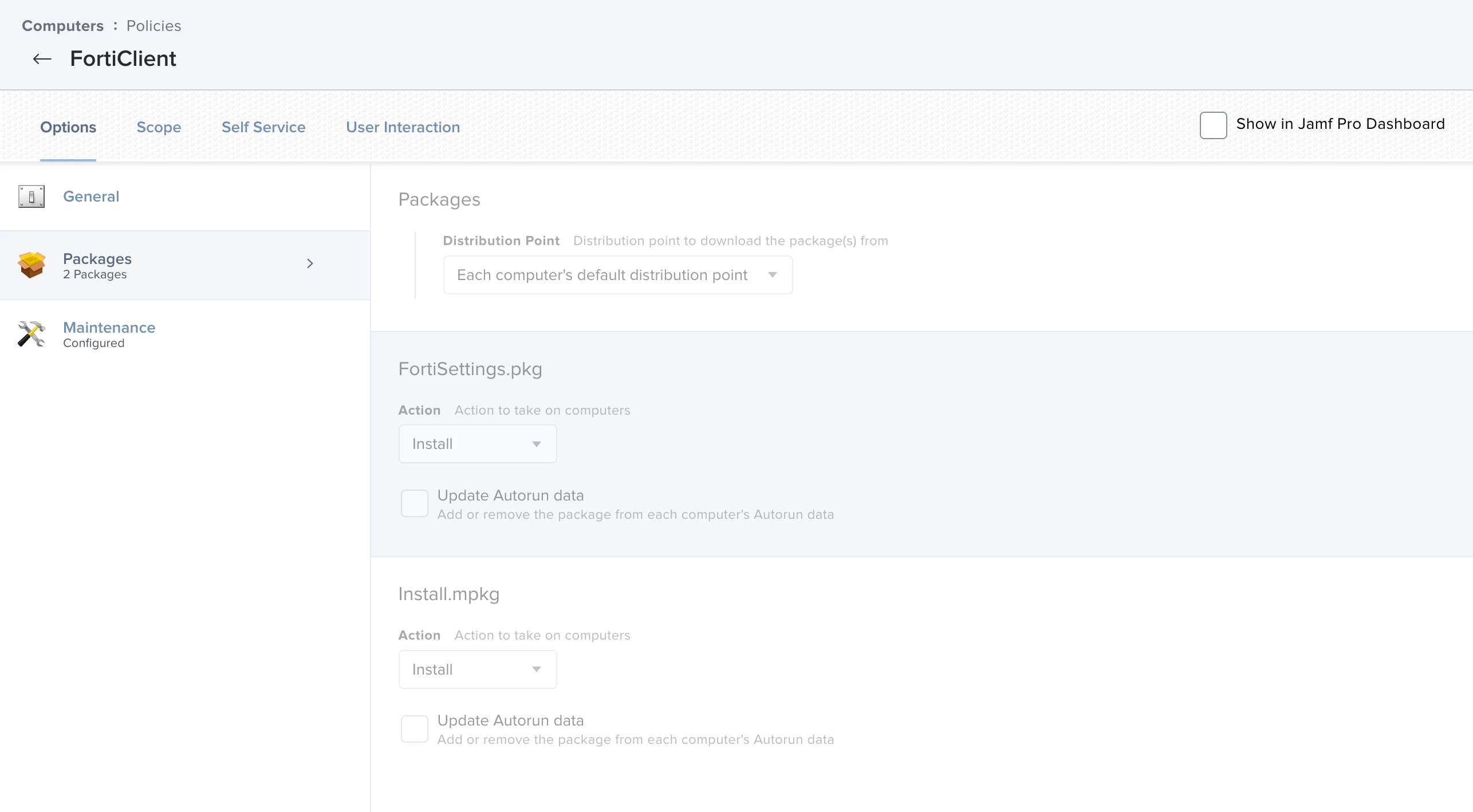
Please note that the settings are in the first place, otherwise the login with the client in the VPN does not work, because the config is not loaded.
Jamf now overwrites all policies that included the "install.mpkg" by itself, you don't have to update the policies by hand anymore.
Differences between the different FortiClient policies
For a correct update via Self Service to work, it must be ensured that the FortiClient is not running at the time of the update.
For this purpose, a policy was written that is similar to the normal installation, but still loads a script in advance that kills all Forti processes. Otherwise, the update would throw errors, which would then be acknowledged in Self Service.
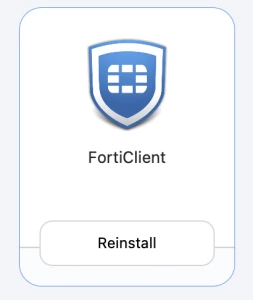
The normal FortiClient installer in Self Service, which all users will see who have not yet installed FortiClient on their computer. This will then also serve the AutoDeploy (automatic computer installation via Jamf).
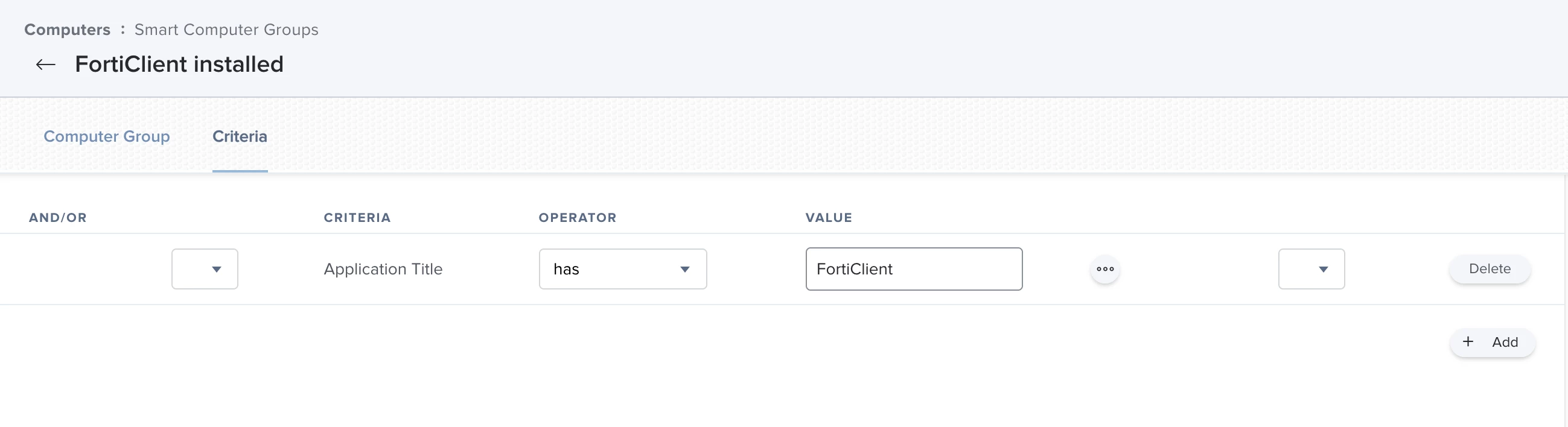
In advance, a Smart Comupter Group was created for this purpose, which contains all computers that do not have FortiClient installed. The scope for this policy was set to this computer group as exclusion. This means that the computer group "FortiClient installed" was defined as an exclusion.
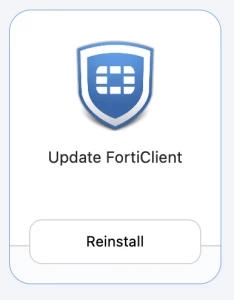
The update variant that is only seen by users listed in the "FortiClient installed" group. That is, the computer group "FortiClient installed" was placed here as a target in the scope.
The Smart Computer Group "FortiClient installed
To ensure a clean separation between the update function and the pure installation, it is necessary to separate the computers for this purpose as well.
Computers that have already installed FortiClient will only see the update function in Self Service, which includes the process kill as the only difference in its policy in addition, so that a clean install over the old version works.
This group can be found in the menu bar on the left under "Smart Computer Groups".
The script that kills the Forti-Client process to be able to apply an update:
A simple two-line command that can be found in the scripts under "Settings" and then "Computer Management" and "Scripts" - named: "kill FortiClient".
Both commands terminate possible running processes of the VPN solution.
killall FortiClientAgent killall FortiClient
Summary or structure of the policy
The following configurations are necessary to ensure both installation and update:
Package: FortiSettings.pkg - as described above necessary for the basic configurations Package: install.mpkg - as described above the pure installer for the client Maintenance: this setting ensures that an update inventory is run after the installation is complete. This way Jamf is informed that the FortiClient has been installed and the computer immediately gets automatically into the Smart Computer Group "FortiClient installed" - afterwards only the update version of the tool is visible in Jamf, which contains the already described process kill.
 +6
+6- Contributor
- June 4, 2021
@mickl089 That is a really well-written walkthrough. I especially like the use of smart groups. Thanks for the info!
- Valued Contributor
- June 8, 2021
So until this morning, Forticlient didn't need any PPPC for our usage, but something "changed" (inquiring) and now fctservctl wants full disk access. Anyone have a PPPC profile they're using? I'd rather not play cat and mouse with this one...
- Valued Contributor
- June 9, 2021
@mickl089 we're on 6.2.x. Looks like "normal" is giving Full Disk access to FortiClient and fctservctl. But not sure that's it.
- Valued Contributor
- June 10, 2021
@rstasel this should also works for you, if you don´t already know this site:
https://docs.fortinet.com/document/forticlient/6.4.4/macos-release-notes/223986/special-notices
- Valued Contributor
- June 10, 2021
@mickl089 Thank you! I literally could not find this info... we don't "own" forticlient as a service tool, and on our site, we're literally only using it for VPN. So this is good, thank you!
- Jamf Heroes
- March 8, 2022
Hate to bump an old post does this still hold true in v7.X.X and up?
 +6
+6- Contributor
- March 8, 2022
We haven’t rebuilt our package from 6.4.4 yet, but we’ve observed that 7.x.x requires a system extension and the addition of a few new PPPC items: Fctlsrv2 among them.
We’re deploying the VPN only client, I’ll see if I can find the release guide for 7.0.3, it had some detailed indications about the components that need to be enabled.
- Jamf Heroes
- March 8, 2022
We haven’t rebuilt our package from 6.4.4 yet, but we’ve observed that 7.x.x requires a system extension and the addition of a few new PPPC items: Fctlsrv2 among them.
We’re deploying the VPN only client, I’ll see if I can find the release guide for 7.0.3, it had some detailed indications about the components that need to be enabled.
We found a ton of stuff in the release notes and a section called "Special Notice macOS" we did all of those but are still trying to figure out how to do the DMG properly to install via Jamf.
 +6
+6- Contributor
- March 8, 2022
We found a ton of stuff in the release notes and a section called "Special Notice macOS" we did all of those but are still trying to figure out how to do the DMG properly to install via Jamf.
Oh yeah, I see. If the install.mpkg is still available in the *.dmg that's what I plan to use, as per mickl089's process. It's what I did for version 6.4.4 and it worked like a dream.
https://community.jamf.com/t5/jamf-pro/deploying-forticlient/m-p/228591/highlight/true#M216822
- Jamf Heroes
- March 17, 2022
Oh yeah, I see. If the install.mpkg is still available in the *.dmg that's what I plan to use, as per mickl089's process. It's what I did for version 6.4.4 and it worked like a dream.
https://community.jamf.com/t5/jamf-pro/deploying-forticlient/m-p/228591/highlight/true#M216822
We are getting an error found here when installing things. Any thoughts on what we can do to get past this?
https://community.jamf.com/t5/jamf-pro/tutorial-forticlient-6-4-x-deploy-with-config/m-p/260674/highlight/true#M240521
- Valued Contributor
- August 16, 2022
So at this point I was able to put the cleanest policy to get FortiClient 7.x installed freshly and upgrade 6.x version.
You need to obtain the FortiClient DMG installer from FEMS server.
- Note: If this is an upgrade policy from previous version, it must have a removal script (run Before) of the current FortiNet client for the re-install policy, what works for me currently is:
#!/bin/bash
cd /
cd /Library/LaunchDaemons
sudo rm -rf com.fortinet.forticlient.*
cd /
cd "/Library/Application Support/Fortinet"
sudo rm -rf FortiClient
#kill FortiNet processes manually
killall FortiClient
killall FortiClientAgent
killall "FortiClient Helper"
#run FortiClientUninstaller from the Applications Folder
#open /Applications/FortiClientUninstaller.app
#delete FortiClient app and uninstaller from Applications to see if then FortiNet 7.x will install with AV component
sudo rm -rf /Applications/FortiClientUninstaller.app
sudo rm -rf /Applications/FortiClient.app
kill $(ps -e | grep Forti | awk '{print $1}')
sleep 5
Now, how I managed to setup the installation part:
- Rename the installer from FEMS server to "FortiClient_Installer.dmg" and copy to /Users/Shared/FortiClient_Installer.dmg
- Double check/mount the DMG to make sure the installer inside the DMG is named "Install.mpkg"
- Using JAMF Composer, package the "FortiClient_Installer.dmg" into a new DMG named "Install FortiClient_Users_Shared_DMG.dmg" so that when deployed by the policy from JSS, it would save the FortiClient_Installer.dmg to machine's \\Users\\Shared folder
- If upgrading to a new version: upload/replace the current "Install FortiClient_Users_Shared_DMG.dmg" on Jamf Admin app and update the current version in General - Info
- Now the script which will mount the DMG and install the MPKG is:
#!/bin/bash
# Needs to have a DMG present at /Users/Shared/
# Variables
dmgPath="/Users/Shared/FortiClient_Installer.dmg"
packageName="Install.mpkg"
# Mount the DMG, and save its device
device=$(/usr/bin/hdiutil attach -nobrowse "$dmgPath" | /usr/bin/grep "/Volumes" | /usr/bin/awk '{ print $1 }')
echo "device is: $device"
# Using the device, determine the mount point
mountPoint=$(/usr/bin/hdiutil info | /usr/bin/grep "^$device" | /usr/bin/cut -f 3)
echo "mountPoint is: $mountPoint"
# Pointing to pkg/mpkg manually
pkgToinstallManual="$mountPoint"/Install.mpkg""
echo "pkgToinstallManual is: $pkgToinstallManual"
# Install the package
/usr/sbin/installer -verbose -pkg "$pkgToinstallManual" -target /
sleep 15
# Detach the volume and remove the DMG with installer
/usr/bin/hdiutil detach $device
rm -rf /Users/Shared/FortiClient_Installer.dmg
exit 0
Then you need a policy on JSS, which will include the DMG which will place the FortiClient installation DMG into /Users/Shared folder, then you need the installation script to run After (second one in my post) and if there is currently FortiClient/FortiNet is installed - you need the removal script (the first one in my post). Please note, we are upgrading from simply FortiNet VPN 6.x to FortiNet 7.x with AV included, so macs which already have FortiClient - they only have the VPN component. I have tried the removal script (first one in my post) on FortiClient 7.x with AV component and it worked, but it requires a reboot after you run the script.
The only other issue we have is the Full Disk Access, which based on Apple responses at this point can't be automated... whatever I have tried via configuration profiles/JSS - it removed most of the prompts, but we still get the "Permission is required for full protection", which comes from the AV component and only by manually allowing it in the Privacy tab - works...
Overall FortiClient vendor does not provide much documentation on how to deploy their software automatically on macs, but this is the closest I got so far...
 +3
+3- New Contributor
- September 16, 2022
I somehow lose some of our machines over time. In the search how to re-add them to EMS i stumbled upon the Linux commandline commands. And yes, they work on the FortiClient 7 versions for the Mac (not on previous version). And because that works, i can simply deploy the .mpkg and afterwards use the command to register to EMS. So no need to push the Fortisettings structure before installing the main Forticlient. Now it is just install, fire off the command and be done. Hope it helps anyone
#!/bin/bash
## Add FortiClient configuration if EMS connection is broken or register the cleaninstall
/Library/Application\\ Support/Fortinet/FortiClient/bin/epctrl -r fqdnofserver y
 +3
+3- New Contributor
- September 26, 2022
I somehow lose some of our machines over time. In the search how to re-add them to EMS i stumbled upon the Linux commandline commands. And yes, they work on the FortiClient 7 versions for the Mac (not on previous version). And because that works, i can simply deploy the .mpkg and afterwards use the command to register to EMS. So no need to push the Fortisettings structure before installing the main Forticlient. Now it is just install, fire off the command and be done. Hope it helps anyone
#!/bin/bash
## Add FortiClient configuration if EMS connection is broken or register the cleaninstall
/Library/Application\\ Support/Fortinet/FortiClient/bin/epctrl -r fqdnofserver y
Thanks for this. We were finding that for some weird reason if we deployed our 6.4.8 via Software Center then everything working (including EMS registration), but when we told Jamf to deploy to all machines that didn't have it the EMS config file wasn't populating.
Deploying this as a script has resolved that for us!
 +3
+3- New Contributor
- September 27, 2022
There is a issue with my script, because of the untrusted certificate. The answer, in this case, YES is not send. So i try to work around this and got some like this which seems to do the trick.
#!/bin/sh
## Add FortiClient configuration if EMS connection is broken
echo
echo - Are we connected to EMS?
/usr/bin/expect <<EOF
spawn /Library/Application\\ Support/Fortinet/FortiClient/bin/epctrl -r fqdn-or-ip-address
expect "=============*" {send "y\\r"}
#expect eof
EOF
echo - Is there an invalid certificate to accept?
/Library/Application\\ Support/Fortinet/FortiClient/bin/epctrl -t accept
echo
exit 0- Jamf Heroes
- October 5, 2022
There is a issue with my script, because of the untrusted certificate. The answer, in this case, YES is not send. So i try to work around this and got some like this which seems to do the trick.
#!/bin/sh
## Add FortiClient configuration if EMS connection is broken
echo
echo - Are we connected to EMS?
/usr/bin/expect <<EOF
spawn /Library/Application\\ Support/Fortinet/FortiClient/bin/epctrl -r fqdn-or-ip-address
expect "=============*" {send "y\\r"}
#expect eof
EOF
echo - Is there an invalid certificate to accept?
/Library/Application\\ Support/Fortinet/FortiClient/bin/epctrl -t accept
echo
exit 0Did you use this to fix the below pop-up by chance when installing 7.0.7? We have all the other certs installed ahead of time, and that's worked FLAWLESSLY for us in 7.0.3, but now, as soon in our sandbox, using pretty much everything (we removed KEXT profiles RIP Catalina), we get this AFTER the app has installed. Even odder, as soon as you provide admin creds, it installs a cert from the EMS server. So we know whatever this is is new and fun and not the way 7.0.3 works. We even tried with our old profiles and still had the same results.
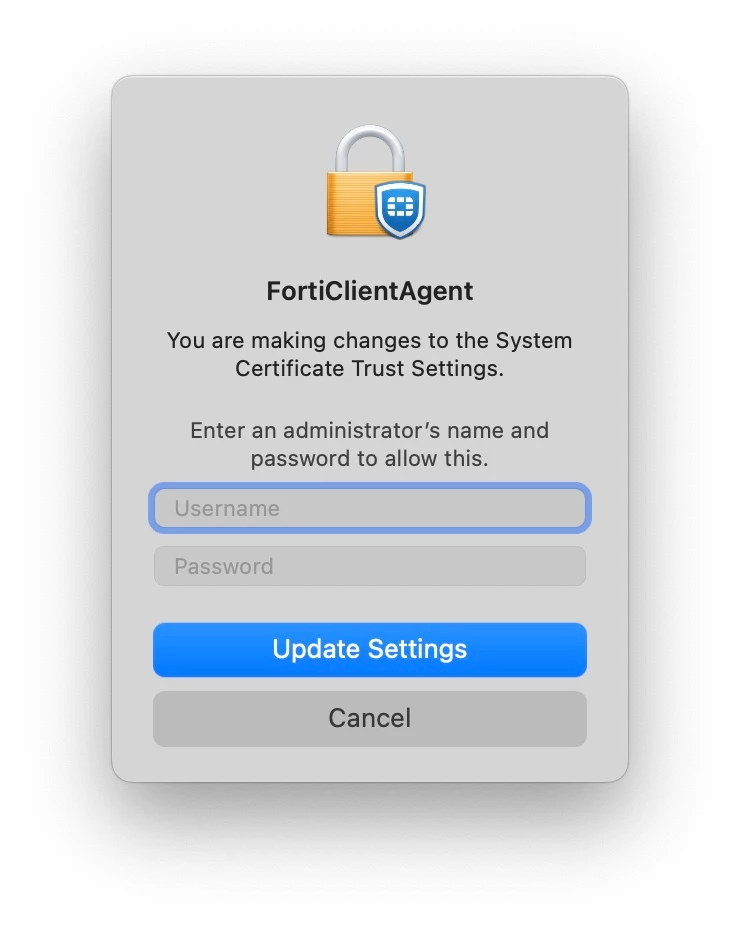
- New Contributor
- October 10, 2023
Did you use this to fix the below pop-up by chance when installing 7.0.7? We have all the other certs installed ahead of time, and that's worked FLAWLESSLY for us in 7.0.3, but now, as soon in our sandbox, using pretty much everything (we removed KEXT profiles RIP Catalina), we get this AFTER the app has installed. Even odder, as soon as you provide admin creds, it installs a cert from the EMS server. So we know whatever this is is new and fun and not the way 7.0.3 works. We even tried with our old profiles and still had the same results.

I know this is an older post, but we are seeing the same thing upgrading from v6 to v7 of FortiClient. We even added the certificate to a config profile and we still see this message. Did you ever find a solution?
- Valued Contributor
- October 10, 2023
I know this is an older post, but we are seeing the same thing upgrading from v6 to v7 of FortiClient. We even added the certificate to a config profile and we still see this message. Did you ever find a solution?
There where some changes in the config profiles... did you create a new profile?
https://docs.fortinet.com/document/forticlient/7.2.0/jamf-deployment-guide/776135/configuration-profiles
- Jamf Heroes
- October 11, 2023
There where some changes in the config profiles... did you create a new profile?
https://docs.fortinet.com/document/forticlient/7.2.0/jamf-deployment-guide/776135/configuration-profiles
@PablitoGordito we got the certs from our NetOps team as they were downloaded right from the EMS portal, and they've been working fantastic thus far.
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.
Scanning file for viruses.
Sorry, we're still checking this file's contents to make sure it's safe to download. Please try again in a few minutes.
OKThis file cannot be downloaded
Sorry, our virus scanner detected that this file isn't safe to download.
OK


