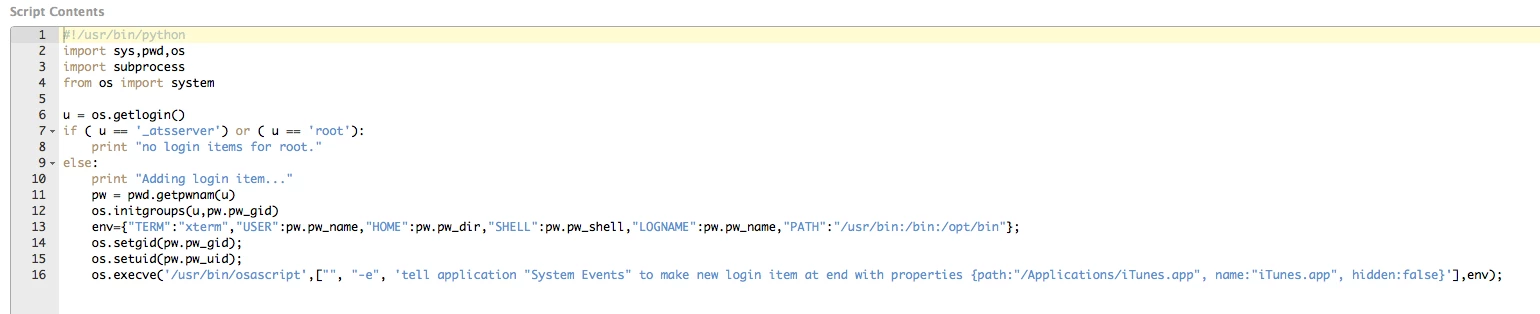
I'm attempting to run a script at login that adds a Login Item for the currently logged in user. I've seen some similar discussion in several places including here:
https://jamfnation.jamfsoftware.com/discussion.html?id=7555
However, when I attempt the same process it get the error message in the subject. Does anyone know of a solution to this or see what i'm doing wrong? Or is it just not possible. I'm testing on 10.10.3 btw.
Script:
#!/bin/sh
## Find currently logged in user
loggedInUser=`/bin/ls -l /dev/console | /usr/bin/awk '{ print $3 }'`
if [ "$3" == "root" ]; then
echo "JAMF Recorded User is: ($3)"
if [ "$loggedInUser"== "root" ]; then
echo "Logged in user is: ($loggedInUser). Exiting."
exit 2
fi
fi
## Add to Login Items
echo "Attempting to add CCAAgent.app to Login Items for $3 using 'su'"
su "$3" -c "osascript -e 'tell application "System Events" to make new login item at end with properties {path:"/Applications/CCAAgent.app", name:"CCAAgent.app", hidden:false}'"
echo "Done"
echo "Attempting to add CCAAgent.app to Login Items for $3 using 'bsexec'"
loggedInPID=$(ps -axj | awk "/^$3/ && /Dock.app/ {print $2;exit}")
launchctl bsexec "${loggedInPID}" sudo -iu "${3}" "osascript -e 'tell application "System Events" to make new login item at end with properties {path:"/Applications/CCAAgent.app", name:"CCAAgent.app", hidden:false}'"
echo "Done"Output:
Script result: Attempting to add CCAAgent.app to Login Items for MYID using 'su'
36:149: execution error: An error of type -10810 has occurred. (-10810)
Done
Attempting to add CCAAgent.app to Login Items for MYID using 'bsexec'
sudo: unknown user: MYID
Done