- Jamf Nation Community
- Products
- Jamf Pro
- Re: 802.1x not authenticating machine based to fre...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
802.1x not authenticating machine based to freeradius but windows laptops are fine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-28-2022 10:47 AM
Hey there,
I am trying to get the mac laptops to use certificate based logons for 802.1x. The machine can join to the AD domain, it can generate a certificate and i see that certificate on the machine. However when i try and apply a jamf profile to add the certificate and wireless profile to connect to the network i get the following errors:
mschap: FAILED: No NT/LM-Password. Cannot perform authentication
Login incorrect (eap: Failed continuing EAP TTLS (21) session. EAP sub-module failed): [MS\lmc02d<FULLHOSTNAMEREMOVED>
I have tried with PEAP as well as TTLS. On the windows laptops i have connecting using the same infrastructure, they connect fine and do not require any password. What is the point of certificate based logons that require a password? Makes no sense. But jamf / macs appear to need something there. Its very possible my jamf config is the problem here.
The domain root certificate is SHA-256, and is added to the same profile and trusted on the trust tab. I also put in the names of the radius server and the CA, and allowed trust exceptions.
I have tried all the different auth protocols and the error message changes, but the results are the same.
I have included the windows settings from group policy that do work without issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-28-2022 02:05 PM
I would suggest using an ADCS cert or SCEP certificate to do this. You can hop over to the 802.1X MacAdmins slack channel if you need more references.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-28-2022 02:06 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-30-2022 10:47 PM
Hello WifiChallenges,
You need to add Root CA in the profile and also add Trust to root CA in Network payload in the same configuration.
Hope this will help
profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-31-2022 08:27 AM
I have no idea about all that scep stuff and from that video i am certainly not going to install anything on my production CA, punch holes in the firewall, or modify external DNS.
i guess ill do preshared key for now. I dont know why it cant use my existing infrastructure. It gets a certificate from the CA fine, why cant it use it...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-31-2022 10:08 PM
Can you go to keychain access on a Mac device where this profile is installed correctly and check if you see your corporate WiFi identity preference ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-02-2022 12:35 AM
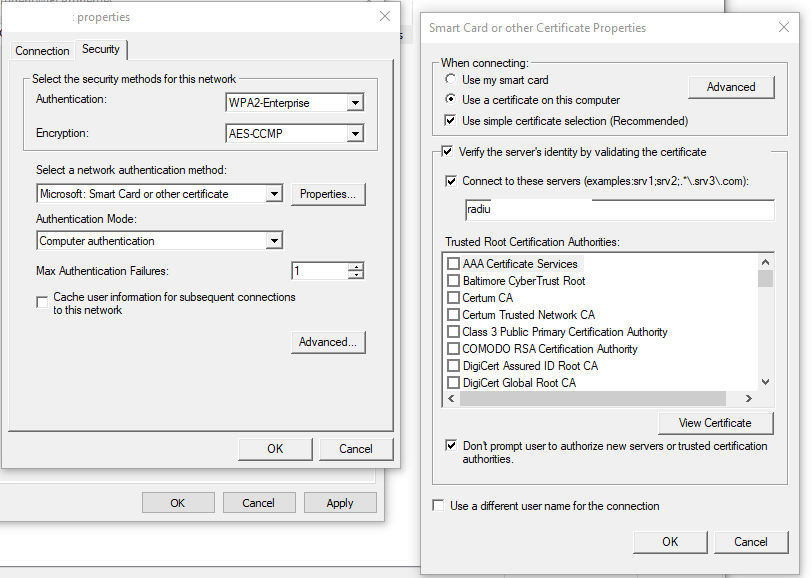
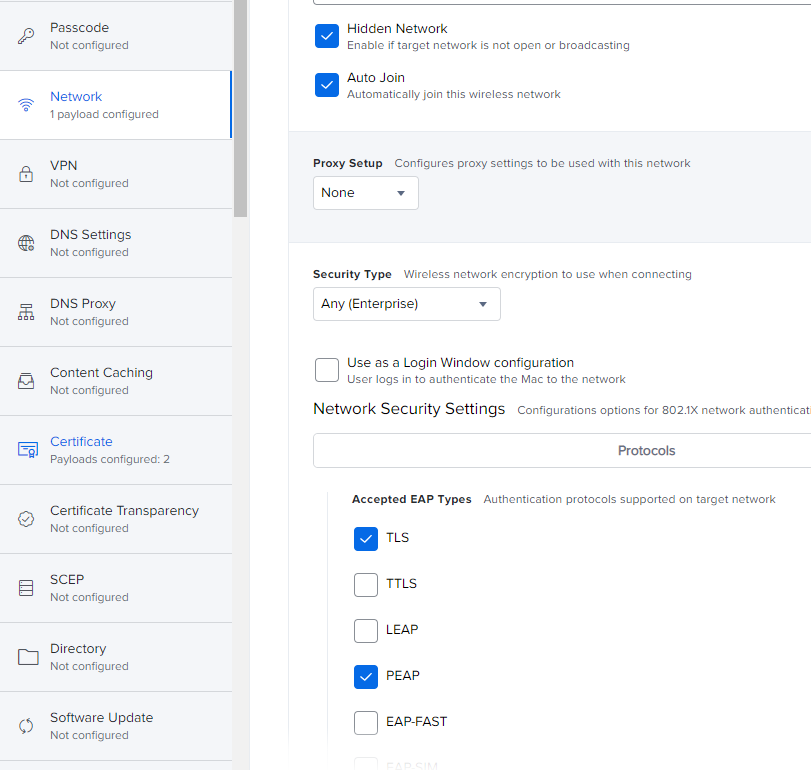
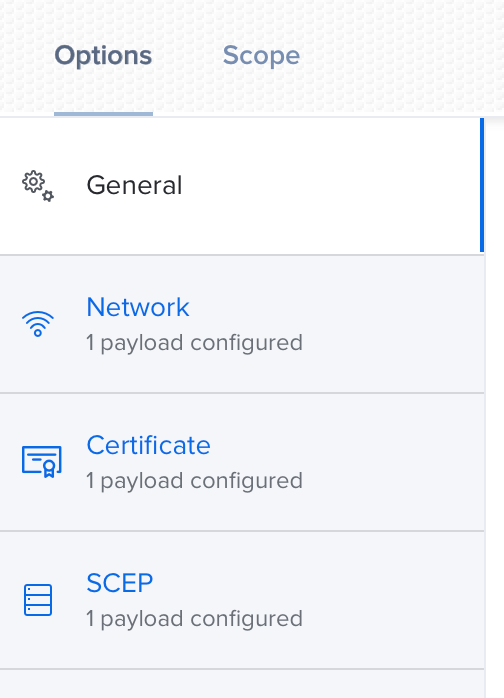
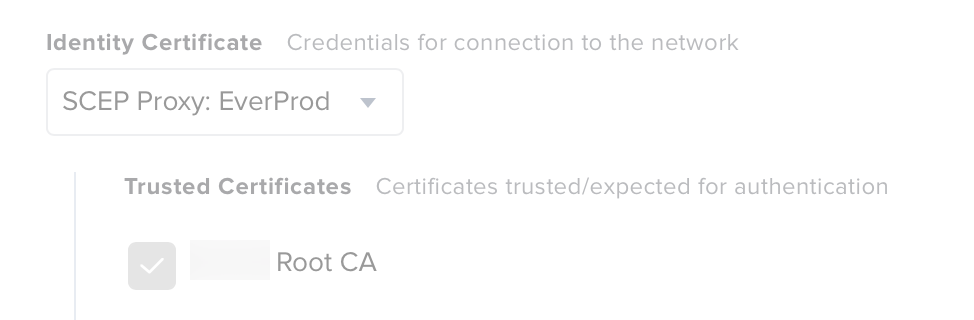
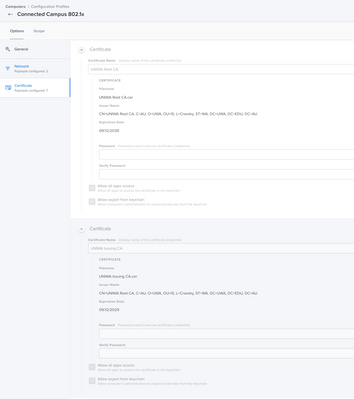
I have this working with a Configuration Profile that gets a cert via ADCS. There is a lot more in my profile than yours as I found separating it out into each part e.g. machine cert, root cert etc was a big fail. I didn't figure it all out myself - my friends in the Network Team helped big time telling me what the Radius server was objecting to as well as our Jamf Success Manager pointed me skillfully in the right direction.
Maybe these screen shots will help ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-02-2022 12:53 AM
You can anytime dm me on Jamf nation or Slack - Samstar777
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-04-2022 01:45 PM
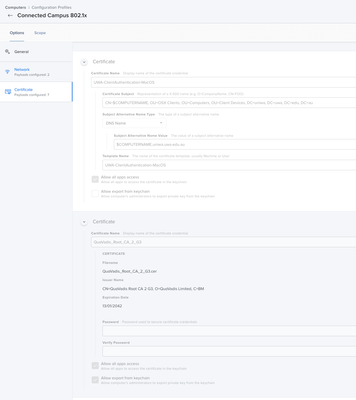
Thanks for those images. That is interesting how you have $COMPUTERNAME in there.... Do you have this AD CS connector installed in your environment?
As for slack, i dont have that, but thank you for the offer.
This is kind of a nice to have for me right now, i got the 22 macs i had to do this for out without the certificate and will have to work on this when i have free time. macs are a small part of our environment, so its not super critical to have working. I just realized though, that the problem may be because it does not seem to have a certificate on the machine. I believe the AD Certificate payload is what does that, so i have just configured that and will test it. I am also not in the office every day.
Will post back if i get it working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-17-2022 12:06 AM
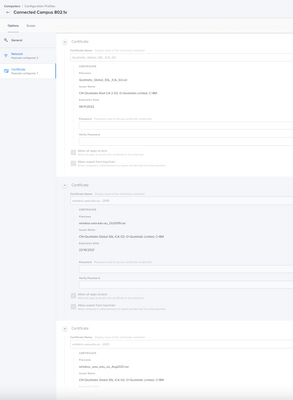
Hi @wifichallenges - Yes that's a working setup I showed you. $COMPUTERNAME gets replaced in the certificate with the machine name that is in scope. I found I needed all the certificates shown - even the wireless cert. This way there are no prompts about trusting certificates and the machine connects before anyone logs in. I needed the AD CA and AD ICA as well as for us the Quovadis CA and ICA certs. I know on Windows that is not needed but it was for the Mac's.
Yes we are using ADCS Connector to get the device certs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-12-2023 06:57 AM
Hi Everyone,
I solved the 802.1x problem. You can contact me here to find out how to solve the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-19-2023 10:24 AM
So i have progressed a bit. The certificate does work, and does connect. However my current problem is that you have to select the cert manually, with an admin credentials prompt, then it connects fine with the certificate. Not sure why it doesn't auto connect, but my radius server does not see the connect attempt even so its not even trying. I almost think it has to do with certificate trust, because even though i am pushing the ROOT CA cert to the machine, if i manually try and connect, it still does pop up a prompt to accept the certificate (even though all the trust settings say "trust" on them) . So why does it even prompt? i mean thats what it feels like is happening.
still researching a solution and found this post lol, so i thought i would update it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-12-2023 01:31 PM
Hi,
It asks for the certificate only once in my environment. Does it ask for a certificate every time in your environment?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-12-2023 02:18 PM
Not sure. i just didnt want it to prompt at all and feel like its broken if its asking the user at all. Means i would have to touch every machine, login, do a manual connect and tell it what certificate to use. Whether this transfers between users, and can be used at login, i do not know.
Anyways i got fed up a few weeks ago and am just using a username and password pair to connect for the laptops now. which of course works flawlessly first try, same as the ipads. F certificate based wireless on the mac... just not worth more days of my time. The older you get in this business, you have to know when to cut your losses and do the workaround instead of the ideal solution.