We are remotely deploying the Akamai Enterprise Threat Protector (ETP) agent on all of our staff Apple laptops with Jamf Pro.
The Akamai ETP platform prevents endpoints from resolving malicious domains based on their threat intelligence. The main Akamai ETP platform is a network-based tool. Akamai will provide you with a specific, unique IP address to route all of your DNS queries (or multiple in our case with two ISPs) and you will receive reporting info on blocked domains.
Domains are evaluated in the following categories: Malware, phishing and C&C
You are able to create custom block pages if your user browses directly to a blocked domain. Otherwise the query simply never resolves.
The platform also has some Acceptable Use Policy enforcement options to block adult content, gambling or other categories of websites, but we are mainly interested in blocking malware, phishing and C&C domains.
This ETP endpoint agent tool allows for added DNS security, specifically away from the organization's network when users are working remotely.
My plan was to silently install this tool on endpoints but I found that there are several things the user will notice.
Their documentation for remote installation is found here.
Here is how I did this within Jamf Pro:
- Within your Akamai portal go to Enterprise Threat Protector > Utilities > ETP client > Versions Management to find the latest release.
- Download the .pkg (I used 3.2.1)
- Create a .txt file with ONLY your specific entitlement code (provided by Akamai) and name it "bootstrap.txt"
- Place the .pkg and the .txt file in private/var/tmp
- Open Composer
- Pull the entire /tmp folder into composer
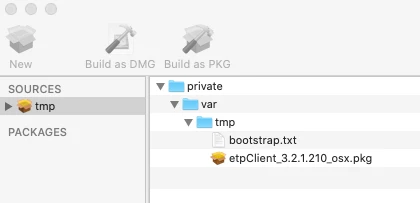
- Build as a pkg and rename it as you wish (I used "Install AkamaiETPInstallerWithCode.pkg")
- Open Jamf Admin
- Pull this pkg into Jamf Admin, add details as needed, save and replicate to other DPs as needed
- Go to Jamf Pro, create a new policy, scope as desired
- While editing the policy, go to "Files and Processes" and enter the following (your version may vary):
installer -pkg /private/var/tmp/etpClient_3.2.1.210_osx.pkg -target / - The ETP agent will install, the bootstrap.txt file will be deleted, and the agent will now show in three places on the computer:
/Applications/Enterprise Client Connector
 Menu Bar
Menu Bar
 Notification banner
Notification banner
These can be addressed however you wish. I emailed staff beforehand letting them know about the installation. This workflow did not interrupt any running programs or prompt a reboot.
Shortly after installation the endpoint will show up in your Akamai control center in Utilities > ETP Client as "Registered" and eventually as "Protected". You may also see "Authentication error" or "Other". Both of these are usually solved when the agent checks in next.
Any problems with the status of the agent, and documents for troubleshooting laptops that are not connecting correctly can be found here.

