- Jamf Nation Community
- Products
- Jamf Pro
- Re: ARD Screen Sharing issue M1 Macs and Monterey
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ARD Screen Sharing issue M1 Macs and Monterey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2022 12:25 AM
Hi All,
I’ve come across a strange issue stopping me rolling out M1 MacBook Pros to our users to replace older Intel machines.
I’m unable to use ARD to screen share onto an M1 Mac in these scenarios:
Filevault on and Firewall on
Filevault on and Firewall off
Works if Filevault is off and Firewall on or Filevault is on and Firewall is off.
I’ve tested a MacBook Pro 14inch and 16inch M1 running Monterey 12.0 through to 12.2 with the same result.
If I test an Intel Mac with the same Filevault/Firewall on, ARD works no problem.
Not sure if I’ve missed something daft on these M1 machines or a bug in Monterey on Apple silicon.
Cheers,
Robert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-10-2022 07:07 AM
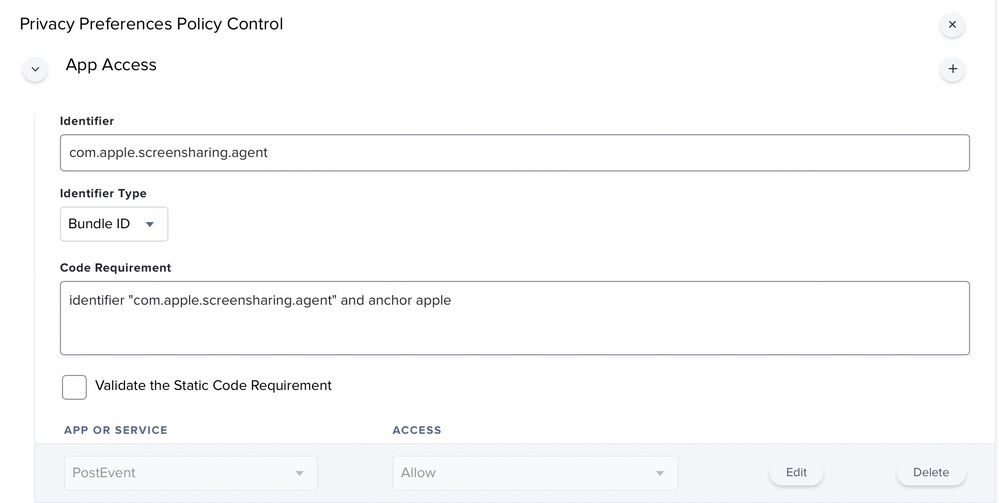
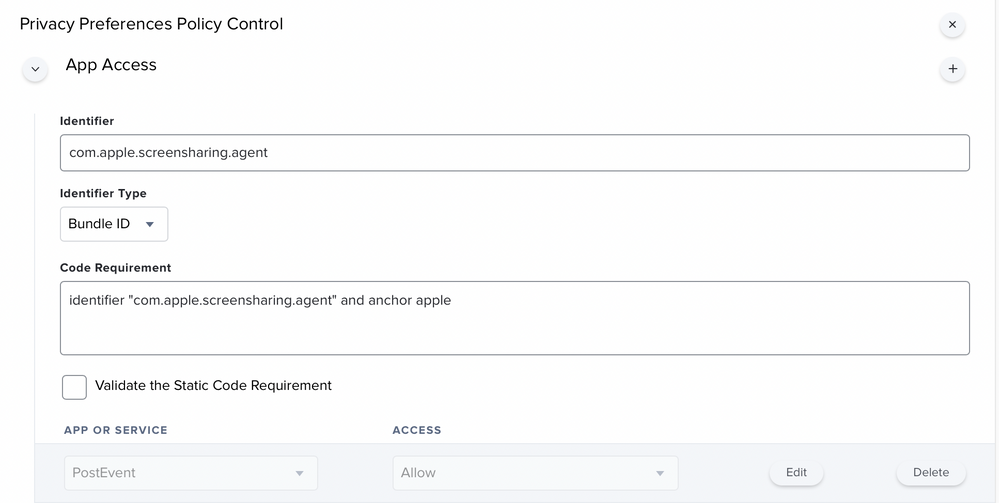
Thanks for the screenshot. I had missed the PPPC in these posts. Maybe that's what I'm missing. I never had to use it before. I'll give it a shot.
So how did the scrip look above?
So for specific users, should it look like this?
-users "USER1" "USER2"
Or without quotes?
-users USER1,USER2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2022 04:47 PM
12.4 definitely works, can use with or without the quotes. PPC is required to enable ARD so that would be it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2022 04:51 PM
In my fleet... Not a single computer on 12.4 is working. I get that strange error every time I try to screen share. M1 or Intel, laptop or iMac...makes no difference. If I go to an earlier OS, no problem. The upgrade (?) to 12.4 is breaking every computer.
@Bol , I did the testing you asked about below. No luck.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2022 04:52 PM
@kwoodard You beat me to it, i replied to your post!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2022 04:58 PM
@kwoodard While I was testing on the weekend i did notice something I had forgotten. Any computers below macos 11+ eg. 10.15, their sharing preference pane for remote management shows the correct radio buttons and users. It was definitely a cosmetic issue on macos 11+ that they only show all users and the people listed.
I have several mac mini's (intel & m1) on 12.4 and they are ok. Very strange!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2022 02:15 PM
Well, they did until 12.4… Now nothing on that version work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-28-2022 05:03 PM
On the off-chance that the eardm2 function proves helpful:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2022 06:03 PM
I’m running out of ideas, so I’m hoping I can figure out your script to make this work. I just did a quick check to see how many computers I can actually reach to a usable state…it’s about 60%.
Will your script work on older operating systems? I’m trying to get everything onto Monterey, but I have a ton of off site folks who just can’t figure out how to push a button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2022 02:52 PM
Anyone know where the settings for Remote Management reside? I think that on the computers where I am seeing this weird error in ARD, something in the remote computer is completely messed up and toggling the check-box for Remote Management isn't enough to clear out the issue. I would like to avoid reinstalling the OS if possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2022 03:56 PM
Somewhere on the computer besides in the Apple System Preferences / Sharing in Service column?
What's the weird ARD error?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 04:15 PM - edited 06-09-2022 04:16 PM
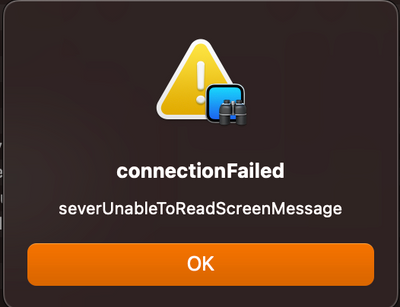
I get the following error when I try to connect via Apple Remote Desktop or the built in VNC… This occurs on both M1 and Intel machines.
connectionFailed
serverUnableToReadScreenMessage
I am looking for the actual (I assume) plist file that stores all this info on Remote Desktop settings. I think I have a bunch of computers where this file is somehow locked and I cannot reset it at all. My only recourse lately is to reinstall the OS...and even then, it hasn't always worked. In those cases, I have to do a wipe and install.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2022 05:53 PM
Yep. You'll either have to use the Management console for now or try @dan-snelson's solution listed above in his post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-10-2022 07:00 AM
~/Library/Containers/com.apple.RemoteDesktop/Data/Library/Preferences
Same error for me as well on Intel machines running Monterey. Prior to Monterey, my original script is just fine.
@rcole: Thanks for mentioning @dan-snelson's post. At a quick glance, it too looks promising. I'll have to give that a shot as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-10-2022 08:15 AM
That’s where the individual user preferences are. I’m looking for the system level presences are hiding. I appreciate the path though, I have 4 computers I regularly use and it would be nice to copy all my lists, groups, and scripts to the other machines.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2022 11:46 PM - edited 06-10-2022 11:47 PM
@HappyTrails @kwoodard
I went back and test, I believe only the PPPC profile was required for ARD. I couldn't find all the docs but from what I understand;
- Kickstart to setup privileges & users
- MDM / API to enable remote desktop
- Config profile to allow interaction of remote management via kickstart
Here's what I'm using in a policy triggered on startup, it will get applied soon after enrolment and can connect straight after. Please test before copy / pasting in your environment as I know there's some overkill elements to what I'm doing.
There was a lot of testing at the time and once it was all solid, i didn't get the chance to go back through and see what wasn't required. Also I removed the config profile and it did indeed break the workflow, so for me it was still a required step.
You can replace $4 / $5 with your own values, I enter these on the policy the script it added too.
#!/bin/bash
# B0L ARD Screen Share / Remote Desktop via Jamf Pro API
# - Added bearer token support as Classic API due for retirement
# - Added print of access group (to see who can ARD)
# - Removed hard code of Jamf Pro URL for plist preference
# - Overkill add Jamf Pro into groups / SSH / ScreenShare
# Note: -ShowObserve has no effect as of macOS 12.3
# https://ss64.com/osx/kickstart.html
error=0
jamfbin=$(/usr/bin/which jamf)
jamfpro_server_address=$(/usr/bin/defaults read /Library/Preferences/com.jamfsoftware.jamf jss_url); jamfpro_server_address=${jamfpro_server_address%%/}
encodedCredentials="$4"
localUserName="$5"
group=com.apple.access_screensharing
machineUUID=$(/usr/sbin/ioreg -rd1 -c IOPlatformExpertDevice | /usr/bin/awk '/IOPlatformUUID/ { gsub(/"/,"",$3); print $3; }')
kickstart="/System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart"
privs="-DeleteFiles -ControlObserve -TextMessages -OpenQuitApps -GenerateReports -RestartShutDown -SendFiles -ChangeSettings"
# Old one Liner
# $kickstart -activate -configure -access -on -users user -privs -all -clientopts -setmenuextra -menuextra no -restart -agent -menu
GenerateAuthToken () {
authToken=$( /usr/bin/curl "${jamfpro_server_address}/uapi/auth/tokens" \
--silent \
--request POST \
--header "Authorization: Basic $encodedCredentials" )
token=$( /usr/bin/awk -F \" '{ print $4 }' <<< "$authToken" | /usr/bin/xargs )
}
ExpireAuthToken () {
/usr/bin/curl "${jamfpro_server_address}/uapi/auth/invalidateToken" \
--silent \
--request POST \
--header "Authorization: Bearer $token"
}
GetJamfProComputerID () {
computerrecord=$( /usr/bin/curl --request GET \
--url "${jamfpro_server_address}/api/v1/computers-inventory?section=USER_AND_LOCATION&filter=udid%3D%3D%22${machineUUID}%22" \
--silent \
--header "Authorization: Bearer $token" )
computerID=$( /usr/bin/osascript -l 'JavaScript' -e "JSON.parse(\`$computerrecord\`).results[0].id" )
}
SetJamfProConfig () {
/usr/sbin/dseditgroup -o edit -a "$localUserName" -t user admin
/usr/sbin/dseditgroup -o edit -a "$localUserName" -t user com.apple.access_ssh
/usr/sbin/dseditgroup -o edit -a "$localUserName" -t user com.apple.access_screensharing
/usr/sbin/systemsetup -f -setremotelogin on
$jamfbin startSSH
}
SetAppleRemoteDesktopViaAPI () {
/usr/bin/curl --request POST \
--url "${jamfpro_server_address}/JSSResource/computercommands/command/EnableRemoteDesktop/id/$computerID" \
--silent \
--header "Authorization: Bearer $token"
}
SetAppleRemoteDesktopViaKickstart () {
# https://support.apple.com/en-au/HT201710
/usr/bin/defaults write /Library/Preferences/com.apple.RemoteManagement allowInsecureDH -bool TRUE
$kickstart -targetdisk / -verbose -uninstall -settings -prefs
$kickstart -targetdisk / -verbose -configure -allowAccessFor -specifiedUsers
$kickstart -targetdisk / -activate -configure -access -on -users $localUserName -privs $privs -clientopts -setmenuextra -menuextra no -setwbem -wbem yes -restart -agent -console -menu
}
GetGroupMembership () {
echo "Screen sharing ACL members:";
for i in $(dscl . list /users); do [[ $(id -nG "$i" | grep $group) ]] && echo "$i"". "; done
# $kickstart -computerinfo -1 "$text"
}
GenerateAuthToken
GetJamfProComputerID
SetAppleRemoteDesktopViaAPI
SetJamfProConfig
SetAppleRemoteDesktopViaKickstart
GetGroupMembership
ExpireAuthToken
exit $error
ps. How do we format code script for bash!?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2022 09:52 AM - edited 06-14-2022 09:54 AM
@Bol I think I have done something wrong... When I use your code, modifying it for my needs, when I attempt to screen share with a remote machine using this script, I get a pop-up window that states that "Authentication failed to (computer name)"... Here is the output from when I run the script... When I am connecting to the remote computer, I am using one of the user/pass combo's that is showing up in the Screen Sharing ACL list.
Checking for policies triggered by "recurring check-in" for user "(my ID)"...
Executing Policy DEP - Enable Remote Management All
Running script ARC-RemoteManagment-Enable_All...
Script exit code: 0
Script result: execution error: Error: TypeError: undefined is not an object (evaluating 'JSON.parse(`{
"httpStatus" : 401,
"errors" : [ ]
}`).results[0]') (-2700)
<html>
<head>
<title>Status page</title>
</head>
<body style="font-family: sans-serif;">
<p style="font-size: 1.2em;font-weight: bold;margin: 1em 0px;">Unauthorized</p>
<p>The request requires user authentication</p>
<p>You can get technical details <a href="http://www.w3.org/Protocols/rfc2616/rfc2616-sec10.html#sec10.4.2">here</a>.<br>
Please continue your visit at our <a href="/">home page</a>.
</p>
</body>
</html>setremotelogin: remote login is already On.
/Library/Application Support/JAMF/tmp/ARC-RemoteManagment-Enable_All: line 51: startSSH: command not found
Starting...
Stopped ARD Agent.
Removed ARD System Preferences.
Removed ARD Agent Preferences.
Removed Remote Management System Preferences.
Removed remote control privileges for all users.
Done.
Starting...
Setting allow all users to YES.
Done.
Starting...
Activated Remote Management.
Stopped ARD Agent.
basicadminuser: Set user remote control privileges.
basicadminuser: Set user remote access.
basicuser: Set user remote control privileges.
basicuser: Set user remote access.
jamf: Set user remote control privileges.
jamf: Set user remote access.
micro: Set user remote control privileges.
micro: Set user remote access.
Set the client options.
Started ARD Admin.
Restarted Menu Extra (System UI Server).
Done.
Screen sharing ACL members:
basicadminuser.
jamf.
micro.
root.
{
"httpStatus" : 401,
"errors" : [ ]
}
@
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2022 06:48 PM - edited 06-14-2022 06:48 PM
@kwoodard It looks like it's gone wrong during the api remote desktop command which makes sense you are seeing that error when connecting.
Double check two things;
- Encoded credentials : Make sure they are a mix of your api username and password by running this in terminal (enter your own user pass)
printf "user:pass" | iconv -t ISO-8859-1 | base64 -i -
dXNlcjpwYXNz
- Check the api user privileges is ticked: Settings - System Settings - Jamf Pro User Accounts & Groups - User - Privileges - Jamf Pro Server Actions -
Send Computer Remote Desktop CommandOnce we sort those two out I think it will start working for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-15-2022 10:41 AM
I am getting an output that looks similar to the output your example generated. I also have the API user privileges set as shown (everything is checked in fact for the user).
I manually went into Remote Management and looked at the options...nothing is being set, so I think there is a discontinuity somewhere in the script beyond that http error...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-15-2022 05:52 PM
Ok well this is where we step through line by line, either the copied syntax will be wrong from what I posted or we will quickly find where things have gone wrong in the setup.
Start with copy pasting in your known values for;
encodedCredentials="somethingsoemthing!"
localUserName="username"
jamfpro_server_address="https://soemthing:8443"
machineUUID="findmeinjamfpro"
Then you can paste in the commands to be print on the screen to check their output. Once we know they are ok, re-run that command to store them inside the variable.
eg.
/usr/bin/curl "${jamfpro_server_address}/uapi/auth/tokens" \
--silent \
--request POST \
--header "Authorization: Basic $encodedCredentials"
authToken=$( /usr/bin/curl "${jamfpro_server_address}/uapi/auth/tokens" \
--silent \
--request POST \
--header "Authorization: Basic $encodedCredentials" )
/usr/bin/awk -F \" '{ print $4 }' <<< "$authToken" | /usr/bin/xargstoken=$( /usr/bin/awk -F \" '{ print $4 }' <<< "$authToken" | /usr/bin/xargs )
/usr/bin/curl --request GET \
--url "${jamfpro_server_address}/api/v1/computers-inventory?section=USER_AND_LOCATION&filter=udid%3D%3D%22${machineUUID}%22" \
--silent \
--header "Authorization: Bearer $token"
computerrecord=$( /usr/bin/curl --request GET \
--url "${jamfpro_server_address}/api/v1/computers-inventory?section=USER_AND_LOCATION&filter=udid%3D%3D%22${machineUUID}%22" \
--silent \
--header "Authorization: Bearer $token" )
/usr/bin/osascript -l 'JavaScript' -e "JSON.parse(\`$computerrecord\`).results[0].id"computerID=$( /usr/bin/osascript -l 'JavaScript' -e "JSON.parse(\`$computerrecord\`).results[0].id" )
And then test the big boss;
/usr/bin/curl --request POST \
--url "${jamfpro_server_address}/JSSResource/computercommands/command/EnableRemoteDesktop/id/$computerID" \
--silent \
--header "Authorization: Bearer $token"
Let us know what you find.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-16-2022 08:56 AM
I will try to give this a go today. I will report back with my findings. Thank you for your help!
As an aside, I did a new setup yesterday, leaving out the Remote Management command. I got everything setup and manually checked the boxes for RM. Once I updated the computer to 12.4 from 11.6...RM doesn't work again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-16-2022 02:41 PM
Wanted to expand on my previous observation... I just provisioned a brand new computer, straight out of the box. Had some flavor of Big Sur on it. Did a full provisioning and setup (no Remote Management) then updated to Monterey 12.4 using the built in updater. Once finished, manually enabled Remote Management by checking the box, then checking all the options. Restarted the computer... When I tried to connect to the new machine (M1 MBP 13") I am getting the error I have seen a lot and listed above. Seems something is amiss here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-16-2022 05:05 PM
Wait a second, I’m confused.
If you are leaving out the remote management command in the script, are you then using the ‘enable remote desktop’ button in Jamf for this computer record?
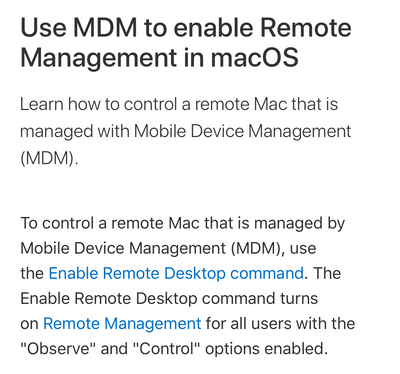
If the device is enrolled in MDM, then it must have enable Remote Desktop enabled via MDM also to work. (Either script : api or Jamf)
https://support.apple.com/en-us/HT209161
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-16-2022 05:10 PM
Usually I am doing the remote management command when provisioning a computer. Since I’m doing 80 this week and next, I’m trying out a few things as I go. Today, I disabled the remote management command in Jamf and wanted to see the behavior of manually enabling it. On 12.4, I get the same error across the board. M1/Intel… Jamf enabled or manually enabled… I get the same error when trying to connect to any computer on 12.4 from multiple other computers running ARD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-16-2022 05:14 PM
If you're certain everything else is correct then all i can offer more if reboot. I find after sending the command either by script or Jamf, it takes a restart before I can then connect without authentication error.
Also I'm using Apple remote desktop so if any machine is being stubborn, I delete the record out first. Then add the creds again, run an admin report to confirm all the privileges are ok, lastly reconnect and control screen.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-16-2022 05:15 PM
Also, what happens if you enroll and solely use the script to automate the permissions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2022 05:20 PM - edited 06-16-2022 05:21 PM
I will give that a try and report back. I am going to grab a second laptop that I have that also has this issue and bring it along with me as I setup these new Mac's. Work on it while provisioning... It's so frustrating.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-17-2022 08:52 AM
I wasn't able to do line-by-line, but I ran your script exactly as written and this is the results I got... The account I am trying to connect with is micro.
Script result: execution error: Error: TypeError: undefined is not an object (evaluating 'JSON.parse(`{
"httpStatus" : 401,
"errors" : [ ]
}`).results[0]') (-2700)
<html>
<head>
<title>Status page</title>
</head>
<body style="font-family: sans-serif;">
<p style="font-size: 1.2em;font-weight: bold;margin: 1em 0px;">Unauthorized</p>
<p>The request requires user authentication</p>
<p>You can get technical details <a href="http://www.w3.org/Protocols/rfc2616/rfc2616-sec10.html#sec10.4.2">here</a>.<br>
Please continue your visit at our <a href="/">home page</a>.
</p>
</body>
</html>setremotelogin: remote login is already On.
Starting...
Stopped ARD Agent.
Removed ARD System Preferences.
Removed ARD Agent Preferences.
Removed Remote Management System Preferences.
Removed remote control privileges for all users.
Done.
Starting...
Setting allow all users to NO.
Done.
Starting...
Activated Remote Management.
Stopped ARD Agent.
micro: Set user remote control privileges.
micro: Set user remote access.
Set the client options.
Done.
Screen sharing ACL members:
basicadminuser.
jamf.
micro.
root.
{
"httpStatus" : 401,
"errors" : [ ]
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-17-2022 09:05 AM
It looks like it's failing when passing the computer id number from Jamf;
computerID=$( /usr/bin/osascript -l 'JavaScript' -e "JSON.parse(\`$computerrecord\`).results[0].id" )
Navigate to the device record in Jamf and grab it's Computer ID number. eg. 824
Then add this to the variable and see if the line by line test successfully works after. We can sort the why out later if it's what I think it is.
eg.
computerID="824"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2022 08:36 AM
I got the same error when adding in the comuterID manually.
Here is the complete code I am using. It should mirror yours, with the line about computerID changed (I commented the original out).
#!/bin/bash
# B0L ARD Screen Share / Remote Desktop via Jamf Pro API
# - Added bearer token support as Classic API due for retirement
# - Added print of access group (to see who can ARD)
# - Removed hard code of Jamf Pro URL for plist preference
# - Overkill add Jamf Pro into groups / SSH / ScreenShare
# Note: -ShowObserve has no effect as of macOS 12.3
# https://ss64.com/osx/kickstart.html
error=0
jamfbin=$(/usr/bin/which jamf)
jamfpro_server_address=$(/usr/bin/defaults read /Library/Preferences/com.jamfsoftware.jamf jss_url); jamfpro_server_address=${jamfpro_server_address%%/}
localUserName="$4"
encodedCredentials="$5"
group=com.apple.access_screensharing
machineUUID=$(/usr/sbin/ioreg -rd1 -c IOPlatformExpertDevice | /usr/bin/awk '/IOPlatformUUID/ { gsub(/"/,"",$3); print $3; }')
kickstart="/System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart"
privs="-DeleteFiles -ControlObserve -TextMessages -OpenQuitApps -GenerateReports -RestartShutDown -SendFiles -ChangeSettings"
# Old one Liner
# $kickstart -activate -configure -access -on -users user -privs -all -clientopts -setmenuextra -menuextra no -restart -agent -menu
GenerateAuthToken () {
authToken=$( /usr/bin/curl "${jamfpro_server_address}/uapi/auth/tokens" \
--silent \
--request POST \
--header "Authorization: Basic $encodedCredentials" )
token=$( /usr/bin/awk -F \" '{ print $4 }' <<< "$authToken" | /usr/bin/xargs )
}
ExpireAuthToken () {
/usr/bin/curl "${jamfpro_server_address}/uapi/auth/invalidateToken" \
--silent \
--request POST \
--header "Authorization: Bearer $token"
}
GetJamfProComputerID () {
computerrecord=$( /usr/bin/curl --request GET \
--url "${jamfpro_server_address}/api/v1/computers-inventory?section=USER_AND_LOCATION&filter=udid%3D%3D%22${machineUUID}%22" \
--silent \
--header "Authorization: Bearer $token" )
#computerID=$( /usr/bin/osascript -l 'JavaScript' -e "JSON.parse(\`$computerrecord\`).results[0].id" )
computerID="1063"
}
SetJamfProConfig () {
/usr/sbin/dseditgroup -o edit -a "$localUserName" -t user admin
/usr/sbin/dseditgroup -o edit -a "$localUserName" -t user com.apple.access_ssh
/usr/sbin/dseditgroup -o edit -a "$localUserName" -t user com.apple.access_screensharing
/usr/sbin/systemsetup -f -setremotelogin on
$jamfbin startSSH
}
SetAppleRemoteDesktopViaAPI () {
/usr/bin/curl --request POST \
--url "${jamfpro_server_address}/JSSResource/computercommands/command/EnableRemoteDesktop/id/$computerID" \
--silent \
--header "Authorization: Bearer $token"
}
SetAppleRemoteDesktopViaKickstart () {
# https://support.apple.com/en-au/HT201710
/usr/bin/defaults write /Library/Preferences/com.apple.RemoteManagement allowInsecureDH -bool TRUE
$kickstart -targetdisk / -verbose -uninstall -settings -prefs
$kickstart -targetdisk / -verbose -configure -allowAccessFor -specifiedUsers
$kickstart -targetdisk / -activate -configure -access -on -users $localUserName -privs $privs -clientopts -setmenuextra -menuextra no -setwbem -wbem yes -restart -agent -console -menu
}
GetGroupMembership () {
echo "Screen sharing ACL members:";
for i in $(dscl . list /users); do [[ $(id -nG "$i" | grep $group) ]] && echo "$i"". "; done
# $kickstart -computerinfo -1 "$text"
}
GenerateAuthToken
GetJamfProComputerID
SetAppleRemoteDesktopViaAPI
SetJamfProConfig
SetAppleRemoteDesktopViaKickstart
GetGroupMembership
ExpireAuthToken
exit $error- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2022 04:51 PM
Ok well that's everything I have done to get my fleet working.
If I was in your situation, I would be starting from scratch;
- Enroll a new machine and exclude all profiles / restrictions apart from these two;
Also if you are using ARD to connect from your machine, remove any reference or saved computer from ARD before trying to connect again.
As of right now, I am able to use ARD or the screen sharing app to connect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-22-2022 08:48 AM
@Bol You are an absolute legend! Thank you for spending so much time and effort providing us with your workflows and information. Leveraging the plist to generate the jamf pro server address is a stroke of genius.
I am VERY new to JAMF administration, I apologize in advance for any dumb questions. I am having trouble wrapping my head around your script and where to plug-in my org's variables.
I want to implement 1 local user to be able to use remote management through ARD (we'll call it ARDuser).
And we have a JAMF specific api user (we'll call it APIuser) to be able to make calls to the API. I am having trouble figuring out where to plug this in as well.
is
encodedCredentials="$4"
Where you put in the API user? If so, where does the password go? I know the classic API's plain text passwords are getting phased-out, but how does the API-user authenticate to the JAMF Pro API without inputting the password somewhere? Something about this concept is not clicking for me with the bearer tokens/ auth tokens.
and is
localUserName="$5"
The user who will have ARD access to the remote computers?
We could probably have a teach piece for our helpdesk to walk through the enabling ARD through the JAMF commands, but it would be nice if we could get it going during the enrollment process.
Thank you again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 01:08 AM - edited 06-23-2022 01:12 AM
Thank you very much for mentioning that, it's much appreciated.
Firstly, I have only borrowed the genius thoughts of some of the other community brains
eg. Jamf Pro Server Address via Plist is thanks to the Der Flounder blog. Again, many thanks!
You seem to have a good grasp on what is happening with the api calls in Jamf and really, if you take out the move to bearer tokens, you can get away with a single line command to turn on remote access for all users (using your api username as an example)
/usr/bin/curl -s -u ARDuser:$apiPass https://yourmdm.com:8443/JSSResource/computercommands/command/E...
Perhaps try that command first and ensure it;
1. Enables remote access and you see this become enabled in the computer object in Jamf
2. Proves your api account has the correct access to then move on using bearer token as opposed to the classic api calls.
You should be able to set who and what privileges have access to remote management via the kickstart command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-23-2022 04:36 PM
So it does look like my API user is good to go! Using the above script in your reply enabled ARD for all users on my test Bench when I manually specified the Computer ID#.
When I try to incorporate all of my variables into your monster of a script, I keep getting JSON parse error. I think it's having trouble pulling the computer ID to drop in the call to the API. I'm going to keep playing with it, but maybe you had some tips?
Again, thank you for being so helpful to us JAMF Newbz.
Output from Jamf Pro:
Executing Policy testing ARD issue with black screen
Running script Restart ARD services Test...
Script exit code: 0
Script result: execution error: Error: SyntaxError: JSON Parse error:
Unexpected EOF (-2700)
setremotelogin: remote login is already On.
Starting...
Removed ARD Agent Preferences.
Removed Remote Management System Preferences.
Removed remote control privileges for all users.
Done.
Starting...
Setting allow all users to NO.
Done.
Starting...
[31mScreen recording might be disabled. Screen Sharing or
Remote Management must be enabled from System Preferences
or via MDM.
[0m[31mScreen control might be disabled. Screen Sharing or
Remote Management must be enabled from System Preferences
or via MDM.
[OmActivated Remote Management.
Stopped ARD Agent.
hadmin: Set user remote control privileges.
hadmin: Set user remote access.
Set the client options.
Restarted Menu Extra (System UI Server).
Done.
Screen sharing ACL members:
hadmin.
root.
teacher.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-23-2022 04:45 PM
I have that same issue. I recently switched over to Jamf Cloud and noticed (while working with a Jamf engineer) that there can be lag. In a few of my scripts, I had to incorporate some sleep commands in the script to allow AWS to catch up. I wonder if that needs to happen here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 05:47 PM - edited 06-23-2022 05:53 PM
Sorry, that's my bad. I forgot using the older api you can easily find the id of the computer by adding in the serial;
serial=$(/usr/sbin/ioreg -rd1 -c IOPlatformExpertDevice | /usr/bin/awk -F'"' '/IOPlatformSerialNumber/{print $4}')Then api call for the computer ID;
computerID=$(/usr/bin/curl -u "$apiuser":"$apipass" "$jssurl":8443/JSSResource/computers/serialnumber/"$serial" -H "accept: text/xml" | /usr/bin/xpath "/computer[1]/general/id/text()")
You don't have to use the monster script, in the beginning, I only had the kickstart one liner then I added the api ard call. That was it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-23-2022 05:50 PM
You can then remove the line you have commented out, plus the one where you declare the id underneath it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-27-2022 09:53 AM
Oh man, I think I (we, really) am so close. Something about the xpath part of the computer ID line is not working properly to isolate the computer ID#.
I did a bit of testing with echoing the variables because I wasn't getting the script to work all together.
If I echo the computerID variable without the xpath part of the line, it just dumps the entire contents of the XML file into the terminal. I get an error once the xpath command is put back in.
With this script:
#!/bin/bash
apiuser=myValue
apipass=myValue
jssurl=https://myValue
serial=$(/usr/sbin/ioreg -rd1 -c IOPlatformExpertDevice | /usr/bin/awk -F'"' '/IOPlatformSerialNumber/{print $4}')
computerID=$(/usr/bin/curl -u $apiuser:$apipass $jssurl:8443/JSSResource/computers/serialnumber/$serial -H "accept: text/xml")
echo $computerID
It spits out the entire contents of that XML page in the terminal.
When i put back in the xpath I get this:
#!/bin/bash
apiuser=myValue
apipass=myValue
jssurl=https://myValue
serial=$(/usr/sbin/ioreg -rd1 -c IOPlatformExpertDevice | /usr/bin/awk -F'"' '/IOPlatformSerialNumber/{print $4}')
computerID=$(/usr/bin/curl -u $apiuser:$apipass $jssurl:8443/JSSResource/computers/serialnumber/$serial -H "accept: text/xml" | /usr/bin/xpath "/computer/general/id/text()")
echo $computerID
terminal error/output:
Executing Policy testing ARD issue with black screen
Running script Restart ARD services Test...
Script exit code: 0
Script result:
% Total
% Received % Xferd Average Speed
Time
Time
Time Current
Dload Upload
Total
Spent
Left Speed
0
0
0
0
0 --:--:--
/usr/bin/xpath5.30 [options] -e query [-e query...] [filename...]
OUsage:
If no filenames are given, supply XML on STDIN. You must provide at
least one query. Each supplementary query is done in order, the
previous query giving the context of the next one.
Options:
-q quiet, only output the resulting PATH.
-S suffix, use suffix instead of linefeed.
-p postfix, use prefix instead of nothing.
-n Don't use an external DTD.
100 15900
0 15900
0
0
118k
0
--:--:-- --:--:--
126 k
curl: (23) Failure writing output to destination
I can see the ID number in the XML file through the terminal and if it's accessed through the browser as well, but it won't seem to isolate that ID value through the command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-27-2022 06:12 PM
@kbreed27 Oh man, so close! Try adding the following option to xpath as below, I've just test with the same variable names you have used and it works.
computerID=$(/usr/bin/curl -u $apiuser:$apipass $jssurl/JSSResource/computers/serialnumber/$serial -H "accept: text/xml" | /usr/bin/xpath -e "/computer/general/id/text()")
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-28-2022 08:24 AM
@Bol Huzzah! That was it. If you are ever in the DFW area I owe you a coffee, man.
Just as a follow-up. Since my script doesn't include the encoded credentials or the bearer token stuff, am I basically staring down this policy going by the way-side once they deprecate the classic API? I think I read that is slated for any time from August to the end of the year.
And I guess is there no way to leverage the Serial number with the Auth/Bearer Tokens?
For reference to anyone, this is my script working in my environment:
#!/bin/bash
apiuser=yourJamfApiUser
apipass=yourJamfAPIPass
jssurl=https://yourJamfUrl.com
kickstart="/System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart"
localUserName=yourLocalAdminName
privs="-DeleteFiles -ControlObserve -TextMessages -OpenQuitApps -GenerateReports -RestartShutDown -SendFiles -ChangeSettings"
serial=$(/usr/sbin/ioreg -rd1 -c IOPlatformExpertDevice | /usr/bin/awk -F'"' '/IOPlatformSerialNumber/{print $4}')
computerID=$(/usr/bin/curl -u $apiuser:$apipass $jssurl:8443/JSSResource/computers/serialnumber/$serial -H "accept: text/xml" | /usr/bin/xpath -e "/computer/general/id/text()")
/usr/bin/curl -s -u $apiuser:$apipass $jssurl:8443/JSSResource/computercommands/command/EnableRemoteDesktop/id/$computerID -X POST
/usr/bin/defaults write /Library/Preferences/com.apple.RemoteManagement allowInsecureDH -bool TRUE
$kickstart -targetdisk / -verbose -uninstall -settings -prefs
$kickstart -targetdisk / -verbose -configure -allowAccessFor -specifiedUsers
$kickstart -targetdisk / -activate -configure -access -on -users $localUserName -privs $privs -clientopts -setmenuextra -menuextra no -setwbem -wbem yes -restart -agent -console -menu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-28-2022 08:45 AM
@kbreed27 Nice one!!!
I wish mate, I'm down under right now but hey, that's my first coffee kudo so I appreciate that :D
Not sure of the cut off date but it's optional now keeping classic going. Check here for all the commands and whats possible plus I think the new api isn't yet matching all the previously available commands from what I understand..
https://developer.jamf.com/jamf-pro/reference/jamf-pro-api
This is great reading also from Mr Purves, getting a handle on the newer token setup
https://richard-purves.com/2021/12/09/jamf-pro-api-for-fun-and-profit/