Hi,
I'm having an issue with JDS where by it will not copy new packages across all JDS DPs.
I have tried lots of things:
- checked connectivity between JSS and the JDS
- checked connectivity between master JDS and a child JDS
- checked DNS wasn't an issue
- Ran inventory on each JDS
- Restarted the JDS instances
- Changing master distribution point and uploading to that.
- Restarted tomcat service for jss incase there was anything on that side.
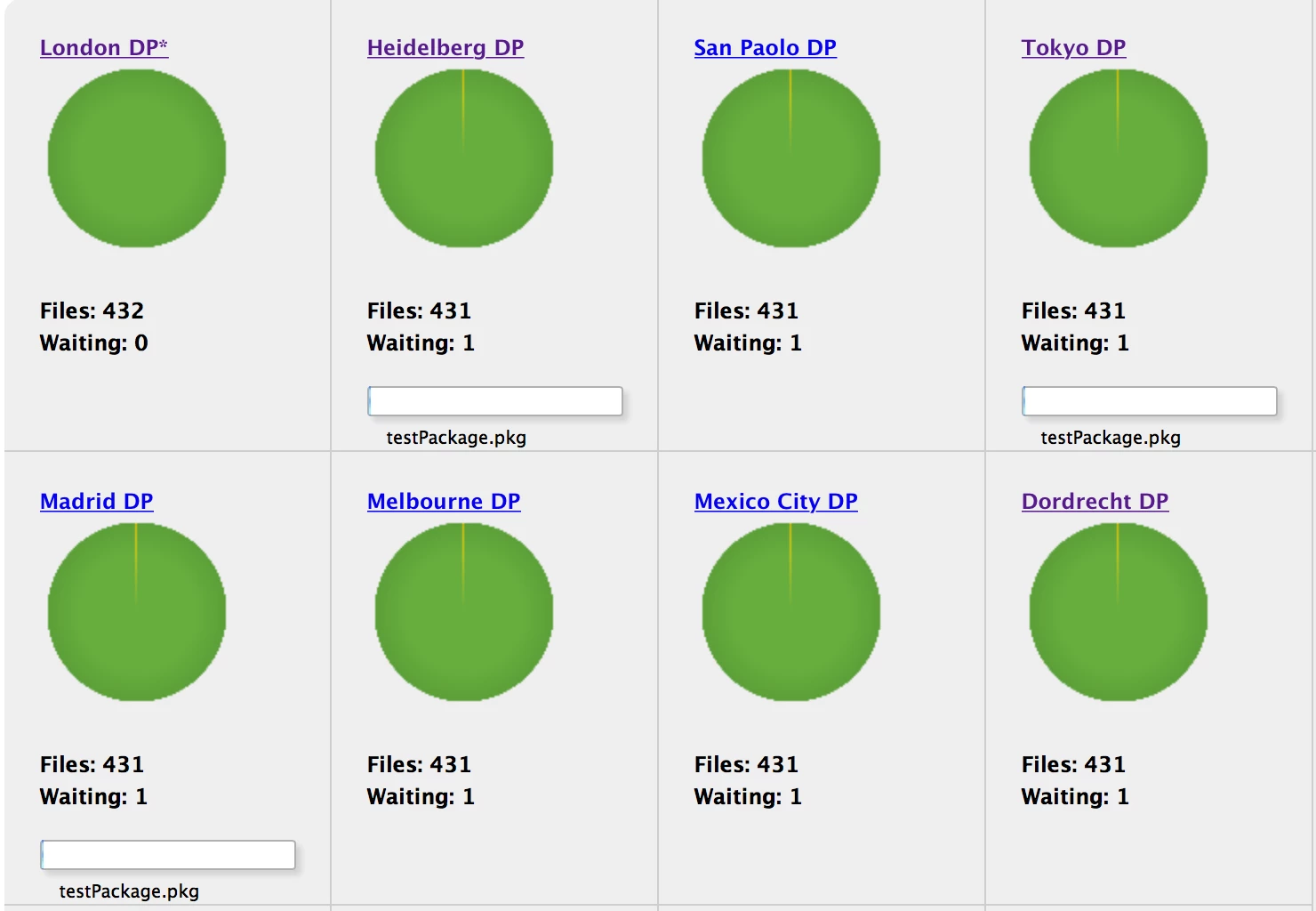
I can see that existing packages are replicating fine because i have a test jds server that i can use to select specific packages, which works. The problem is uploading new packages.
See the screenshot of the JDS dashboard. The package is visible to the servers but not is happening.
Please help!