- Jamf Nation Community
- Products
- Jamf Pro
- Concerns about Jamf Pro Azure AD Connector Permiss...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Concerns about Jamf Pro Azure AD Connector Permissions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2021 11:58 AM
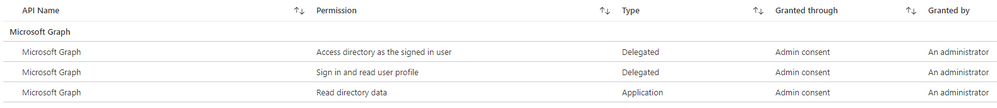
We recently began looking into configuring Azure AD as the Cloud Identity Provider for our Jamf Pro environment. The setup went smoothly in our dev environment and we've successfully been able to read user and group information, but we have some concerns because we noticed that the Jamf Pro Azure AD Connector application has a delegated permission to Microsoft Graph to access our Azure AD "as the signed in user", in addition to the expected "Read user profile" and "Read directory data" permissions. My understanding is that Jamf only ever needs to read data from Azure, why is this permission needed, which would theoretically allow Jamf to make changes to our Azure environment?