Hi everyone,
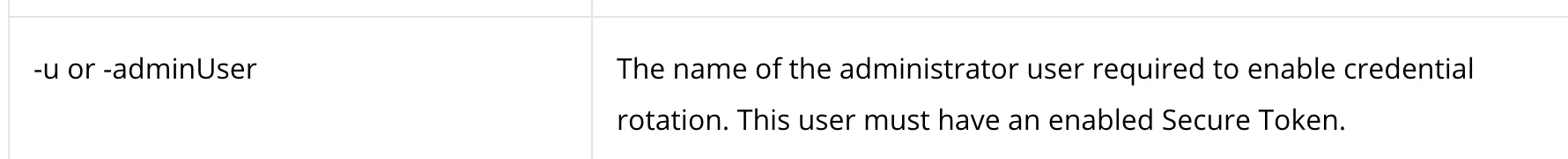
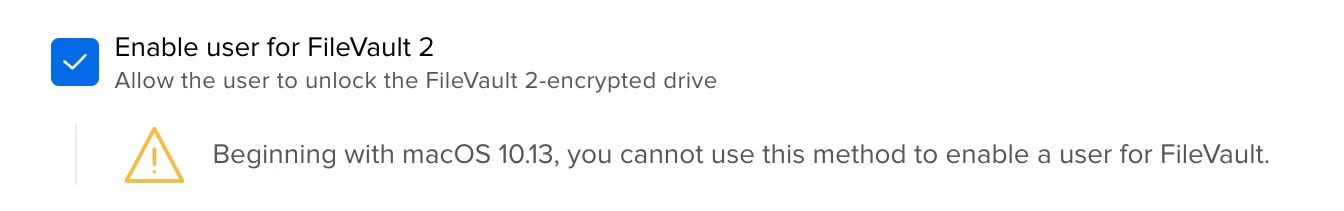
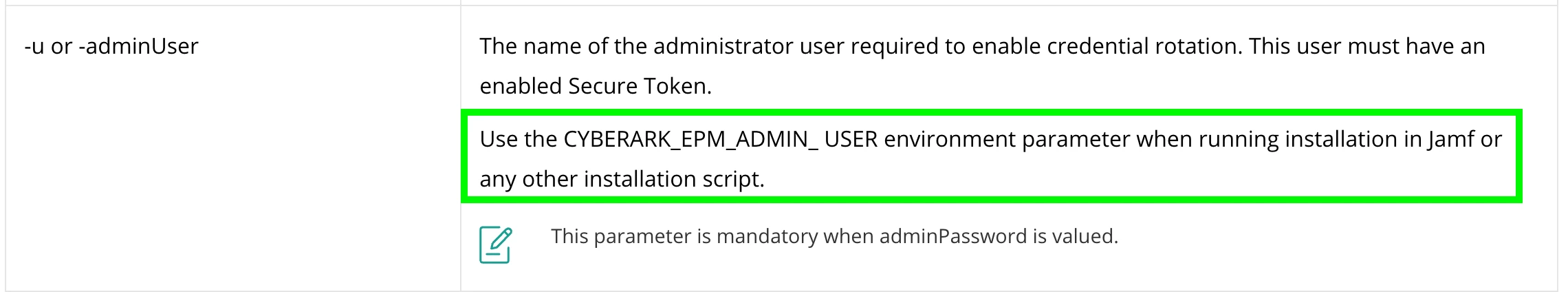
I've set up a test PreStage Enrollment, where a local admin account is created. In addition to that account, the local user account that gets created during the Setup Assistant, is a standard account (we don't allow our users to be admins). Our FileVault 2 configuration profile is set to be enabled at login, which works fine for the standard user. The first time this user logs out and logs back in, the FV2 is enabled. However, that leaves the admin user, which is still not FV2 enabled. How can we remotely enable FV2 for this user, without the end user having access to the admin user's credentials and logging into that account, just to enable FV2?
Thanks!