Hi Jamf Nation,
we are using conditional access policies in EntraID to prevent users from using private mobile devices to access our M365 Services.
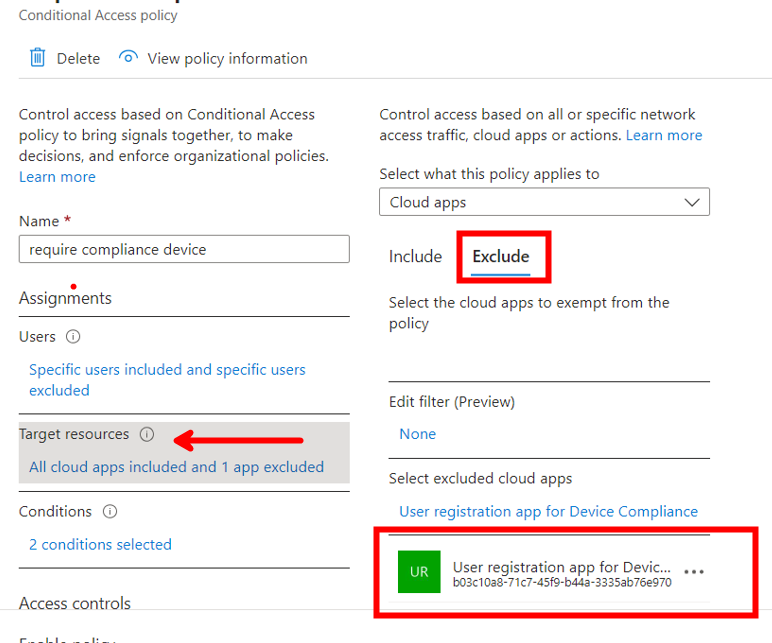
However I need to Exclude Microsoft Authenticator App from this Policy but im not able to select this app in CA Policy Config.
I tried to use a filter for a device condition "device.mdmAppId -eq "4813382a-8fa7-425e-ab75-3b753aab3abb""
But i guess this attribute is not available to EntraID since Devices are not Intune but Jamf managed.
In the Device Sign In Log im able to see the block based on the Application ID for Microsoft Authenticator.
Do any of you have any ideas on how to do this?