- Jamf Nation Community
- Products
- Jamf Pro
- Re: File Vault 2: No Longer Enabling on Catalina
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
File Vault 2: No Longer Enabling on Catalina
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-14-2019 09:42 AM
We currently have a configuration profile that enables the FV2 & Redirects the Key back to JAMF servers.
However now while testing with Catalina among all the is officially broken the FV2 seems to be in a loop. When I restart the machine I get the typical "To add this user to FileVault, enter the password for $jamfuser" following adding the PW it proceeds with this new message now instead of producing a KEY like normal.
"Enabling FileVault on your volume.
The Initial set-up may take a few minutes. The FileVault recovery key will be displayed when FileVault is ready. This may show up after this user logs out."
It then loops everytime I restart the machine never really Enabling FV2.
Anyone else encountering this as well?
UPDATE: More on this issue here: Catalina - FileVault Enablement
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 03:49 AM
@JarvisUno Yes we had the same issue starting with macOS 10.15, seems to be broken when enabling FV at logout. Have a look at this topic: https://www.jamf.com/jamf-nation/discussions/33538/catalina-filevault-enablement
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 06:22 AM
@jordy.witteman So is the only solution right now is to Enable it upon login instead of log out?
Is this something that JAMF or Apple needs to fix?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 06:58 AM
@JarvisUno I believe Apple needs to fix it because I created a custom FV config profile (signed) only with the required keys and could reproduce easily. The easiest fix seems to use a policy 'At next login' combined with a config profile to require FV and to escrow the recovery key.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 07:00 AM
@jordy.witteman This would be that custom script you posted on your thread correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 07:28 AM
@JarvisUno Yes if you only want to use a config profile without any policies that one should work if you paste that in the PayloadContent of the mobileconfig file. For now I use the following successfully without having to use the custom config profile:
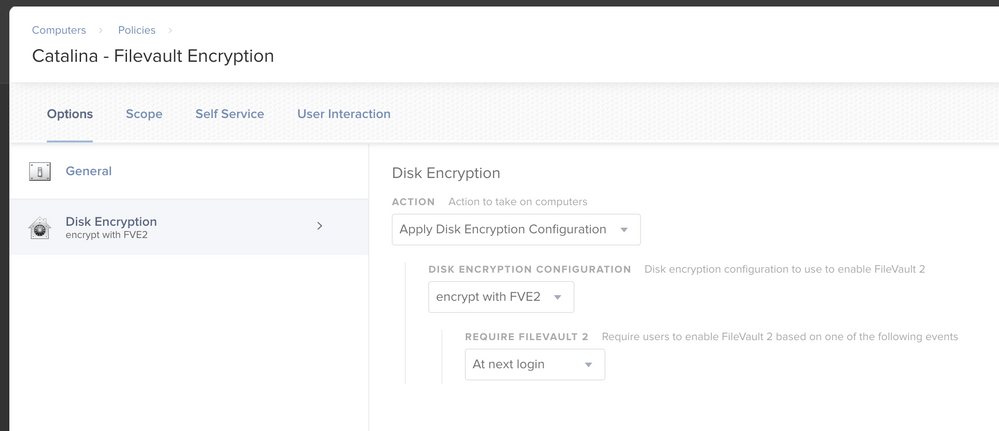
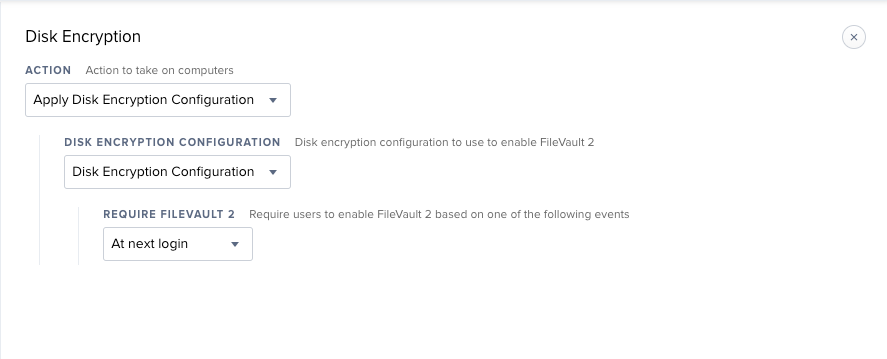
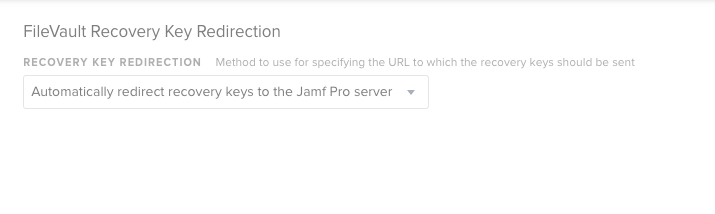
Config Profile --> Security & Privacy: Require FileVault 2 + Escrow Recovery Key
Policy with Disk Encryption: At Next Login
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2019 01:41 PM
i have that setup too except no "require filevault 2"
its set to current or next user
however, it just loops and loops and by random chance it would do the encryption.
no idea why.
manual intervention allows it though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2019 01:54 PM
@jcheLC I just started to notice this as well, this was working fine up until a couple of days ago and it just so happens that I wiped my test machine and am seeing this now. I have wiped it x3 times since then and FV2 has only enabled x1 of those times.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2019 03:27 PM
@JarvisUno do you have a workaround or whats your worklflow now?
it randomly enables for us for us, not sure why, its like after 4-5 reboots/retries.
i can do it manually, but that defeats the purposed of automation :(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2019 07:02 AM
@jcheLC I do not I have started to discover what I can do as of right now I do not have a game plan. Zero Touch for Mac's is a "Lie"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2019 07:19 AM
there are other threads about this: https://www.jamf.com/jamf-nation/discussions/33538/title#responseChild195408 but basically the Filevault doesn't enable at logout, but it works at login. My quick solution was to set up this policy and scoped to Catalina computers. there is an extra reboot involved in our provisioning process but it works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2019 08:01 AM
The closest I've got to "Zero Touch" on Jamf Pro 10.13.1 is using MDS (no ardunio, so a few touches to get to recovery, launch terminal, run command), which auto logs in a temp local admin and uses preloaded jamfhelper to prompt to trigger enrollment using the profiles binary (3 clicks).
After enrollment reboot the user first run script manually prompts for user (Mobile Admin) password using jamfhelper/osascript
Use sysadminctl to grant a secure token to user (necessary in 10.15, not 10.14 in my testing)
Use fdesetup to enable FV (Catalina requires user clicking accept to allowing fdesetup, on the to-do list to fix)
Use sysadminctl to disable secure token for temp admin
Use "diskutil apfs updatePreboot /" to remove temp admin from FV login screen
Delete temp admin
Was sort of surprised it worked with Catalina. Interested to test out bootstrap tokens in Jamf Pro 10.18.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2019 08:02 AM
@strayer That is current policy I have setup it was working just fine it's now looping and I restart it multiple times but it never turns on FV2.
It's very frustrating because I thought I was passed this issue already and well here I am again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2019 08:15 AM
same as you @JarvisUno
literally same setup with next login, only thing i notice that we have different vs everyone else so far is that they . have "require fv2" checked in your second to last picture.
no zero touch here, what i do is manually go in and enable FV.
good thing is, at least it knows where the JAMF server is and shoots the key there vs originally asking for iCloud....which was very unnerving.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-05-2020 01:12 PM
Still stuck with this garbage @peaudunk Can you post the actual commands you are using on a manual basis as I am going to have to do the same thing till there is a better solution out there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-06-2020 08:36 AM
@JarvisUno This is the FV section of my user Mobile Account first run script for 10.15.3.
It starts with an Erase+Install package that sets up ladmin to autologin and trigger DEP enrollment via Jamf Helper, which binds the machine+misc, never enabling FV for ladmin, but it has a secure token.
Config Profile escrows key, once FV is enabled and inventory update, CP gets updated to require FV.
Hopefully getting to test bootstrap in the next couple months.
#!/bin/sh
##variables
#logged in user
USER=$(/usr/bin/python -c 'from SystemConfiguration import SCDynamicStoreCopyConsoleUser; import sys; username = (SCDynamicStoreCopyConsoleUser(None, None, None) or [None])[0]; username = [username,""][username in [u"loginwindow", None, u""]]; sys.stdout.write(username + "
");')
#jamf helper location
JAMFHELPER="/Library/Application Support/JAMF/bin/jamfHelper.app/Contents/MacOS/jamfHelper"
FIRSTMSG="Welcome to Mac@Company!\n\nYou will now be asked to input you password to encrypt the system with FileVault."
FIRSTMSGFORMATTED=$( echo $FIRSTMSG )
MSG="FileVault has been successfully configured.\n\nPress OK to continue setup.\n\nWhen the Self Service app loads the user interactive portion of enrollment is complete."
FINALMSG=$( echo "$MSG" )
#FileVault Status
FVSTATUS="$(/usr/bin/fdesetup status)"
#FileVault Status Check
if [ "$FVSTATUS" != "FileVault is On." ]; then
#branded jamfhelper window to inform end user about FileVault process
"$JAMFHELPER" -windowType utility -title "Mac@Comapny" -description "$FIRSTMSGFORMATTED" -button1 "Okay" -icon /path/to/brandingimage.png
#get passwords
PASSWORD="$(/usr/bin/osascript -e 'Tell current application to display dialog "Please enter your password:" default answer "" with title "FileVault Setup" with text buttons {"Ok"} default button 1 with hidden answer' -e 'text returned of result')"
PASSCHECK=`dscl /Local/Default authonly $USER $PASSWORD; echo $?`
#autheticate password
while [[ "$PASSCHECK" != "0" ]]; do
echo "asking again"
PASSWORD2="$(/usr/bin/osascript -e 'Tell current application to display dialog "Incorrect password, please try again:" default answer "" with title "FileVault Setup" with text buttons {"Ok"} default button 1 with hidden answer' -e 'text returned of result')"
PASSWORD=$PASSWORD2
PASSCHECK=`dscl /Local/Default authonly $USER $PASSWORD2; echo $?`
done
#grant secure token
sysadminctl -adminUser ladmin -adminPassword ladminpw -secureTokenOn $USER -password "${PASSWORD}"
#enable FileVault
/usr/bin/fdesetup enable -inputplist << EOF
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Username</key>
<string>$USER</string>
<key>Password</key>
<string>$PASSWORD</string>
</dict>
</plist>
EOF
#branded jamfhelper window to inform end user about process completion
"$JAMFHELPER" -windowType utility -title "FileVault Setup Complete" -description "$FINALMSG" -button1 "OK" -icon /path/to/brandingimage.png
#remove secure token from ladmin
sysadminctl -secureTokenOff ladmin -password ladminpw -adminUser $USER -adminPassword "${PASSWORD}"
#remove ladmin from filevault login screen
diskutil apfs updatePreboot /
fi- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-06-2020 01:14 PM
@peaudunk This looks interesting I am kind of a visual learner mind sharing your workflow and how you have it all setup so I can test this on my end?
But I like what I see here.