- Jamf Nation Community
- Products
- Jamf Pro
- Re: FortiClient 6.4.x Web Content Filter
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-28-2021 01:12 PM
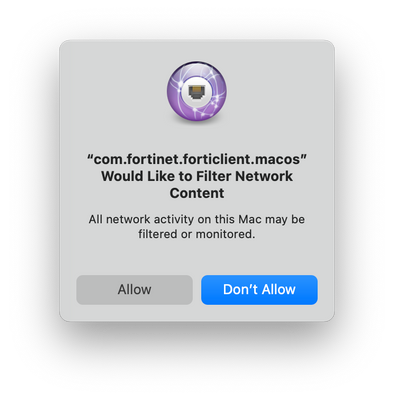
Currently in the process of deploying FortiClient 6.4.x to macOS devices, however after installing FortiClient 6.4.x, users are seeing a prompt to allow "com.fortinet.forticlient.macos" to filter network content.
Does anybody know how to create a configuration profile for the delivery of a payload which adds the web content filter for FortiClient, pre-allowing it and thus avoiding the users being prompted?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 05:47 AM
Thanks @jonlju for the suggestions... Googling for over a week didn't really help & Fortinet support was pretty useless when reached out to them. But through persistence combined with trial and error I have now found that implementing the following settings as part of a configuration profile does the trick for macOS:
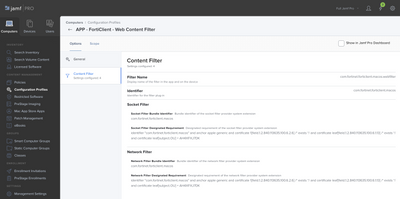
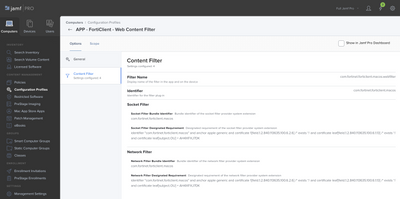
OPTIONS > CONTENT FILTER
FILTER NAME = com.fortinet.forticlient.macos.webfilter
IDENTIFIER = com.fortinet.forticlient.macos
SOCKET FILTER BUNDLE IDENTIFIER = com.fortinet.forticlient.macos
SOCKET FILTER DESIGNATED REQUIREMENT = identifier "com.fortinet.forticlient.macos" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = AH4XFXJ7DK
NETWORK FILTER BUNDLE IDENTIFIER = com.fortinet.forticlient.macos
NETWORK FILTER DESIGNATED REQUIREMENT = identifier "com.fortinet.forticlient.macos" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = AH4XFXJ7DK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 06:06 AM
Thanks for the suggestions. I had been Googling for over a week with no success and found Fortinet support to be useless when reached out to them. But through continued persistence combined with trail and error I've eventually manage to put together a solution that works. Implementing a configuration profile as follows has done the trick:
OPTIONS > CONTENT FILTER
FILTER NAME = com.fortinet.forticlient.macos.webfilter
IDENTIFIER = com.fortinet.forticlient.macos
SOCKET FILTER BUNDLE IDENTIFIER = com.fortinet.forticlient.macos
SOCKET FILTER DESIGNATED REQUIREMENT = identifier "com.fortinet.forticlient.macos" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = AH4XFXJ7DK
NETWORK FILTER BUNDLE IDENTIFIER = com.fortinet.forticlient.macos
NETWORK FILTER DESIGNATED REQUIREMENT = identifier "com.fortinet.forticlient.macos" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = AH4XFXJ7DK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 06:11 AM
Thanks for the suggestions. I had been Googling for over a week with no success and found Fortinet support to be useless when reached out to them. But through continued persistence combined with trail and error I've eventually manage to put together a solution that works. Implementing a configuration profile as follows has done the trick:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 12:13 AM
We have the same issue but for Sophos, I've followed their configuration guide but I'm unable to pre-approve the "filter network content" pop-up...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 03:48 AM
You need to create a content filter with the identifier & network filter bundle (you might need the socket filter set too), and it need to be deployed on the machine before the software is installed. Like jonlju, i use one for sophos, in my case it doesnt prompt in my case, but it also does not seem to work correctly either. Other filters work fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2021 04:48 AM - edited 07-29-2021 11:41 PM
Thanks @SCCM, I never realized and I've now added that to our configuration profile as well.
To @dan_ashley, maybe it would help reaching out to Fortinet to see if they have a guide for setting up the content filter configuration profile? I tried googling myself but can only find iOS guides.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 05:47 AM
Thanks @jonlju for the suggestions... Googling for over a week didn't really help & Fortinet support was pretty useless when reached out to them. But through persistence combined with trial and error I have now found that implementing the following settings as part of a configuration profile does the trick for macOS:
OPTIONS > CONTENT FILTER
FILTER NAME = com.fortinet.forticlient.macos.webfilter
IDENTIFIER = com.fortinet.forticlient.macos
SOCKET FILTER BUNDLE IDENTIFIER = com.fortinet.forticlient.macos
SOCKET FILTER DESIGNATED REQUIREMENT = identifier "com.fortinet.forticlient.macos" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = AH4XFXJ7DK
NETWORK FILTER BUNDLE IDENTIFIER = com.fortinet.forticlient.macos
NETWORK FILTER DESIGNATED REQUIREMENT = identifier "com.fortinet.forticlient.macos" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = AH4XFXJ7DK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2021 12:48 AM
Hi @dan_ashley
I have a similar requirement for one of the application. I am not able understand the "Filter Name" part. Is it somewhere which we can find out, or is it just a value we give for our reference ? If we can find it out , how do we do it ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 06:06 AM
Thanks for the suggestions. I had been Googling for over a week with no success and found Fortinet support to be useless when reached out to them. But through continued persistence combined with trail and error I've eventually manage to put together a solution that works. Implementing a configuration profile as follows has done the trick:
OPTIONS > CONTENT FILTER
FILTER NAME = com.fortinet.forticlient.macos.webfilter
IDENTIFIER = com.fortinet.forticlient.macos
SOCKET FILTER BUNDLE IDENTIFIER = com.fortinet.forticlient.macos
SOCKET FILTER DESIGNATED REQUIREMENT = identifier "com.fortinet.forticlient.macos" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = AH4XFXJ7DK
NETWORK FILTER BUNDLE IDENTIFIER = com.fortinet.forticlient.macos
NETWORK FILTER DESIGNATED REQUIREMENT = identifier "com.fortinet.forticlient.macos" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = AH4XFXJ7DK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 06:11 AM
Thanks for the suggestions. I had been Googling for over a week with no success and found Fortinet support to be useless when reached out to them. But through continued persistence combined with trail and error I've eventually manage to put together a solution that works. Implementing a configuration profile as follows has done the trick:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 06:53 AM
How did you find the correct Filter Designation Requirements? I'm facing similar issues with a different application.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 07:16 AM
I used the PPPC Utility to get the info for the FortiClient app to give me the Filter Designation Requirements, then swapped the identifier to that which was being presented in the popup macOS was presenting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-29-2021 07:18 AM
Perfect, this will help me a lot, thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-24-2021 12:09 PM
Does anyone know if this changed in FortiClient 7.0.1?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-02-2021 04:44 PM
Anyone else having issues with this when upgrading from a previous version of Forti (in my case 6.4.3) to 6.4.6? It doesn't seem to use the network filter after upgrading.