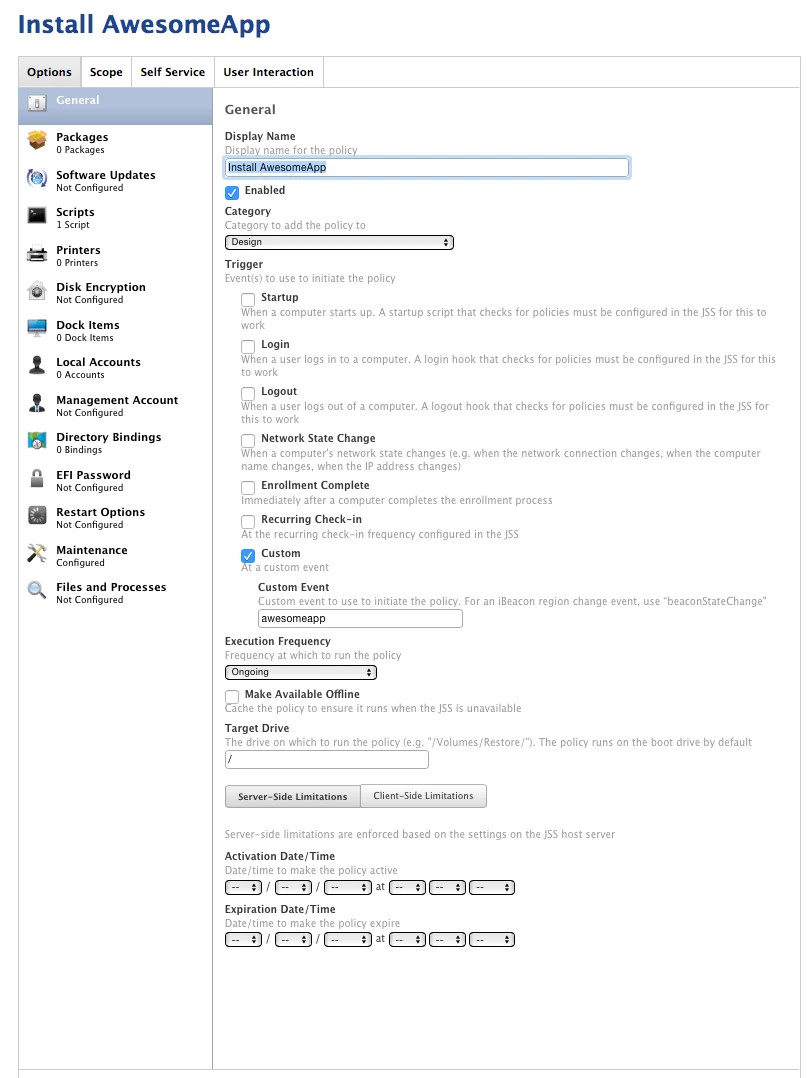
I have a problem with Self Service policies scoped to all computers, but limited to certain LDAP groups / users, with no other triggers except the Custom trigger. Self Service is enabled for these policies.
When I initiate a policy via Self Service, the little window displays "Gathering Information..." for a few seconds, then the progress bar rapidly fills up and the message disappears. The policy says it "Succeeded," but nothing actually happened. In /var/log/jamf.log, it says "Checking for policy ID 12345..." and nothing else.
So I start debugging on the command line:
If I run jamf policy -event awesomeapp then it says "No policies were found for the "awesomeapp" trigger." (Update: thank you @PeterClarke for the correction. This is my mistake.)
If I run jamf policy -trigger awesomeapp then the policy runs and completes as expected.
If I run jamf policy -id 12345 then the policy runs and completes as expected.
wtf...?
Configuration Summary:
- JSS 9.81
- One computer has 10.10.5, the other has 10.11.3
- Both Macs are bound to AD
- Both Macs have AD users logged in
- Self Service is set to "No Login."
- Policies scoped to LDAP user / group appear as expected in Self Service.
- Self Service displays the username set in "User & Location" in the JSS Computer record.
- Actual logged in Mac user makes no difference; Self Service still displays the "assigned" username.
So far I have tried / verified:
- removing the JAMF Framework and re-enrolling the machines;
- Unbinding and rebinding the Macs with AD;
- Rebooting the Macs;
- Resetting the policy scope to computer-based (it works);
- The casper service account in AD is valid and not locked;
- The local management account is valid and has the right password;
What could I be missing? Any other suggestions of things to try?