@LibertyJSS
If you could share your Directory Authentication Profile that would be great. I can't seem to get this working and would like to compare
tia
Larry
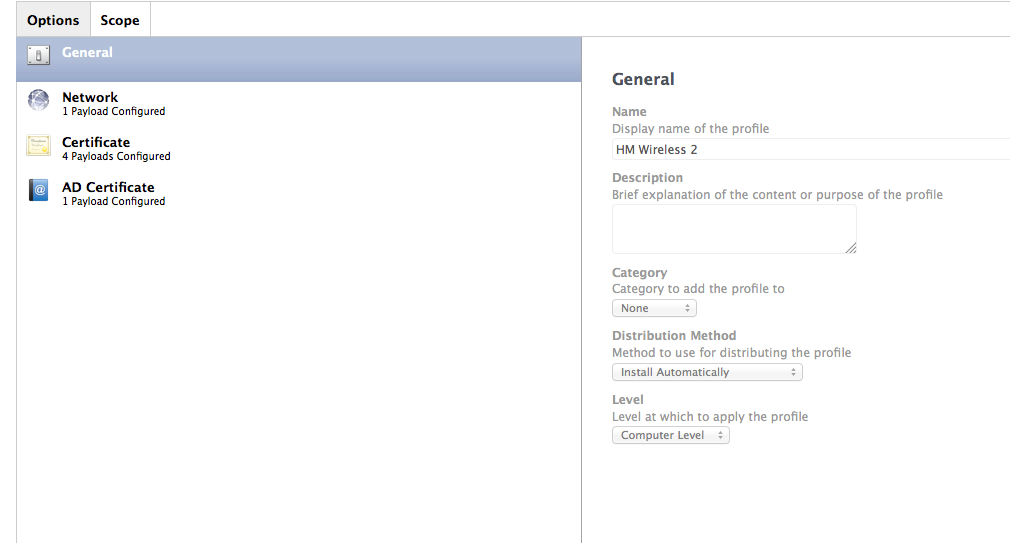
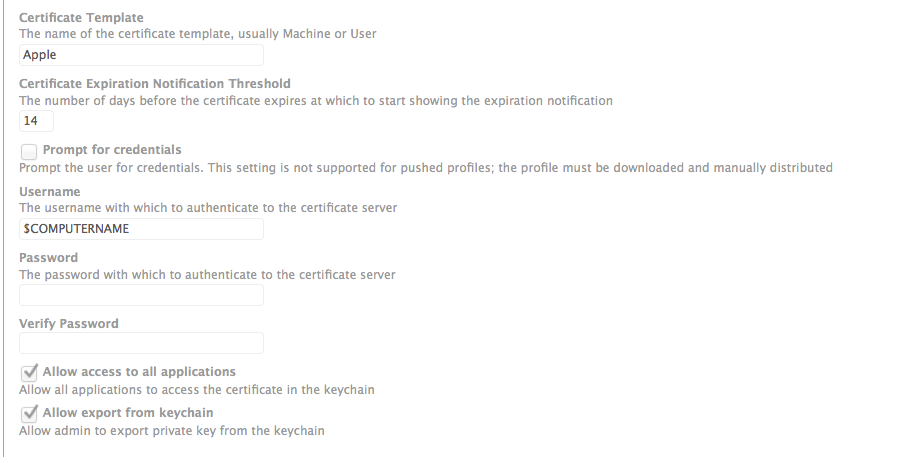
I generated the profile straight from the JSS so I did not add anything to the XML. My network team set up the Radius/AD side so I did not have to do much work except check the box for directory authentication.
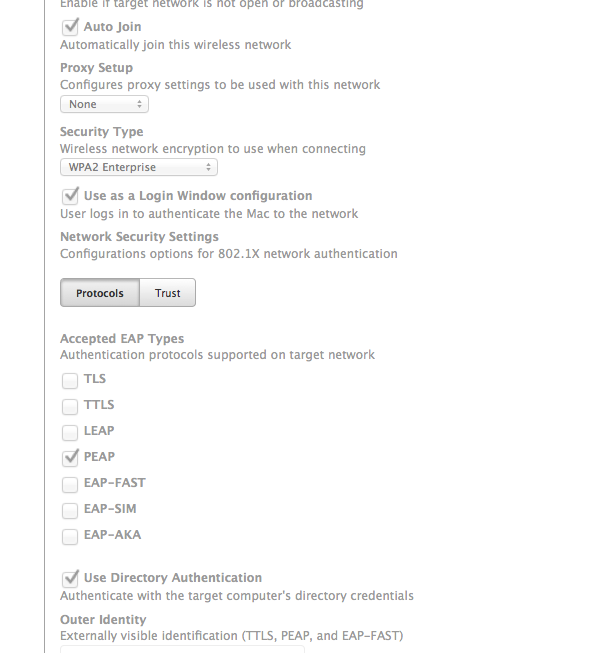
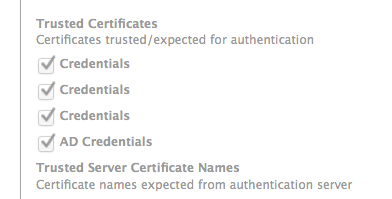
Make sure to import and trust the certificate the radius server uses and check the box for the type of authentication protocol you are using.
Don't check the box for Login Window Configuration if you are using Directory Authentication.
If all that is correct it is probably an error on the Radius/AD side.
It was a problem on the Windows side
Thanks
Larry
Can I also add that in my case the problem was our JSS was not fully up to date.
We were on 9.65 and experiencing errors in machine authentication before upgrading to 9.82. Prior to this our Mavericks laptops were using the exact same profile normally with 9.65 where out Yosemite and ElCapitan laptops were failing to join our hidden network.
We simply upgraded the JSS and it's been working ever since.
In between that we rebuilt the profile in Profile Manager, tried several manual hacks, wiped and reimaged til we couldn't wipe no more. I read through many many posts, advice, tips, tricks JAMF advice and guidance over the phone but the simple fix was making sure the JSS was current.
@LibertyJSS
Have you got this working? We are seeing some issues with NPS and 802.1X.
Everything is working fine with Radiator but we are moving into NPS soon.
Thanks
@Kumarasinghe
Aww man I just left work. I do have this setup and working as per the OP. If it has not been solved today, i will follow up tomorrow. I know I had to preload all my certs in the config.
Thanks.
Our 802.1X config is working fine and initially we thought NPS settings might be the issue but we found that WLAN controllers having delays in DHCP assignment to OS X devices.
Did some tcpdumps and working together with network engineers to get it resolved. Thanks anyway.
We're running 9.101.4 and I'm having difficulty getting this working. There's a product bug regarding the "Tick box" for Login Window Configuration. I guess it has appeared off and on through various versions of the Jamf. We are manually editing the mobileconfig file but are still having issues. Machine authentication works fine. We want to have the machine authenticate to 802.1x wifi then switch to the user authenticating against the wifi. Does anyone have this working on current versions of JamfPro?
@bhouston Did you get this working? We are working to solve the same setup issue. Machine Auth and then User Auth.