I have a couple extension attributes for Enterprise Connect that utilize the EC command line utility (/Applications/Enterprise Connect.app/Contents/SharedSupport/eccl).
During Mojave testing, I have noticed machines get a privacy prompt when I run a recon remotely via SSH on a machine.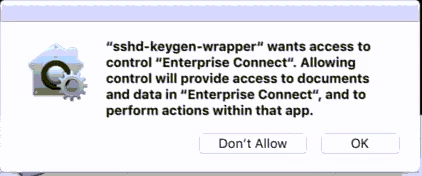
The first instinct is to create a privacy prefs policy for sshd that gives it access, but that seems like it could open up a security issue.
Has anyone run into something similar or have any ideas?




