Just upgraded to 10.11.1 from 10.11. I found something like below
- Passcode complexity NOT working
- Max Auto-Lock NOT working
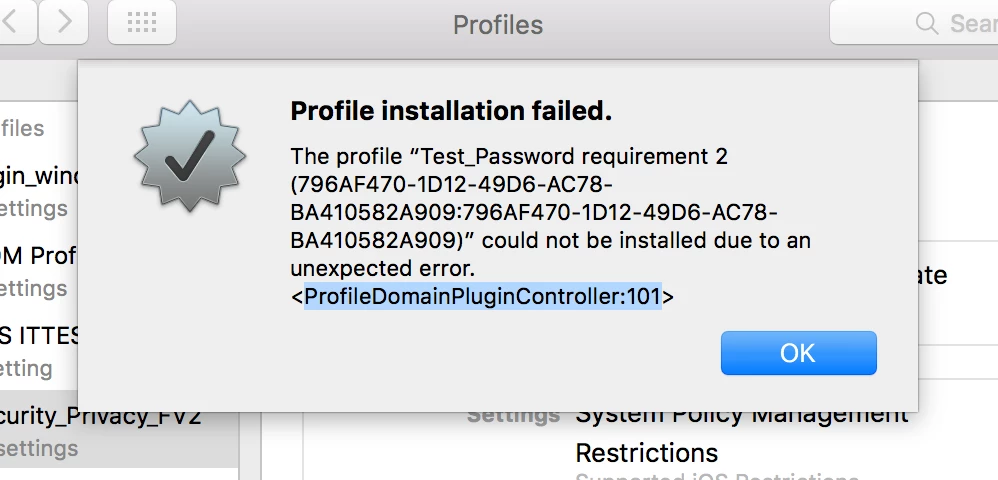
So my configuration profile including passcode settings is gone !
I did a couple of tests, and draw a line that the profile WONT install on 10.11.1 as long as it contains passcode session. here is my test process
A. Deploy a test profile to 10.11.1 Mac with Passcode session
- first create a test profile
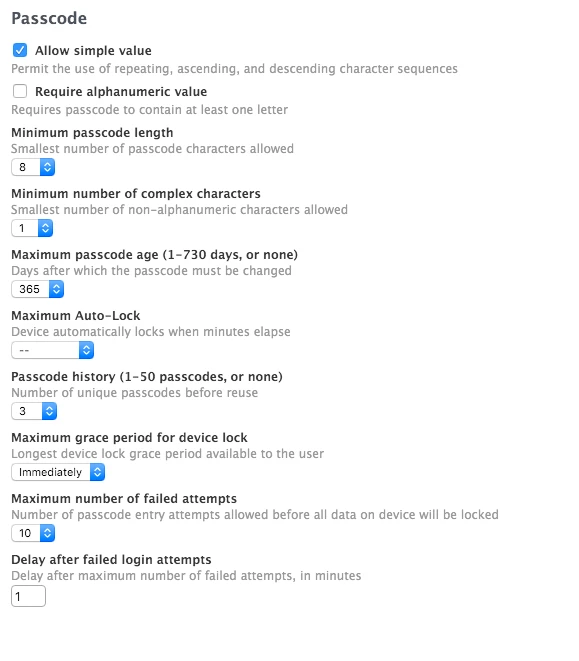
- Input passcode session, checked options like Require alphanumeric value, maximum auto-lock
- scope to my mac el capitan 10.11.1 only
- save and deploy
i found no new profile deployed on my mac. i did refresh all mdm profiles by running ‘jamf removemdmprofile and jamf mdm’, all the other profiles installed immediately, except the passcode test profile
then i did a 2nd test.
B. Deploy the same profile to my 10.11.1 mac with a random session excluding passcode, like Airplay
- open the same profile, remove passcode session
- create a airplay session
- scope to my mac 10.11.1 only
- save and deploy
now this test profile deployed immediately on my mac 10.11.1.
To double confirm with the passcode session, i did a 3rd test.
C. Deploy the same profile with both Airplay and Passcode sessions.
- open the same profile, (the airplay session is there, stays the same)
- add the passcode session like step no.2 in test A
- scope to my mac only
- save and deploy
i found the profile gone. i “refresh” the mdm profiles on my mac, all the profiles came back, except the test profile.
sh-3.2# jamf mdm -verbose
Getting management framework from the JSS...
Enabling MDM...
verbose: Attempting to install the mdm profile at the computer level.
The computer was successfully enrolled in MDM with the JSS.
so apparently it’s the passcode session not working, as long as enable the passcode session in a profile, the profile won’t install on 10.11.1
i need the workaround of setting Max Auto-lock urgently!