- Jamf Nation Community
- Products
- Jamf Pro
- "Casperread" attempting to reach phishing sites
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
"Casperread" attempting to reach phishing sites
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-25-2024 12:36 PM
Hi,
I am the System Administrator at an educational institution that utilizes Jamf software (has done so since Jamf was still called Casper). I am also a part of the security team, and a security software we utilize sent me a weekly report that an account called 'casperread' tried to reach a website known for phishing called contrarymeeting.com
I am hoping someone here can possibly explain why this happened, and if I need to be concerned. Does Jamf still rely on these legacy service accounts? Why is it trying to reach addresses on the internet to begin with?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-25-2024 01:25 PM
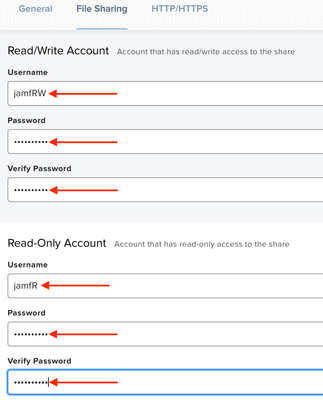
casperread, if memory serves me, is used if you have an AFP or SMB share configured for packages. The read account is able to mount the share to copy packages down to the device during policies, but has no ability to make modifications to the share, or at least that's how it's supposed to work. Do you know if this lines up with how your Jamf server is set up? Do you have a local sharepoint configured in Settings > File share distribution points? If so, do you see a "casperread" account listed as configured under the "Read-Only Account" option?
I can't offhand say why this account would have been flagged for trying to access a website. I didn't think they were used for anything around web access. Then again, a lot of times these accounts are actual service accounts in your directory service, so it's possible it's not even anything Jamf is doing here. The account might have been accessed from another system.
Lastly, my memory on how that account was used may not be complete, since it's been a while since I've had an actual non HTTP/HTTPS share configured with Jamf Pro. So take all that I'm saying here with a grain of salt.
Also, what version of Jamf Pro is your setup running?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2024 10:44 AM - edited 04-27-2024 10:46 AM
First thing I think of is the setting up a https distribution point document;
https://learn.jamf.com/en-US/bundle/technical-articles/page/Configuring_Red_Hat_Enterprise_Linux_7-6...
But as @mm2270 said, it could be a number of tools using this as a service account.
Another place to check is your local Jamf users and see what access / api permissions it has (if any or even exists). Indication whether it's being used by Jamf or something else 3rd party eg. AutoPKG
Sounds like a weak password sniffed out or sprayed against whatever is authenticating it and then used for web?Good luck!