Hi everyone,
I've been lurking here for quite some time as this forum has so much content... Anyway, the school where I work has decided to go with Casper for our Macs and JAMF's MDM for our mobile devices.
I've been playing around in JSS for the last week. Thankfully, next week is spring break so I will have some time where I can dig deep into this. I am looking for a recommendation on what we should do with our iOS WiFi configuration.
Our Wireless Arrays are set to broadcast two networks (which are segmented per building on our campus and per role - faculty/students):
1. SchoolFaculty
2. SchoolStudents
Encryption is done using WPA2 Enterprise. Authentication is done via 802.1x and RADIUS. We are using Windows Network Policy server to perform the radius authentication. Basically, students and faculty can login to their respective SSIDs on personal devices (given correct group membership within AD) using their username and password.
Here's an overview of how our one-to-one devices are currently connecting. Our school owned devices are connecting using device authentication, not user authentication:
- Windows Laptops connect using group policy, a wireless profile is pushed out based off of the device OU (students/faculty). Using a computer certificate and PEAP/MSCHAPv2 a connection should be established given they meet the constraints set on our policy server. Those constraints are that their computer resides in the FacultyComputer/StudentComputers group and the called SSID is the one matching the policy.
- MacBooks that have been enrolled into our JSS connect using a configuration profile. We also have separate profiles adding our PKI CA certificate as a trusted root and enrolling the device based off of the computer name name via SCEP. As far as I know, we aren't using a device identity certificate for connection. I've found that using the "Use directory authentication" checkbox in the profile payload is working well. I checked RADIUS logs and its authenticating based off the AD computer account that was set when the computer was bound to AD. That's the behavior I am expecting. The nice thing is that I didn't have to change anything in our RADIUS policies. The AD computer account for the MacBook can be added to the FacultyComputer/StudentComputers groups and the constraints would be met as expected.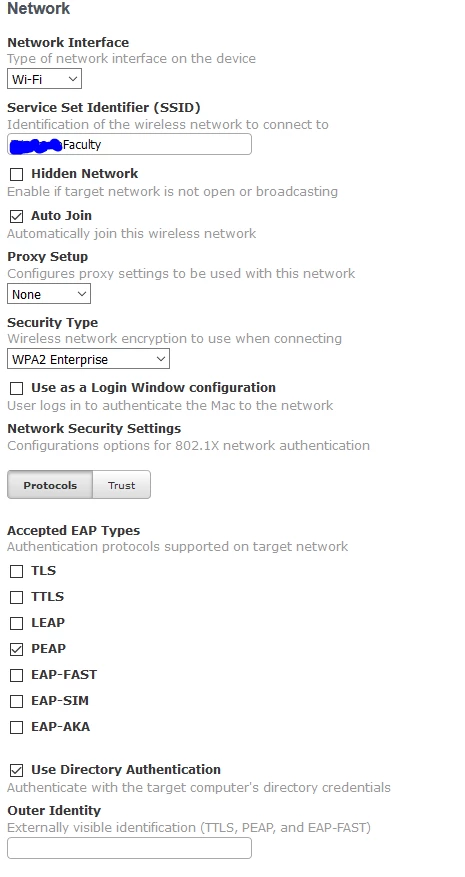
- iOS Devices currently connect using a separately broadcasted SSID called SchoolApple with a PSK for connections.
We would like to get away from the common SchoolApple SSID/PSK for security reasons. I would really like to scope out our SchoolStudents network to our student iPads and the SchoolFaculty network to our teacher iPads. Should we use a service account for authentication and forget device authentication? I have explored device authentication on iOS but haven't come up with anything concrete.
Does anyone have any recommendation based off of the above for iOS? Does anyone see any issues with our Mac configuration?

