- Jamf Nation Community
- Products
- Jamf Pro
- Running updates on High Sierra failing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Running updates on High Sierra failing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
04-19-2018
11:52 PM
- last edited on
03-04-2025
08:57 AM
by
![]() kh-richa_mig
kh-richa_mig
Hi all,
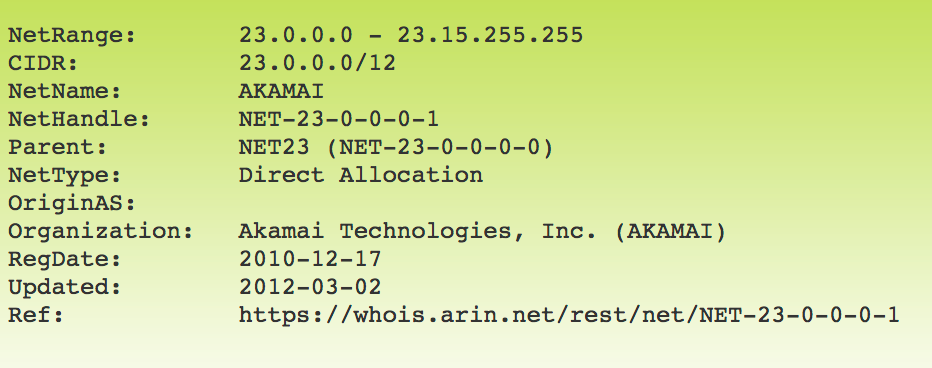
I'm having an issue where I can't run updates on new computers running High Sierra - not on our corp network anyway. We had it set up so the Apple 17/8 range was allowed, but I'm noticing in Wireshark that when running "softwareupdate" it instead tries going to 184.29.2.106 direct, bypassing any proxy info, which is an Akamai address (I'd imagine this is regional).
I can't find this documented anywhere. Has anyone else noticed that software updates are now going to a non 17/8 address? Is there some documentation buried somewhere that would list this? I had a hell of a time getting the Apple netblock whitelisted, I'm not sure I can get Akamai addresses whitelisted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-20-2018 07:02 AM
Apple uses Akami servers for some of their stuff. What stuff I have no idea, but I ran into the same issue and had to allow it in the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2018 05:00 PM
Does, uh... anyone have any info on this? My searches are showing up not a whole lot.
@Asnyder Was there a range you had to whitelist, or just the one address? I noticed that the IP I got resolved to a name with "static" in it. I haven't done enough testing to see if this is the only address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2018 05:21 PM
Also it looks like now that even though we've made exceptions to allow Apple addresses to go through the Proxy unauthenticated (which has worked fine up until now), in High Sierra it doesn't even attempt to adhere to proxy settings and just tries to connect direct. I've confirmed this by comparing Wireshark logs in Sierra and High Sierra.
Any info would be greatly appreciated, as I need to raise this with SecOps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2018 09:26 PM
HI @Aaron, I know we had some big problems with AKAMI, try whitelisting:
swcdn.apple.com.akadns.net
there might be some more which are needed
we had the network team monitor any software updates and add them one by one until finally the traffic was successful.
Can you run from terminal softwareupdate -l to get a list of available updates?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2018 06:05 AM
@Aaron If you have application control on your firewall you should be able to allow if that way. That's what I do. If you look at the second image you can see that the akami address falls under apple services, and more specifically the software update application.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-04-2018 12:12 AM
So I've been working closely with the networks team to try and work this out. With our current setup, we cannot whitelist against a wildcard (ie: *.apple.com).
Looking around, I've found this: https://www.richard-purves.com/2016/09/10/apple-services/
Which lists a large number of Apple services and their DNS entries. It seems pretty comprehensive, but does anyone have any other documentation that can be added to this?