Hi there,
I am trying to automate some processes based on our LDAP integration.
At this we have a stable integration with our LDAP and all the tests are successful. (Settings: System > LDAP servers).
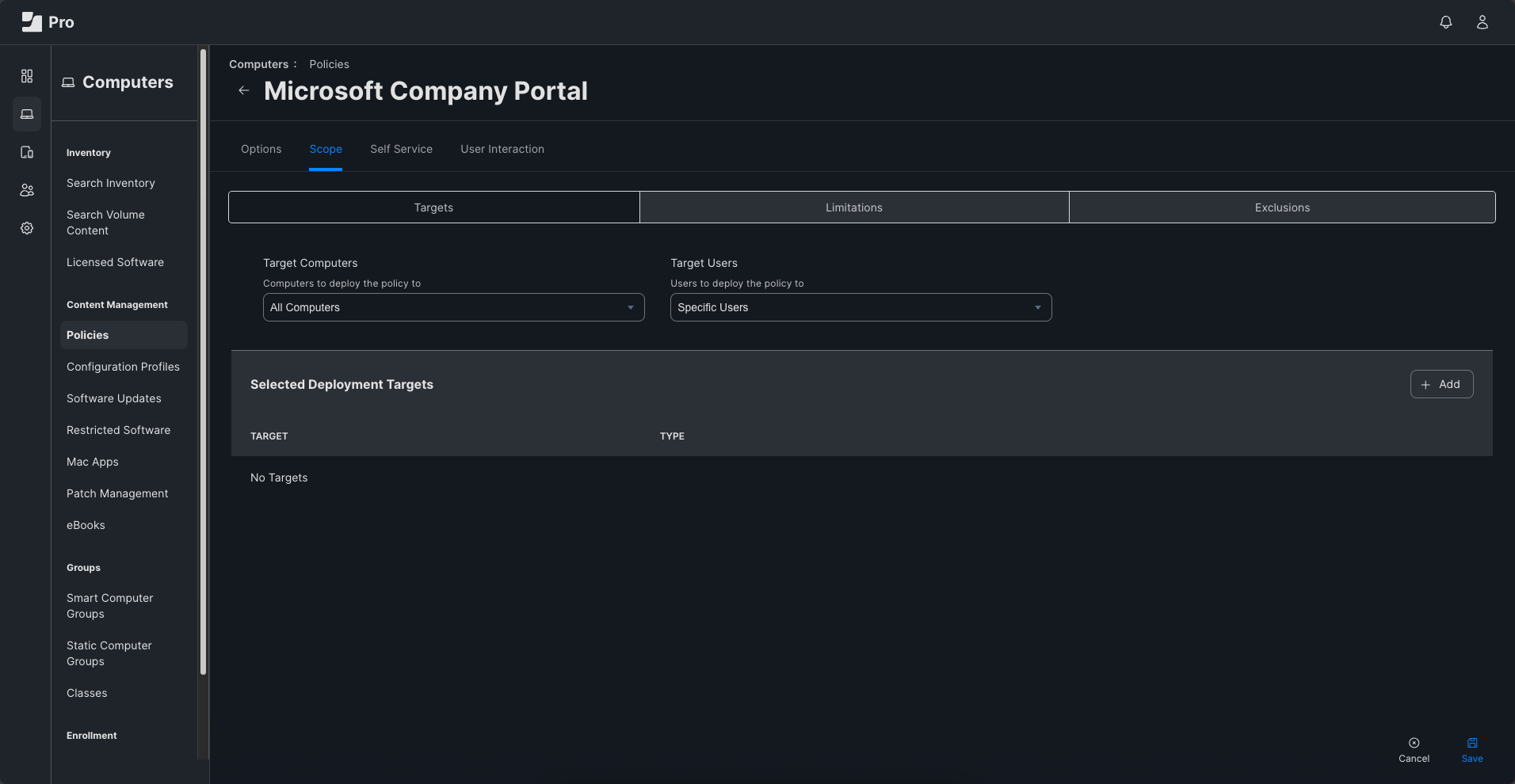
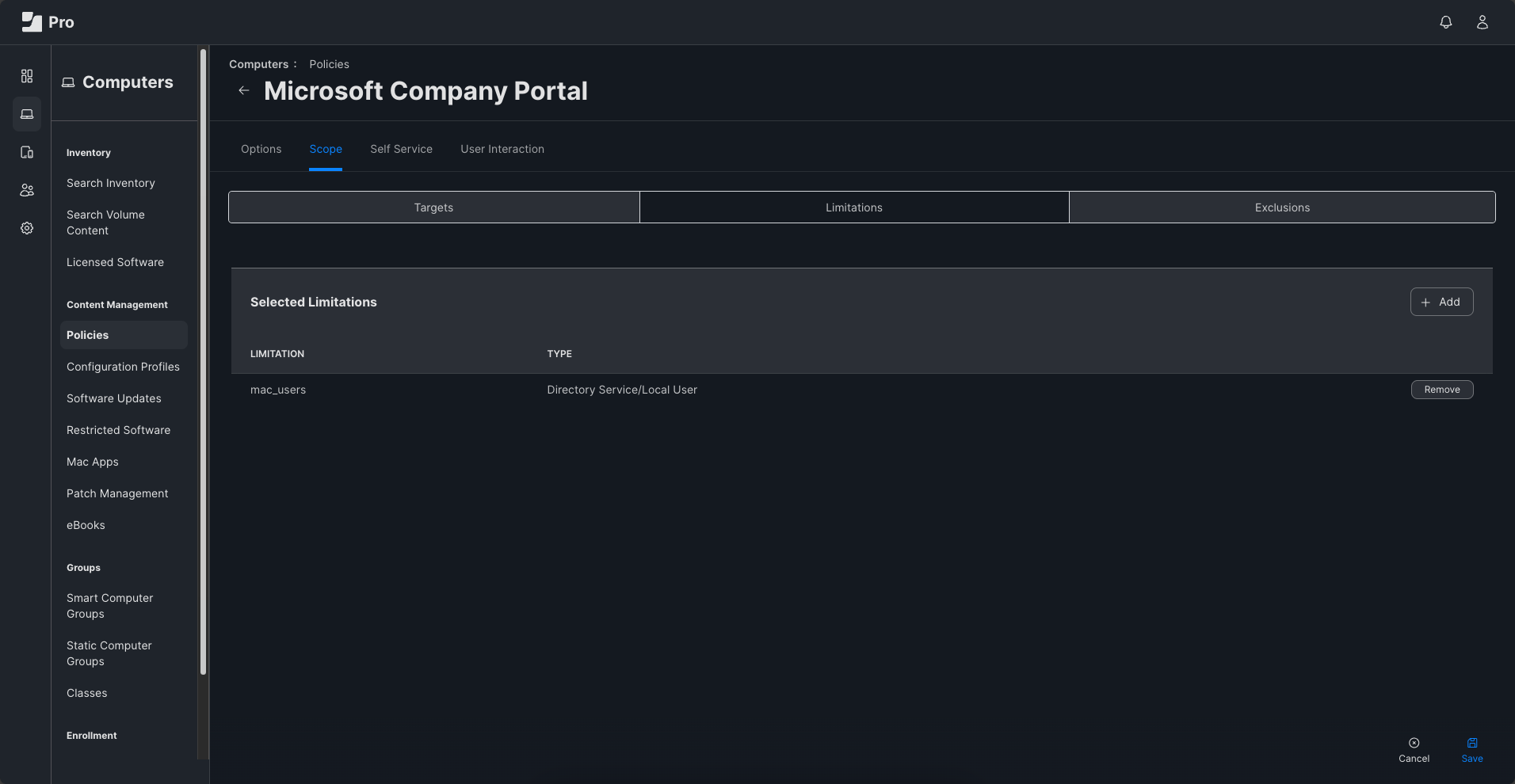
Group Names and GIDs are found. So far I was able to use the information for some configuration profiles. Now I want to use it for associating specific devices with a smart computer group but I am somehow stuck.
Ultimately, it should result like this: If user is member of a specific LDAP group, then the user's device to be associated automatically with a specific computer smart group.
In system > computer management, I created custom "extension attributes" to map the "Directory Service Attribute" "gidNumber" to the LDAP attribute for "GID".
But it does not seem to work. Any idea what I am missing?
Question
Smart Computer Group based on user's LDAP Group
 +4
+4Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.