Hi Jamf Community,
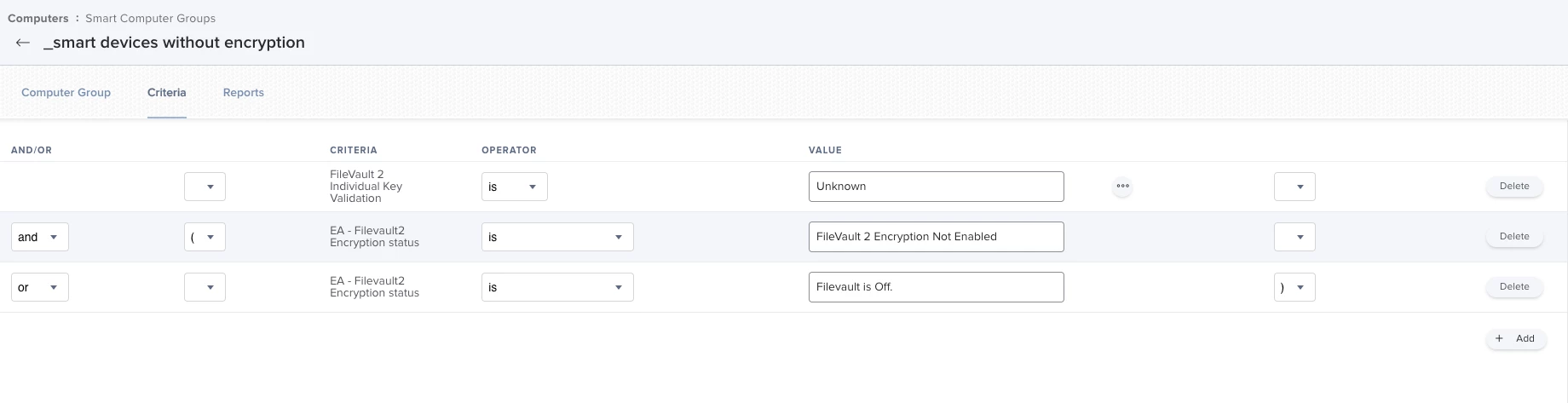
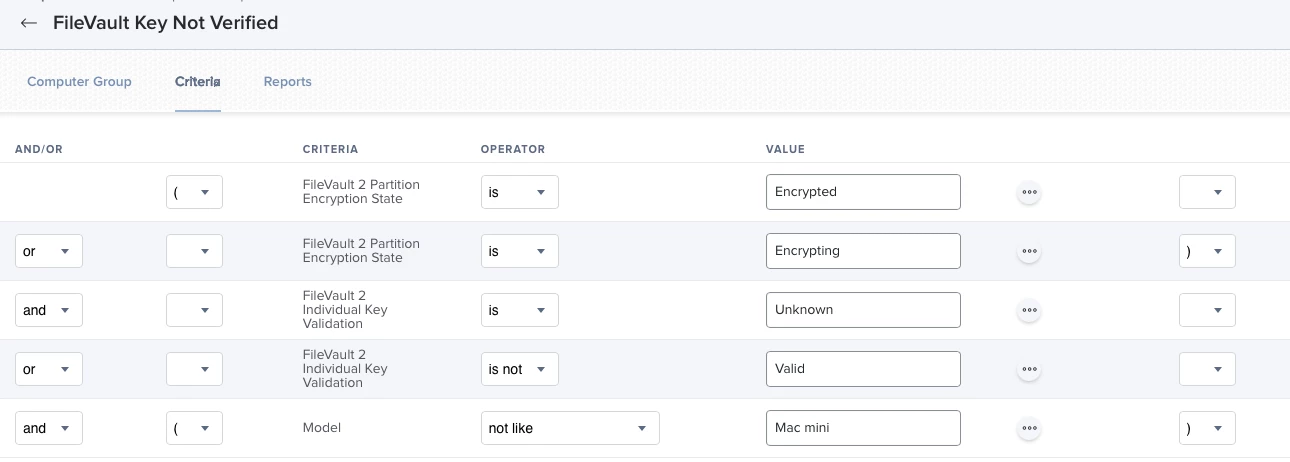
i have been trying to setup a search for all devices that dont have a personal recovery key set . Unfortunately there is no such option. Then i thought i could just check if the Filevault Encryption is "Valid". This would be great but, some of the devices in my jamf network dont have a recovery key set, but are encrytped. I was trying to figure out how to search for all of these devices so i could issue a new key for them. Is there any way to do this ?
Thanks ahead,
Raffael