I'm trying to determine if a Mac is On or Off the Corporate Network when scoping policies and a found @Rosko Joshua Roskos process on his git hub page https://github.com/jamfprofessionalservices/macNetworkLocation
The Issue I have run into is the API user w/ the following permissions:
Read & Update permission for Computer Objects
Read permission for Computer Extension Attributes
I found Computer Extension Attributes but not Computer Objects, there is Computers but if I give this Read & Update permission the script fails at "Sending network location to Jamf Pro..."
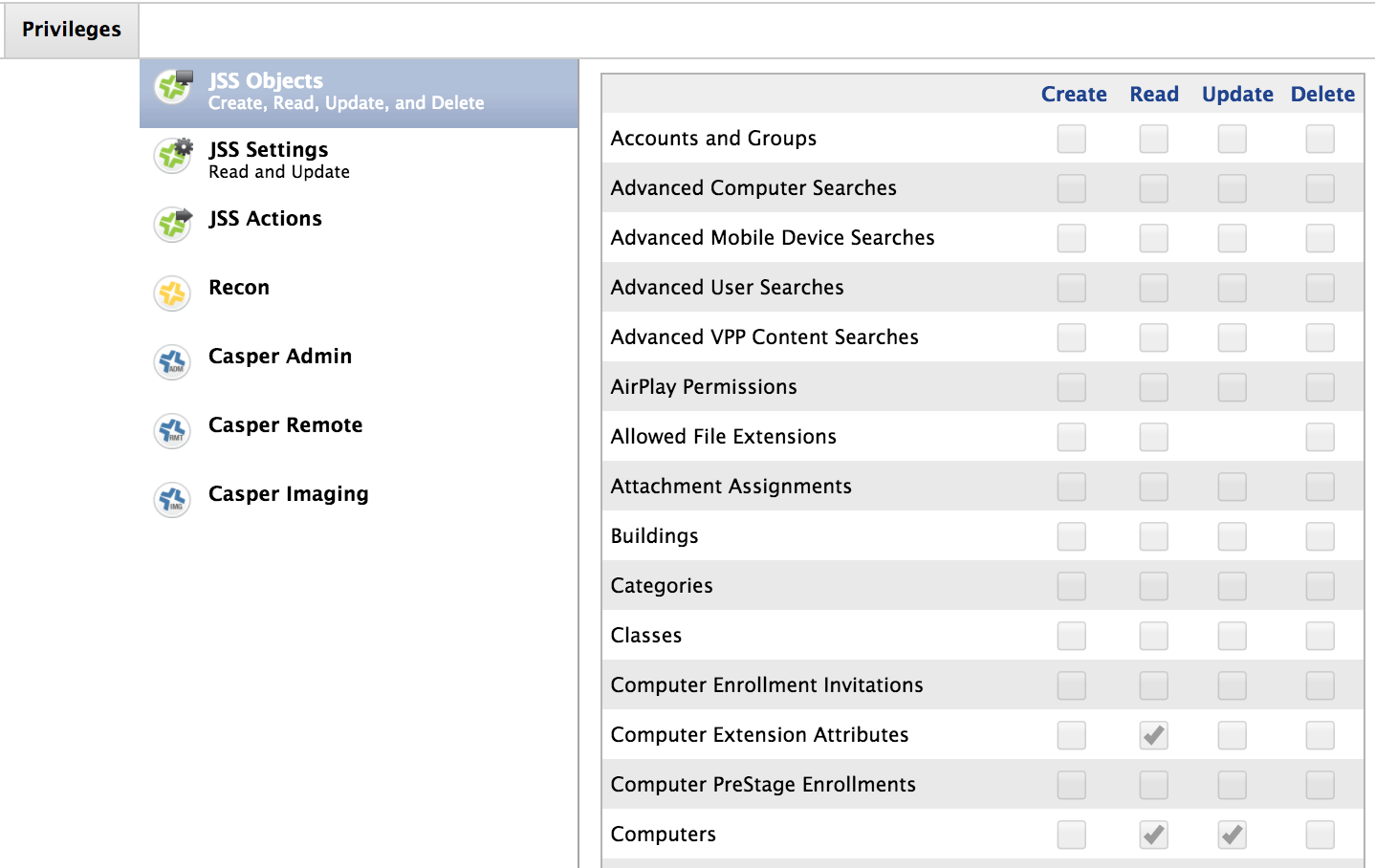
If I give the API user full admin permission the script is successful, so just need to fins out what permissions the API account needs



