We recently had a small group of laptops stolen. They were student checkout laptops and had wifi disabled. As soon as the theft was discovered I tied them to DEP with a prestage enrollment. One of them re-enrolled a few days ago with the JSS management account. Is there a way I can add a secondary admin account and keep it hidden? I would like to be able to ssh into the computer.
Question
Stolen laptop has checked in
 +3
+3Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.

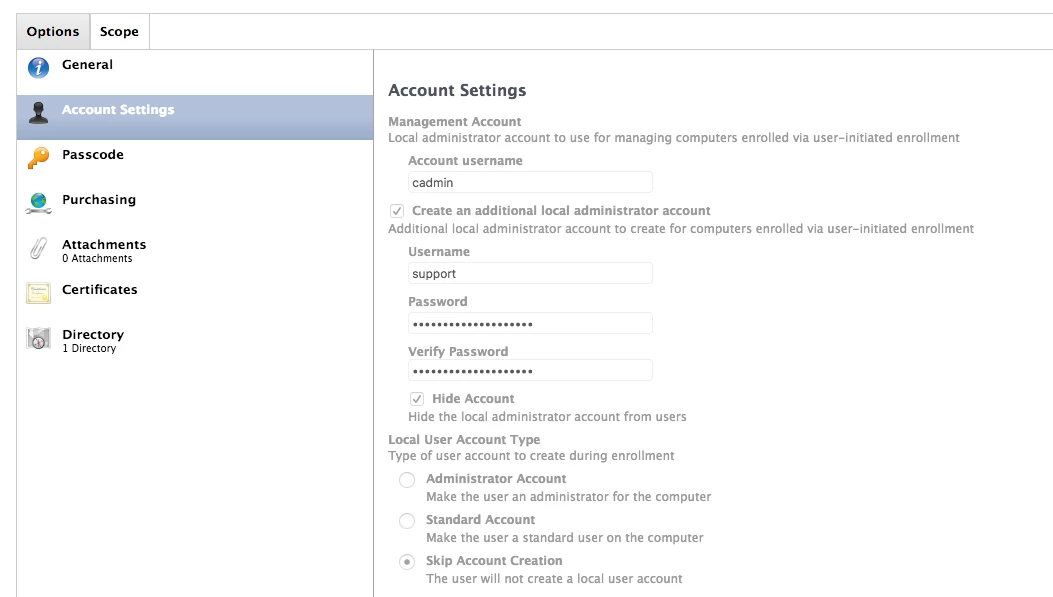 . But then SSH will be available to anybody.
. But then SSH will be available to anybody.

