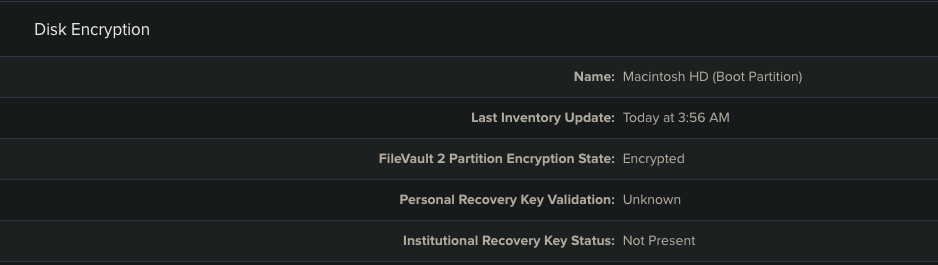
We've successfully deployed the reissue FileVault key script in our environment to send FV recovery keys to Jamf Pro to 99% of the Macs in our fleet. However, we have one Mac whose user is unable to send the key to Jamf Pro due to the following error: Error: User could not be authenticated. Error: Unable to unlock or authenticate to FileVault.
To be sure, the user is using his Mac password to unlock System Settings, unlock FileVault at login, etc. But it's unable to generate a new FV key.
Any suggestions on how to troubleshoot this sort of thing? I would prefer to avoid having to wipe/reinstall the OS unless it's the only option.