Hello Jamf Nation,
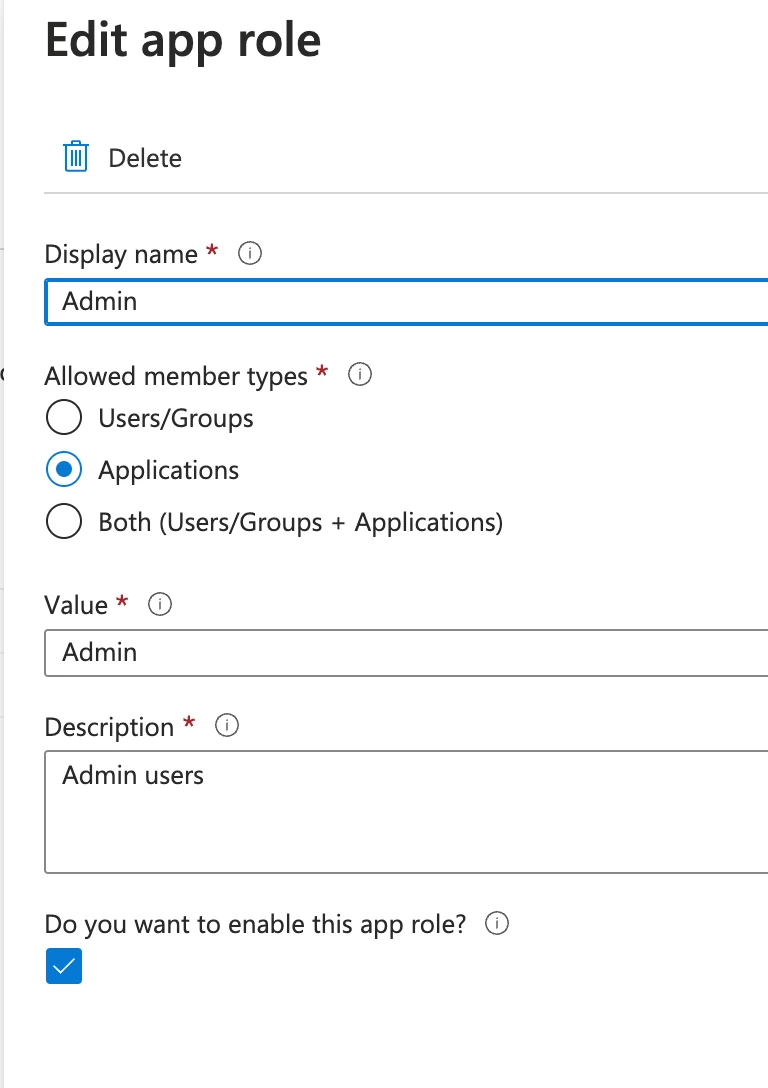
I had Jamf Connect configured to create the local user account as Administrator if the Azure AD user has the Admin role assigned in the Jamf Connect Azure AD enterprise application. This worked like a charm until we introduced an enrollment customization with Single Sign-On Authentication (with user information passthrough enabled).
Now the user first has to authenticate with Azure via SSO before confirming the password once more in the Jamf Connect flow which then creates the local user. Although the user has to enter their password twice, the added benefit is of course the automatic "registration" of the user to the computer object in Jamf Pro.
However, as the title of this post indicates, it seems the 'roles' attribute is now ignored and the local user is always created as Standard.
Is there a way to benefit from the enrollment customization without losing the user roles functionality?
PS. Using Jamf Connect 2.27.0.