- Jamf Nation Community
- Community & Events
- Jamf Nation
- Re: Cisco Secure Client 5.1.0.136- AnyConnect VPN ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2023 10:24 AM
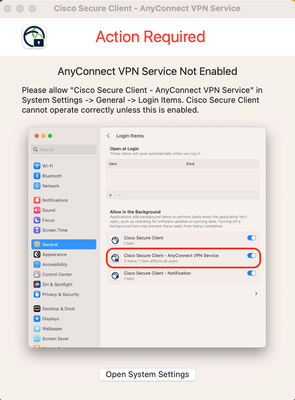
I've been down the rabbit hole of deploying Cisco's new Secure Client and I am running into an issue that I cannot find any documentation on. Some context: we only need the Umbrella Module for our school and nothing else that is loaded within Cisco's PKG. I have been successful with deploying the choice XML file, but I get the following pop-up in the installation:
I would like this permission to be enabled within the config profile I built in jamf, but I can't seem to locate any of the info I need to do so. I already have gone through Cisco's docs and pushed out the System Extensions payload, but that seems to be just for the Cisco Secure Client itself and not this "AnyConnect VPN Service." If I manually toggle it on, the Umbrella Roaming Module will activate and work as it should, but if this is not toggled on, then the roaming stays inactive.
Any ideas? I am assuming there is something I am missing in the System Extensions payload, but I could be wrong...
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2023 10:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2023 10:52 AM
The name displayed in that field is what Cisco wants it to be, not necessarily what it actually is. Cisco should have the documentation you need to get this approved. However, Cisco is also pretty well known for being beyond half effort with macOS.
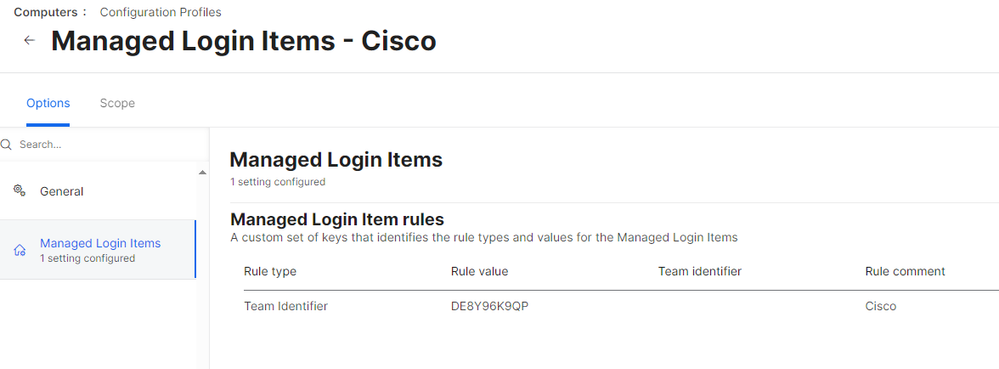
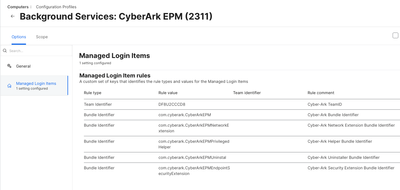
This is not a System Extension, it's a Background Service. You need to force enable the Background Service, or Managed Login Item as it's called in MDM. Below is an example of a configuration profile that would enable this toggle for an application called Cyber-Ark EPM. The general principle is the same for any Background Service approval.
https://support.apple.com/guide/deployment/managed-login-items-payload-settings-dep07b92494/web
https://support.apple.com/guide/deployment/manage-login-items-background-tasks-mac-depdca572563/web
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2023 10:49 AM
Looks like you need to make a
Managed Login Items for cisco
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2023 10:52 AM
The name displayed in that field is what Cisco wants it to be, not necessarily what it actually is. Cisco should have the documentation you need to get this approved. However, Cisco is also pretty well known for being beyond half effort with macOS.
This is not a System Extension, it's a Background Service. You need to force enable the Background Service, or Managed Login Item as it's called in MDM. Below is an example of a configuration profile that would enable this toggle for an application called Cyber-Ark EPM. The general principle is the same for any Background Service approval.
https://support.apple.com/guide/deployment/managed-login-items-payload-settings-dep07b92494/web
https://support.apple.com/guide/deployment/manage-login-items-background-tasks-mac-depdca572563/web
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2023 11:13 AM
Wow, yup that was it. Simple. I can't believe that step was missing from Cisco's Deployment docs. I just had to add the team id and the bundle id and boom. Thanks a ton!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2023 11:14 AM
Woot, I'm glad you got it.
@Jmardian wrote:
I can't believe that step was missing from Cisco's Deployment docs.
Oh, I can believe it was missing from their deployment docs. lol
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-02-2024 05:28 AM
Could you please post an example of the .mobileconfig
Would really appreciate it.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-02-2024 06:52 AM
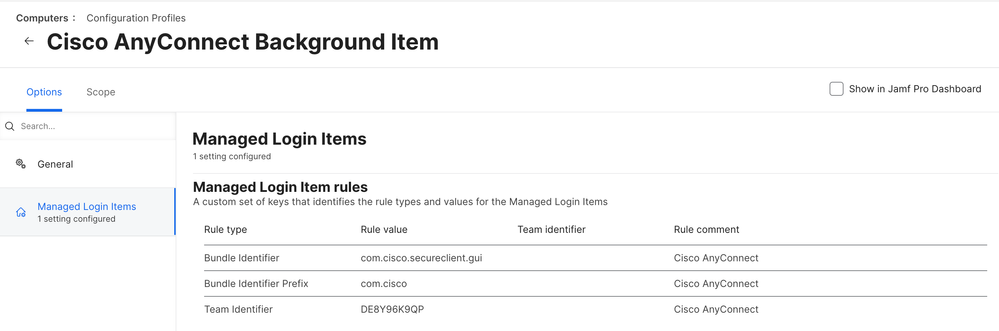
Got it working with the following config:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-12-2024 07:55 AM
Just curious if there was a reason to do both "com.cisco" and "com.cisco.secureclient.gui"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2024 02:33 PM
I have this working on 2 test Macs and on my production Mac, using the above config profile that @hhorn posted. However for 2 of my test users that I've deployed the same config profile to and the same version of AnyConnect (5.1.1.42), but they are still getting "no connection... Reattach failed"
What could be going wrong on my test users?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2024 07:12 AM
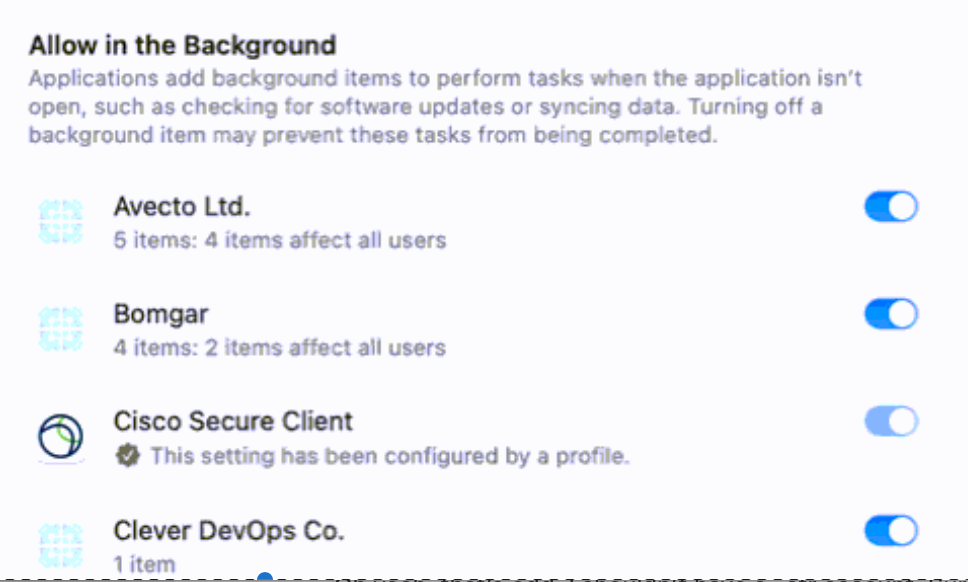
I found the problem is that the login item for "Cisco Secure Client – AnyConnnect VPN Service" isn't showing up on the devices that are having trouble.
On my device where it is working, I do have the item:
How can I get "Cisco Secure Client – AnyConnnect VPN Service" to show up here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2024 01:58 AM
I had the same issue, it looks like a bug in newer Cisco install packages, I don't have the issue with 5.0 install packages.
I fixed it by manually starting the VPN service after the installation with:
open -a /opt/cisco/secureclient/bin/Cisco\ Secure\ Client\ -\ AnyConnect\ VPN\ Service.app
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-15-2024 04:35 AM
They finally have a fix that they provided to us in a test build of 5.1.3.18. We haven't deployed it to everyone yet but every device I've tested with it works as expected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-16-2024 10:02 AM
Hello, I have the same issue with Mac OS Sonoma 14.4 and Cisco 5.1.0.136. I did not understand how you solved it. Could you explain deeply how to do for fix the issue. I do not have in login items the Cisco app.
Many thanks in advance for the help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-18-2024 04:42 AM
It is a bug with that version of AnyConnect. Cisco support provided us with a test built which solved the issue. The only way we could get the version you are using to work, is to run these commands either in Terminal or in a shell script after install.
sudo cp /opt/cisco/secureclient/bin/Cisco\ Secure\ Client\ -\ AnyConnect\ VPN\ Service.app/Contents/Resources/com.cisco.secureclient.vpnagentd.plist /Library/LaunchDaemons/
sudo launchctl bootstrap system /Library/LaunchDaemons/com.cisco.secureclient.vpnagentd.plist- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-21-2024 09:36 AM
had this issue today, thanks for the great work!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
4 weeks ago
Great fix! Did Cisco provide any documentation or perhaps a release note about this being fixed? I'd love to justify to my networking team why I'm requesting a newer version of Secure Client than the one they want me to deploy to our Macs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-27-2024 08:57 AM
Thank you very much!!! now it works!! Just someone else has the same issue: to fixing you should run the 2 codes separately.
Once again, Thank you!