- Jamf Nation Community
- Products
- Jamf Pro
- Re: 10.13.4 FileVault With APFS w/ Config Policy (...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
10.13.4 FileVault With APFS w/ Config Policy (Working - Testing)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
06-07-2018
09:24 PM
- last edited on
03-04-2025
07:43 AM
by
![]() kh-richa_mig
kh-richa_mig
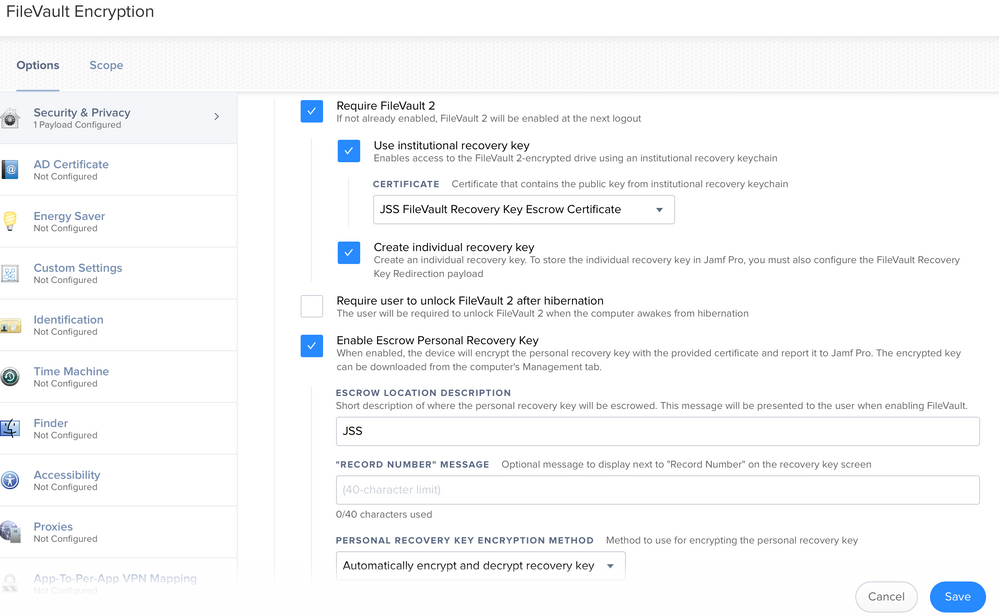
I thought I would share this. I did some testing as I was working with support and for some reason I got the individual keys to work with JAMF's configuration profile without using my own.
For whatever reason, if you select both individual and institutional it will allow you to Escrow the password and also encrypt. The only issue is that it prompts the end user when you log out for the password then shows the decrypt key.
I worked around this by using NoMAD NoLoAD profile that will encrypt on sign in. This completely makes the process seamless at least with an administrator account. I have to do additional testing in my AD environment at work with NoLoAD and a non-admin account, but for the built-in admin account it does allow you to do encryption.
Thought I would share!
Test Machine:
MBP 13 2017
OS: 10.13.4 (17E199)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2018 07:35 AM
Unfortunately when I got into work, it started asking for the admin decrypt key on login. I am going to continue testing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2018 08:15 AM
If you encrypt via Config Profile using the Individual key you will see the key displayed by default. There is a key you can set, ShowRecoveryKey, that you can set as False and it will suppress that. However, that means you have to download the profile, edit it, and upload it again.
We requested Apple to put that as an option in Configuration Manager, which they just released. There is an open FR now with Jamf to implement the same, so we can set this directly from the interface. Vote up!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2018 11:38 AM
Definitely voted that up!
This could be a make or break for my deployment. I have found it to use the inline config profile in the above way does work... but it just might need to be a manual process when setting up these devices. I can just have them accept it before we get to the onboarding portion by having our team login before the end user does.
I do think there should be a way to sync up the escrow keys when you have a user encrypt on login. The guys from NoMAD seem to have this working with other MDMs. This also suppresses any notification of filevault and does encrypt, but it seems when JAMF's binary runs, it changes the password before it escrow's and breaks the login process... I am still testing on this, hopefully I can find some sort of work around to use the escrow and NoMAD for that seamless FDE.