Hi all,
Can I please confirm that by integrating my AD CA to Jamf Pro, does it mean that i can push AD Cert to computers via Config Profile eventhough the computer doesnt have connection to the domain?
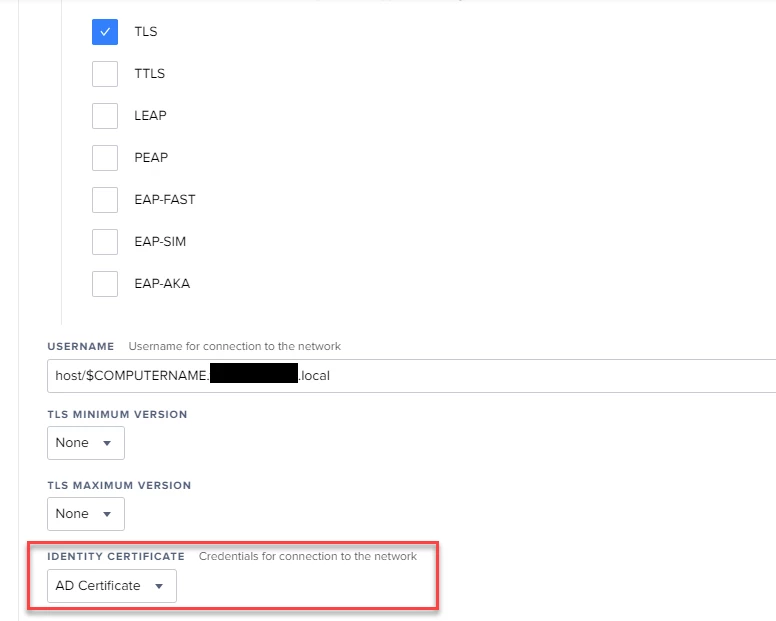
We are about to deploy .1x WiFi Profile to use AD cert for EAP-TLS and do have a concern with computers that are not on the network to receive the AD machine Cert.
Thanks
Update
Just to sum it up for other people's reference.
On your Certificate Authority
1. Right click Certificate Template - Manage Template
2. Select Workstation Authentication and Right Click - Duplicate Template
3. Type in the Template Display Name and Template Name
4. Click Security tab - Add Proxy Server computer and set Read, Enroll and Autoenroll permissions (as advised by Jamf)
5. Click Subject Name - Click "Supply in the request" option
6. Close Certificate Template Console - Right Click Certificate Template - New - Certificate Template to Issue - Select your Certificate Template
On your Jamf Config Profile
1. Add Certificate Payload
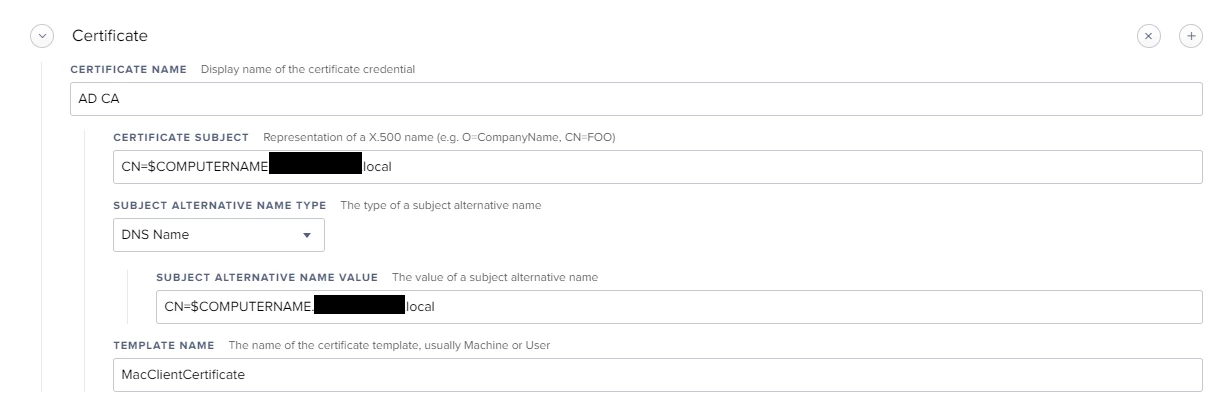
2. Give it a name, and set your Certificate Subject to "CN=$COMPUTERNAME.my.domain"
3. As a particular application in my environment requires Subject Alternative Name - i set it to DNS name with a value of "CN=$COMPUTERNAME.my.domain"
4. Template Name - as the one you created with the process above.
5. Depending on your CA structure, dont forget to add your intermediate and root certificate payloads so the certificate chain is valid.