Adding certificate with configuration profile - change trust settings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-18-2015 09:23 AM
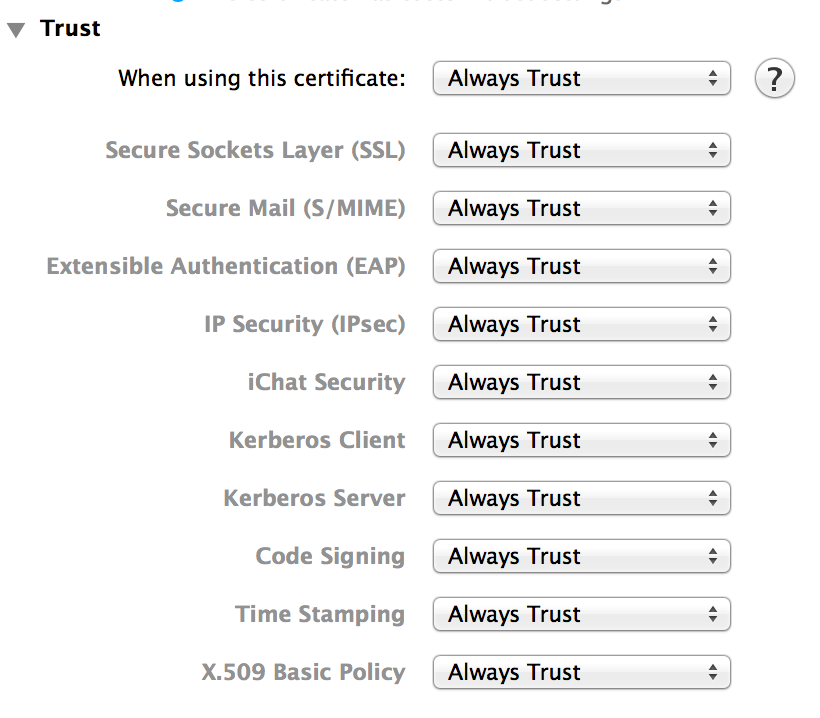
I'm deploying an 802.1x certificate to some of our endpoints using a config profile, and it's landing and appears to be trusted, but only using the system defaults. I've not been able to figure out a way to change these trust settings (Always trust) while still using a config profile (did find a link that described how to package it and manually trust it, but would rather not do it manually).
How are you guys doing this in your environments? If it helps, we're on 9.72.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-19-2015 03:40 PM
@grahamfw Certs delivered via a config profile should be set to always trust. Are you not seeing that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-24-2015 09:12 AM
I'm having the same issue as the OP. My trust settings for a System keychain cert aren't holding. Anyone know how to remediate this issue? I have seen posts regarding using the security command and exporting/importing trust settings. Kind of a PITA when using a config profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-15-2016 01:53 PM
Having this same issue when pushing out an intermediate CA. If I fully trust the cert, upload it, then redistribute it will show up as fully trusted for the user that exported the cert, but any new users get the untrusted version. Anyone else see this behavior and/or know how to fix short of using a follow-up command?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2016 08:30 AM
I experience the same behavior. I have deployed a cert using a config profile to two different computers and when the config profile applies the cert, the cert isn't trusted.
I then set the Trust Level to Always Trust, export the trusted instance of the cert to the desktop, then manually (not with a config profile) double-click the cert and it gets imported but isn't trusted using this method either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2016 10:21 AM
Anyone have and update for this? We have the same issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2016 10:26 AM
I gave up and ended running a policy that copied/installed the config profile locally then ran a post action script to import trust settings. It's messy but it was the only way I found to get what I needed done. Annoying and frustrating to say the least.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2016 12:52 PM
Good to know. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2016 02:59 PM
@dilan Can you be so kind to share your post action script?
Thanks
-3!gg3r-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2016 03:23 PM
@Eigger Below are snippet samples of the shell script I wrote to handle this. I copied the cert files and the trust setting file locally on the machine in a temp directory and then let the script handle the installation of the certs as well as the import of the trust settings. One thing to keep in mind is that you'll need to create a trust settings file based on what you have set. This WILL export all trust settings so it's best you create the trust setting file on a machine that has mainly (or just) the certs you want to deploy.
Terminal command to export trust settings (do this after you have manually set your cert trust settings on your test machine):
/usr/bin/security trust-settings-export -d /Path/To/Save/File/trust_settings.plistTerminal commands to install certs and apply trust settings (this is to be performed on your deployment machine):
Files needed in temp location: certificate file and trust settings plist file you created above.
Install cert to System Keychain:
/usr/bin/security add-certificates -k /Library/Keychains/System.keychain /temp/location/"AddTrust External CA Root.cer"Apply cert trust settings:
/usr/bin/security trust-settings-import -d /temp/location/eduroam_trust_settings.plistHopefully this makes sense. Basically you're copying your cert files and trust setting plist to the machine locally. You then run these lines above to install the cert and import trust settings. You can add something into your script to delete these temp files afterwards. If you need more details, please don't hesitate to ask.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2016 03:54 PM
@Eigger Also, if you're interested, below is how I handled the installation of the Configuration Profile:
Using Casper, I made the settings I wanted to deploy and then used the "Download" option to download the Config Profile file. I then moved this over to the local machine and let the script install it with the following command:
/usr/bin/profiles -I -F /temp/location/"Your Configuration Profile.mobileconfig"Your configuration profile should not include installing certificates as this is handled with what I described in my previous post.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2016 06:16 PM
Thanks Sir! will try this tonight! Have a good one!