- Jamf Nation Community
- Products
- Jamf Pro
- Re: ADMINUSERID is not in the sudoers file. This ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ADMINUSERID is not in the sudoers file. This incident will be reported.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 07:30 AM
hello JAMF,
i keep getting this error everytime i try to use sudo while on my supposed to be admin AD useraccount.
error = ADMINUSERID is not in the sudoers file. This incident will be reported.
my Mac is properly bound to the domain since i am able to do "su ADMINUSERID".
ADMINUSERID is not a local account.
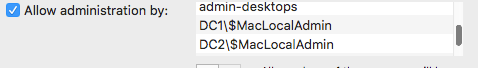
ADMINUSERID is a member of a security group that is listed in the "Allow admin groups" in Directory Utility.
security group name sample = $MacLocalAdmin
please help...
thanks,
-Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 07:52 AM
The "Allow administration by" option forAD groups in Directory Utility has never been reliable for me. You really want a local admin account on the machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 08:15 AM
@RobertAlviar I use the following from Rich Trouton's post here
%DOMAINGroupName ALL=( ALL) ALL
or commands you want the user or group to be able to run
ie %DOMAINADMINUSERID ALL=/sbin/shutdown -h now
If you are not comfortable using visudo command, you could always use the sudoers dropfile folder (/etc/sudoers.d)
Larry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 08:22 AM
we actually have a local admin account but since every support person knows about it, it is hard to identify who made changes to any machines (something like running some commands).
and this is why we decided to allow support personnel's own userID to be used for administration. and put them all to a specific security group.
it would really help if we can workaround this issue :)
is there a way to make the security group be a member of the admin group or sudoers group without touching the sudoers file? perhaps via Terminal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 08:31 AM
"Allow Administration By" should work if you are on the LAN (Mac able to talk to AD). If you are using a mobile account and go off the LAN you just need to check the box in Users and Groups to "Allow User to Administer this Computer".
If the groups aren't working on the LAN I'd double check the name is entered correctly (there is no verification in that field), group memberships, and AD binding....you should be able to get them to work.
This will list out the current groups in the Allow Administration By field, comma separated (might help verify they are entered correctly):
dsconfigad -show | grep "Allowed admin groups" | awk 'BEGIN {FS = "="};{print $2}' | sed 's/ //'You can change the groups like this:
dsconfigad -groups "group1,group2"- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 08:42 AM
@Josh.Smith
thank you for the response. i tried the first command and it resulted in this:
domain admins,enterprise admins,admin-desktops,$MacLocalAdmin
though i have this on my script when i add the group after binding to AD:
dsconfigad -groups "domain admins,enterprise admins,admin-desktops,$MacLocalAdmin"
-there is a backslash in front of the security group $MacLocalAdmin because we have 3 domains. should i edit the group name and have:
domain admins,enterprise admins,admin-desktops,DC1$MacLocalAdmin,DC2$MacLocalAdmin,DC3$MacLocalAdmin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 10:25 AM
@RobertAlviar I haven't tried this with multiple domains, good question. I know in a single domain it works with or without the domain specified before the group name, so it makes sense to try to include the domain. I think single quotes will be your friend here to include the :
sudo dsconfigad -groups 'domain admins,enterprise admins,admin-desktops,DC1$MacLocalAdmin,DC2$MacLocalAdmin,DC3$MacLocalAdmin'- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 10:26 AM
Here is what we have noticed and come to expect from AD Admin Groups and Mobile Accounts: The problem is that Apple does not cache all those AD groups onto the Mac itself, so if you restart the device while disconnected from the Network your AD is on, then you will lose your Admin rights, but if you stay logged in to the Mac, then your Admin rights will continue to work offline. The only fix I have seen for offline Admin Access is to add those Users to the Local Admin Group.
Here are two ways to add user a User to the Local Admin Group:
End User Enablement: Tech/User logs in while connected to the Network.
a. Open System Preferences -> Users & Groups
b. Select the Managed Mobile User Account from the Left Column
c. Check the box to "Allow user to administer this computer"
Script Enablement: Script method to enable Users if they are in the AD Admin Group or Remove them if they are not in the AD Admin Group. Please be aware that this should only be run while connected to the Network with AD Access. As with anything you get from here, please test and do not assume it works for your situation.
Just change the below "AdminGroupName" to your AD Admin Group Name and test.
#!/bin/sh
# Add User to Local Admin Group.sh
#
#
# Created by Edberg, Jesse L on 7/25/13.
#
## Grab logged in username
loggedInUser=`last console | egrep logged | awk '{ print $1 }'`
## Check User Group Membership for AD Admin Group
memberMacAdminCheck=`dsmemberutil checkmembership -U $loggedInUser -G "AdminGroupName"`
## Check User Group Membership for local admin group
memberLocalAdminCheck=`dscl . read Groups/admin GroupMembership | sed -e 's/GroupMembership://g' | grep $loggedInUser`
## If the User is in the AD Admin Group and not in Local Admin Group, then add to Local. If the User is not in the AD Admin Group and is in Local Admin Group, then remove User from Local.
if [ "$memberMacAdminCheck" == "user is a member of the group" ] && [ "$memberLocalAdminCheck" == "" ]; then
dseditgroup -o edit -a $loggedInUser -t user admin
echo "$loggedInUser is in AD Admin Group, but is not in the Local Admin Group. Adding user to local admin group."
else
if [ "$memberMacAdminCheck" == "user is not a member of the group" ] && [ "$memberLocalAdminCheck" != "" ]; then
dseditgroup -o edit -d $loggedInUser -t user admin
echo "$loggedInUser is not in AdminGroupName Group, but is in the admin group. Removing from admin group."
fi
fiGood luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 11:15 AM
@Josh.Smith i tried the command below but still getting the same error message.
sudo dsconfigad -groups 'domain admins,enterprise admins,admin-desktops,DC1$MacLocalAdmin,DC2$MacLocalAdmin,DC3$MacLocalAdmin'
@Jedberg i tested your script but to no avail.
will it be possible to add an AdminADGroup to the local admin group?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 12:22 PM
sorry i forgot to mention that after adding my AD adminAccount as a mobile admin account it is still:
unable to administer the computer
unable to unlock the admin padlock
still getting the error "AdminADaccount is not in the sudoers file. This incident will be reported."
and this is not an issue with a single computer. and since we manage 10k+ macs, hopefully we can get a solution that can be deployed on all machines.
if only there is a way to add a specific AdminADGroup to a LocalAdminGroup to gain sudo access without touching the sudoers file... and if it can be done via command in Terminal.
please share more of your thoughts... thank you...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 12:41 PM
I've never seen it not work, so I'm not sure! I'd try to verify that the Mac can see that the user account is in the group that is giving admin rights....you can use this command to list all of the groups a user account is a member of (source).
You'll need to change the DOMAIN and USERNAME parts of the following command:
dscl /Active Directory/DOMAIN/All Domains read /Users/USERNAME dsAttrTypeNative:memberOf | awk -F"OU" '{ print $1 }' | sed -e 's/CN=//g;s/,$//g;1d'- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 12:56 PM
@Josh.Smith below is my result.
bash-3.2$ dscl /Active Directory/DC1/All Domains read /Users/ADUSERID dsAttrTypeNative:memberOf | awk -F"OU" '{ print $1 }' | sed -e 's/CN=//g;s/,$//g;1d' $MacLocalAdmin $Admin-US-Citrix2Factor $role-gs-Casper $App-US-Citrix-RDPAdminConsoleMode-CorpFL $admin-gs-Field Support Admin-RemRes $role-us-breakfix $role-gs-MAC $role-us-mEUC $role-gs-EUC $Admin-US-CitrixSupport
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 01:06 PM
hey Robert as long as your systems are on OS X 10.11.x, the following could be run via terminal without touching the sudoers file:
cd /etc/sudoers.d
touch domainadmins
echo "%DOMAIN1GroupName ALL=( ALL) ALL " > domainadmins
echo "%DOMAIN2GroupName ALL=( ALL) ALL " >> domainadmins
echo "%DOMAIN3GroupName ALL=( ALL) ALL " >> domainadmins
I am sure you would be able to script it, but I listed this way for simplicity. I have this automated via puppet, but you should be able to make pkg, if you chose to go that route
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 01:17 PM
@LSinNY yes we are on OS X 10.11.x
i'll go ahead and test this out, i hope this is the answer :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 01:24 PM
@LSinNY actually i'm not good at scripting and i'm still a noob.
when i tried the first command in terminal here is what i get:
bash-3.2$ cd /etc/sudoers.d
bash: cd: /etc/sudoers.d: No such file or directory
what do i do?
i'm on OS X 10.11.4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2016 03:24 PM
as @Josh.Smith posted
You can nest AD groups in the admin group. Get the group name, e.g. "UKDomain Admins" and then run:
dsconfigad -groups "UKDomain Admins"comma separate if you want to add multiple groups. Check out the -groups section in the man page.
You should see the GeneratedUID of the relevant group added to the NestedGroups of the admin group. With the above example:
$ dscl /Active Directory/UK/All Domains read /Groups/"UKDomain Admins" GeneratedUID
$ dscl . read /Groups/admin NestedGroupsIf you want to check admin rights on a username:
dsmemberutil checkmembership -U [username] -G adminYou don't need to mess with the sudoers file.
The reason you may be struggling is that all of your AD groups appear to have a '$' sign at the beginning of their name. Bash could think this is a variable and as it isn't it will just appear as blank text.
Try using double quotes as per my example above. If that doesn't work, you may need to escape the '$' with a backslash or two.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-04-2016 11:39 AM
Hi Robert;
apologies as I was multitasking in 2 discussion groups yesterday. The solutions that @sean and @Josh.Smith will work, I use them in a firstboot script. The way I suggested would work, but you would have to create the folder first. I did not paste in that part of the solution, which should have been
cd /etc
mkdir sudoers.d
cd /etc/sudoers.d
touch domainadmins
echo "%DOMAIN1GroupName ALL=( ALL) ALL " > domainadmins
echo "%DOMAIN2GroupName ALL=( ALL) ALL " >> domainadmins
echo "%DOMAIN3GroupName ALL=( ALL) ALL " >> domainadmins
Thanks to Sean,Josh and others for following up to help
Larry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-04-2016 12:22 PM
@sean i tried what you suggested and what @Josh.Smith suggested but i am still unable to make it work.
and i decided to work on what @LSinNY suggested. i studied the script provided by @LSinNY and rewrite it and i come up on this:
sudo mkdir /etc/sudoers.d
sudo touch /etc/sudoers.d/domainadmins
echo "%domain admins ALL=(ALL) ALL" >> /etc/sudoers.d/domainadmins
echo "%enterprise admins ALL=(ALL) ALL" >> /etc/sudoers.d/domainadmins
echo "%admin-desktops ALL=(ALL) ALL" >> /etc/sudoers.d/domainadmins
echo "%\$MacLocalAdmin ALL=(ALL) ALL" >> /etc/sudoers.d/domainadminsand guess what... it works!!! thanks to @LSinNY . I am now able to do "sudo" commands.
But for some reason the AD Groups that i added under "Allow Administration by:" is not getting admin rights.
i comfirmed it after i tried unlocking the "Lock" to make changes in system preferences (i.e. ) and i used my ADUSERID that can do "sudo" now. :(
perhaps this is the main reason i am unable to get the sudo command working initially. maybe if it is able to get admin rights i can remove the sudoers.d folder to test if i can still do sudo.
i thought it is fixed but it seems there is another issue :(
still, I thank all of you for helping me :)
please advise on the next step...
-Robert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-06-2016 01:40 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-06-2016 01:55 PM
@LSinNY enjoy! waiting to hear from you again next week! :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-09-2016 10:01 AM
I was not able to duplicate your issue.My firs tboot script uses the commands that were given by @Josh.Smith , and I use the /etc/sudoers.d for individual control. Perhaps remove the file and retry the dsconfigad commanda
Larry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-11-2016 08:35 AM
@LSinNY
i was able to get on a different machine where the issue is not happening and the current configuration is just using the "Allow Administration by" and no sudoers.d file.
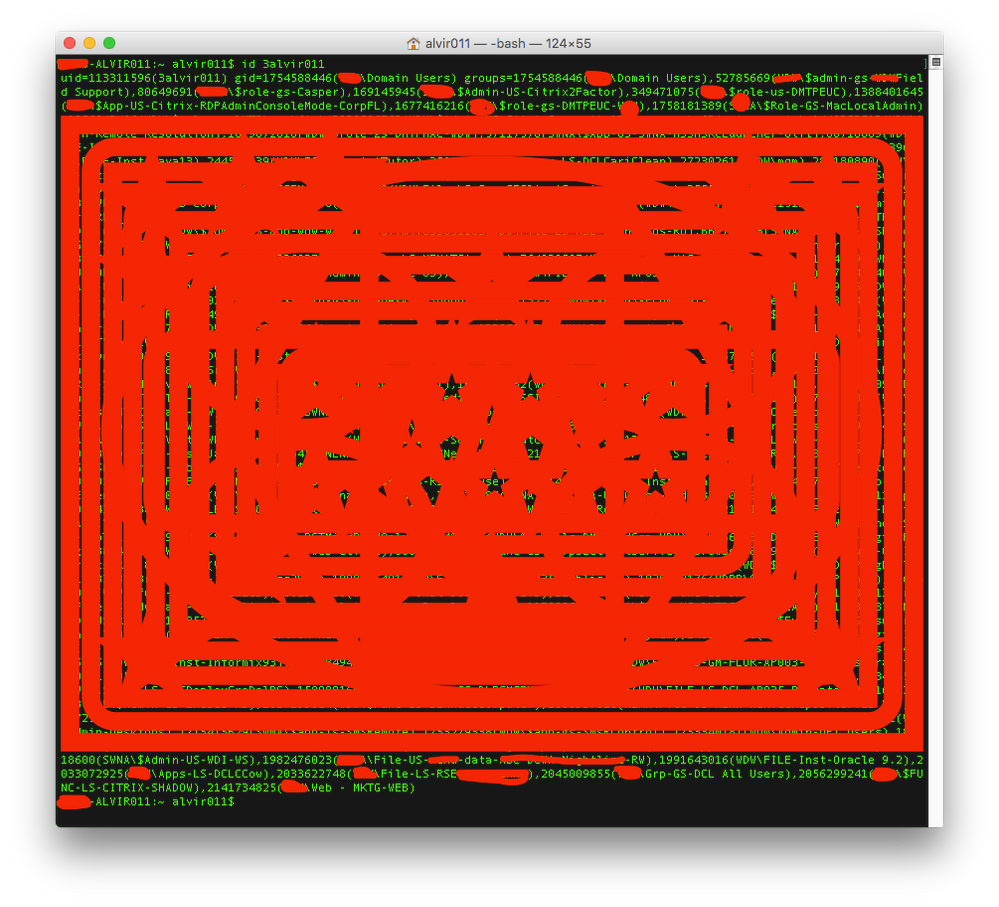
the difference that i notice is that on the problematic machine when i do
id <adminuserid>it shows a lot of groups...
and on the NON-problematic machine it shows...
also when i try
dsmemberutil checkmembership -U [username] -G [AD group name]the OK Mac results in "user is a member of the group"
the NON-OK mac results in "user is NOT a member of the group"
did i make a mistake on Binding the machine to the domain?
below is the script i used to bind the affected computers...
#!/bin/sh
#
# Bind To WDW
# 20160422 RA
#REBIND
computerid=`/usr/sbin/scutil --get ComputerName`
sudo dsconfigad -a $computerid -u <adminuserid> -ou "CN=Computers,DC=domain,DC=server,DC=com" -domain <domain.server.com>
sudo dsconfigad -mobile enable
sudo dsconfigad -mobileconfirm disable
sudo dsconfigad -useuncpath disable
sudo dsconfigad -preferred domain.server.com
sudo dsconfigad -groups "domain admins,enterprise admins,admin-desktops,$Role-GS-MacLocalAdmin"
killall DirectoryService
exit 0hope this helps, thanks! :)