I've setup an API role to Read Smart Computer Groups + Read Static Computer Groups but when I try the script (at bottom) following I get this result:-
Access token obtained successfully.
{
"httpStatus" : 401,
"errors" : [ ]
}
I'm fairly new to the API side of things so might be the script is inaccurate.
My Questions are:-
1) If I go to JAMF_PRO_URL/Api what do I put for username and password (screenshot below)? Is this an account that has access to the Jamf Pro instance or should this be client id / secret or something else?
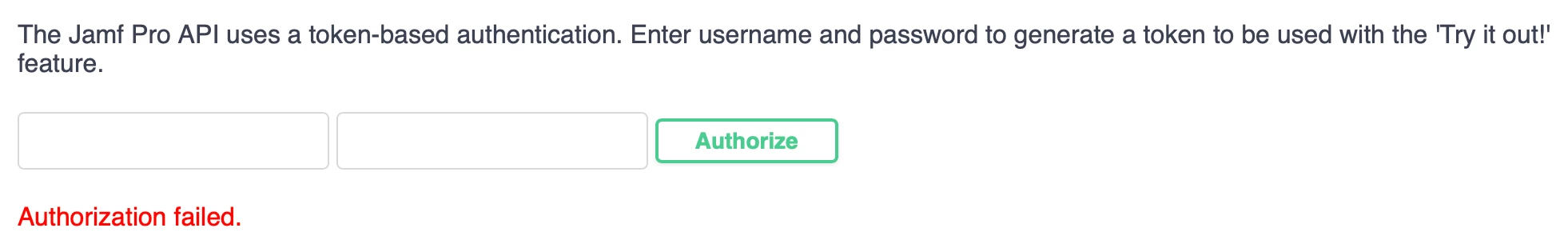
2) What privileges do you need as a user in Jamf Pro to be able to run these API calls?
3) Is there something wrong with the script below? If I do echo "$access_token" should it show details or would it be normal to get a response like "Could not extract value..."
For the script below I changed JAMF_PRO_URL to URL for Jamf Pro instance and CLIENT_ID + SECRET to details of the API Client.
#!/bin/zsh
baseURL="JAMF_PRO_URL"
client_id="CLIENT_ID"
client_secret="CLIENT_SECRET"
response=$(curl --silent --location \\
--request POST "https://$baseURL/api/oauth/token" \\
--header "Content-Type: application/x-www-form-urlencoded" \\
--data-urlencode "client_id=$client_id" \\
--data-urlencode "grant_type=client_credentials" \\
--data-urlencode "client_secret=$client_secret")
access_token=$(echo "$response" | plutil -extract "access_token" raw -)
if [ -z "$access_token" ]; then
echo "Error: Failed to obtain access token."
echo "Response: $response"
exit 1
else
echo "Access token obtained successfully."
fi
curl -X 'GET' \\
'https://JAMF_PRO_URL/api/v1/computer-groups' \\
-H 'accept: application/json'



