- Jamf Nation Community
- Products
- Jamf Pro
- Re: ARD Screen Sharing issue M1 Macs and Monterey
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ARD Screen Sharing issue M1 Macs and Monterey
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2022 12:25 AM
Hi All,
I’ve come across a strange issue stopping me rolling out M1 MacBook Pros to our users to replace older Intel machines.
I’m unable to use ARD to screen share onto an M1 Mac in these scenarios:
Filevault on and Firewall on
Filevault on and Firewall off
Works if Filevault is off and Firewall on or Filevault is on and Firewall is off.
I’ve tested a MacBook Pro 14inch and 16inch M1 running Monterey 12.0 through to 12.2 with the same result.
If I test an Intel Mac with the same Filevault/Firewall on, ARD works no problem.
Not sure if I’ve missed something daft on these M1 machines or a bug in Monterey on Apple silicon.
Cheers,
Robert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-04-2022 02:20 PM
I have not. I thought I had something, but it doesn’t work on Monterey.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-04-2022 09:22 PM
Likewise, I have not. I thought I had it, but Bol has been giving me some things to try. I've been slacking, due to work getting in the way. 😓
-But discovered how I can poke at it remotely to wake it up again by Disable Remote Desktop when I need to, as mentioned above.
To review, here's my current workflow...
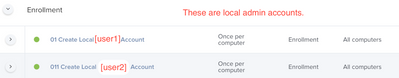
1st - a policy to create local admin accounts during my pre-stage enrollment
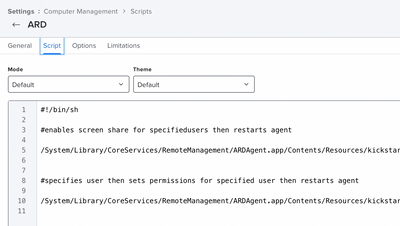
2nd - my ARD script
Script: Special thanks to "RossMadness." Source Link: https://www.reddit.com/r/macsysadmin/comments/f2recc/apple_remote_desktop_and_jamf_pro/fhec8aj/
==================
#!/bin/sh
#enables screen share for specifiedusers then restarts agent
/System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart -activate -configure -allowAccessFor -specifiedUsers -restart -agent
#specifies user then sets permissions for specified user then restarts agent
/System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart -configure -users [user1],[user2] -access -on -privs -all -clientopts -setmenuextra -menuextra no -restart -agent
==================
3rd - workaround, as mentioned above as needed:
In Jamf Pro, I went into a computer's Management tab and clicked Disable Remote Desktop button, refresh my screen, then do it again, a few times (which I thought was quirky) until I get the Enable Remote Desktop button. Once I got that, I was able to ARD into the workstation as normal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2022 05:29 PM - edited 05-10-2022 11:12 AM
I figured out a simple way to enable Remote Management using a script and a custom trigger that seems to work now.
Create a script like this:
#!/bin/sh #Turn on Remote Desktop Sharing, allow access for all users, and enable the menu extra: //System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart -activate -configure -allowAccessFor -allUsers -privs -all -clientopts -setmenuextra -menuextra yesSystem/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart -activate -configure -allowAccessFor -specifiedUsers exit 0 |
... attach it to a policy, use a custom trigger, run that in Terminal or set it to run itself after enrollment. I'm testing it now, seems to work.
Step #3 seems like the only other way to Enable Remote Desktop for now as well as messing with the API.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-09-2022 06:04 PM
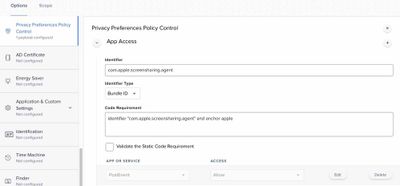
That’s what I have been using. Even with a PPPC profile, black screen on Monterey. I have resorted to keeping the PPPC and manually checking the Remote Management box and selecting all the options on each machine. Not ideal, but it’s working for now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-10-2022 10:31 AM
Same here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-21-2022 12:56 PM
Did you ever find a way to automate this? I tried multiple ways of the using the scripts in this post and haven't been able to make it work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2022 06:36 PM - edited 05-14-2022 05:20 PM
This is my script to enable ARD/screen sharing on Monterey/M1
#!/bin/bash
jamf_User="$4"
jamf_Pass="$5"
# Get the Jamf instance URL from the computer
jss_Url=$( /usr/bin/defaults read /Library/Preferences/com.jamfsoftware.jamf.plist jss_url )
#Kick start command
KICK_START_BINARY="/System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart"
echo "Enabling ARD..."
# generate base64 ecnrypted password
encoded_creds=$(printf "$jamf_User:$jamf_Pass" | iconv -t ISO-8859-1 | base64 -i -)
# generate an auth token. tr truncates and removes all line feeds
authToken=$( /usr/bin/curl -s "${jss_Url}api/v1/auth/token" -H "authorization: Basic ${encoded_creds}" -X POST | tr -d "\n" )
# parse token, remove expiration date
token=$( /usr/bin/osascript -l 'JavaScript' -e "JSON.parse(\`$authToken\`).token" )
# Get Mac serial number
mac_serial=`system_profiler SPHardwareDataType | awk '/Serial/ {print $4}'`
echo "Mac serial: $mac_serial"
# Get ID of the Mac from Jamf
JAMF_ID=$(curl --header "Authorization: Bearer $token" "${jss_Url}JSSResource/computers/serialnumber/${mac_serial}" -X GET | xmllint --xpath '/computer/general/id/text()' -)
#echo "Jamf ID: $JAMF_ID"
#Send MDM command to enable remote desktop for this mac
/usr/bin/curl --header "Authorization: Bearer $token" "${jss_Url}JSSResource/computercommands/command/EnableRemoteDesktop/id/${JAMF_ID}" -X POST
## Enable ARD options using the kickstart command
$KICK_START_BINARY -activate -configure -access -on -restart -agent -privs -all -allowAccessFor -allUsers
# expire the auth token
/usr/bin/curl "${jss_Url}uapi/auth/invalidateToken" --silent --request POST --header "Authorization: Bearer $token"
exit 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-09-2022 07:19 PM
Will this work on Intel Macs as well?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-10-2022 10:33 AM
Thank you. I'll have to give it a shot. To be continued...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-10-2022 11:07 AM
This is fantastic and very intriguing @junjishimazaki. Thanks, for sharing this. I've found that my script above works as well on Monterey. Give it a try, it's more simple and doesn't require auth tokens. I'm still testing it, However, this is awesome!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-10-2022 11:12 AM
I tried using the kickstart on the M1 and it didn't work which is why I ended up using curl to send the command to enable remote desktop. Then I use kickstart to allow the users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2022 04:34 PM
Do you mind if I implement some of your API calls into a script in a public repo and add you to the file header as a contributor?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2022 04:36 PM
I don't mind. Go ahead
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2022 04:37 PM
Thanks! I'll publish my variant of the script once I get some testing done on it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2022 04:39 PM
Sounds good and thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2022 05:03 PM
Do you happen to know the minimum API permissions needed to perform these functions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2022 05:19 PM
Thank you very much for this. This resolved the ARD screenshare error on the Intel/Monterey devices we have. Will also use this for the M1/Monterey.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-09-2022 07:20 PM
I haven't had any issues
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-12-2022 12:52 PM
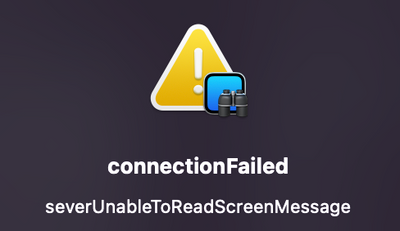
I am still having issues... I have tried the script provided by @junjishimazaki and although it appears to send successfully and I have a PPPC in place, I am getting the following error in ARD...
connectionFailed
serverUnableToReadScreenMessage
Any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-12-2022 01:26 PM
Hi kwoodward, I don't use a config profile. I only use the script and it works for me on M1/Intel macs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2022 04:45 PM
I still can’t get my Intel based Macs working. Your script works perfectly on M1 macs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2022 04:51 PM
I don't understand this should work on either one. All it does is send the command. It works fine for me on Intel and on M1. When you run it, do you get any error messages?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2022 05:13 PM
I get the following error when I try to connect via Apple Remote Desktop or the built in VNC…
connectionFailed
serverUnableToReadScreenMessage
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 07:43 AM
But, what error message do you get when you run the policy from Jamf?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 08:19 AM
I don't get any error in Jamf. As far as Jamf thinks, it installed correctly. In use, I get that popup message from any computer trying to connect to any Intel Mac, using ARD. It's perplexing to be sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 09:59 AM
Have you tried running the script locally on the mac?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 10:16 AM
I have, I get the same error when trying to connect from a different Mac using ARD. Again, only affecting the Intel Mac's.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 10:49 AM
Do you have any Config profiles deployed that would affect this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 10:51 AM
Nope, sure don't.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 10:59 AM
Trully bizarre. Do you have the firewall enabled on the mac?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 11:09 AM
Nope, this is affecting every Intel Mac on macOS 12...unless I had manually flipped on Remote Management.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 10:52 AM
Is the kickstart PPPC no longer required if you use the API to enable?
FWIW this applies to a mix of T2s and Apple Silicon for us.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 10:55 AM
My script doesn't require the kickstart PPPC since the script handles it anyway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 02:10 PM
Hello all. I'm just now finally getting back on this. Here's an update...
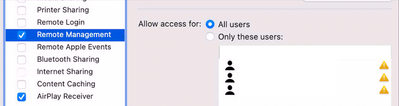
- Enable Remote Desktop from the Jamf Pro Computer Management:
- So far, the workaround of manually Enable Remote Desktop from the Jamf Pro Computer Management works except for one thing, that's all it is. I can remote to the workstation, however I can initiate a restart, a reboot, etc. from ARD tools. After investigating, I found that the options for the Enable Remote Desktop from the Jamf Pro Computer Management is just an "Observe" and "Control" only. -Plus for "All Users", not for the "Only these users."
- Junjishimazaki's Script Test: Failed Unable to Connect
- I removed an Intel machine and an M1, both with Monterey from my ARD script.
- I disabled Remote Desktop from the Jamf Pro Computer Management for each workstation.
- I created another policy with your script and scoped it out.
- It looked promising. It enabled it, however when I try to establish an ARD session, I get this on both machines:
Thoughts?
- I noticed that your script allowed "All users" with all options.
- "
## Enable ARD options using the kickstart command
$KICK_START_BINARY -activate -configure -access -on -restart -agent -privs -all -allowAccessFor -allUsers
" - I tried to do this below to specify a user that is created during enrollment... Unfortunately it didn't work.
- "
## Enable ARD options using the kickstart command
$KICK_START_BINARY -activate -configure -access -on -restart -agent -privs -all -allowAccessFor -specifiedUsers -users [user1,user2]
"
- "
- "
Any suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-08-2022 05:12 PM
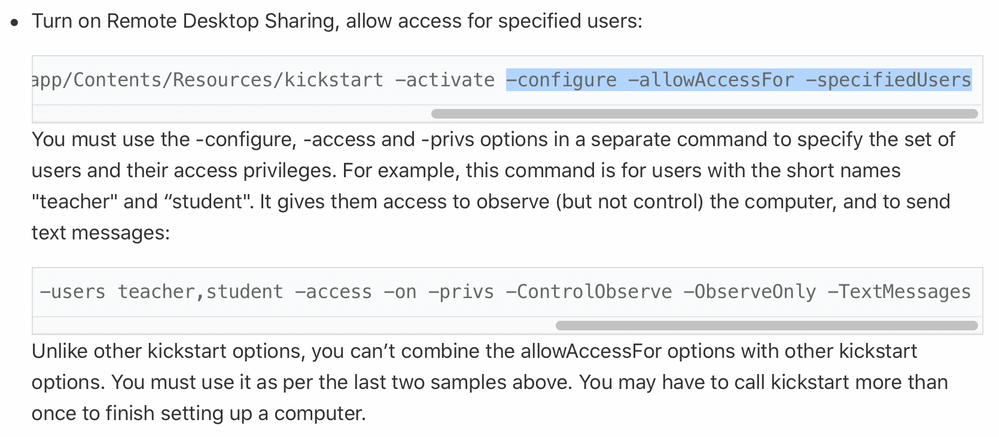
See here in Apple's old docs;
Try setting up like this;
$kickstart -targetdisk / -verbose -uninstall -settings -prefs
$kickstart -targetdisk / -verbose -configure -allowAccessFor -specifiedUsers
$kickstart -targetdisk / -activate -configure -access -on -users "$localUserName" -privs "$privs" -clientopts -setmenuextra -menuextra no -restart -agent -console -menu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2022 02:45 PM
Yeah Bol. The first two line above is exactly on my original script. Now I'm just updating that to fit in Junjishimazaki's script. Thanks for the $kickstart lines. I'll give it a shot.
Oh... This is for all local user accounts. Yes?
-users "$localUserName"
So for specific users, should it look like this?
-users "USER1" "USER2"
Or without quotes?
-users USER1,USER2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2022 03:23 PM
Didn't work. Here's everything combined:
#!/bin/bash
jamf_User="$4"
jamf_Pass="$5"
# Get the Jamf instance URL from the computer
jss_Url=$( /usr/bin/defaults read /Library/Preferences/com.jamfsoftware.jamf.plist jss_url )
#Kick start command
KICK_START_BINARY="/System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart"
echo "Enabling ARD..."
# generate base64 ecnrypted password
encoded_creds=$(printf "$jamf_User:$jamf_Pass" | iconv -t ISO-8859-1 | base64 -i -)
# generate an auth token. tr truncates and removes all line feeds
authToken=$( /usr/bin/curl -s "${jss_Url}api/v1/auth/token" -H "authorization: Basic ${encoded_creds}" -X POST | tr -d "\n" )
# parse token, remove expiration date
token=$( /usr/bin/osascript -l 'JavaScript' -e "JSON.parse(\`$authToken\`).token" )
# Get Mac serial number
mac_serial=`system_profiler SPHardwareDataType | awk '/Serial/ {print $4}'`
echo "Mac serial: $mac_serial"
# Get ID of the Mac from Jamf
JAMF_ID=$(curl --header "Authorization: Bearer $token" "${jss_Url}JSSResource/computers/serialnumber/${mac_serial}" -X GET | xmllint --xpath '/computer/general/id/text()' -)
#echo "Jamf ID: $JAMF_ID"
#Send MDM command to enable remote desktop for this mac
/usr/bin/curl --header "Authorization: Bearer $token" "${jss_Url}JSSResource/computercommands/command/EnableRemoteDesktop/id/${JAMF_ID}" -X POST
## Enable ARD options using the kickstart command
$KICK_START_BINARY -activate -configure -access -on -restart -agent -privs -all -allowAccessFor -allUsers
$kickstart -targetdisk / -verbose -uninstall -settings -prefs
$kickstart -targetdisk / -verbose -configure -allowAccessFor -specifiedUsers
$kickstart -targetdisk / -activate -configure -access -on -users "$localUserName" -privs "$privs" -clientopts -setmenuextra -menuextra no -restart -agent -console -menu
# expire the auth token
/usr/bin/curl "${jss_Url}uapi/auth/invalidateToken" --silent --request POST --header "Authorization: Bearer $token"
exit 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2022 09:01 PM
Yes sorry, replace with your local users, I am using a script variable so I can enter the username on the policy page.
Im sorry if it’s been said but are you all scoping these two settings by config profiles also?
I haven’t gone back to see if one or both is still required but I know, at some point of testing, they were both needed to allow ARD to work again in latest macOS builds.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2022 11:07 PM
I get the same results using a PPPC or without. Strange error, or a black screen.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-10-2022 07:17 AM
😣
Hmmm... 🤔