- Jamf Nation Community
- Products
- Jamf Pro
- Re: Block Mackeeper.app
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Block Mackeeper.app
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2018 09:47 AM
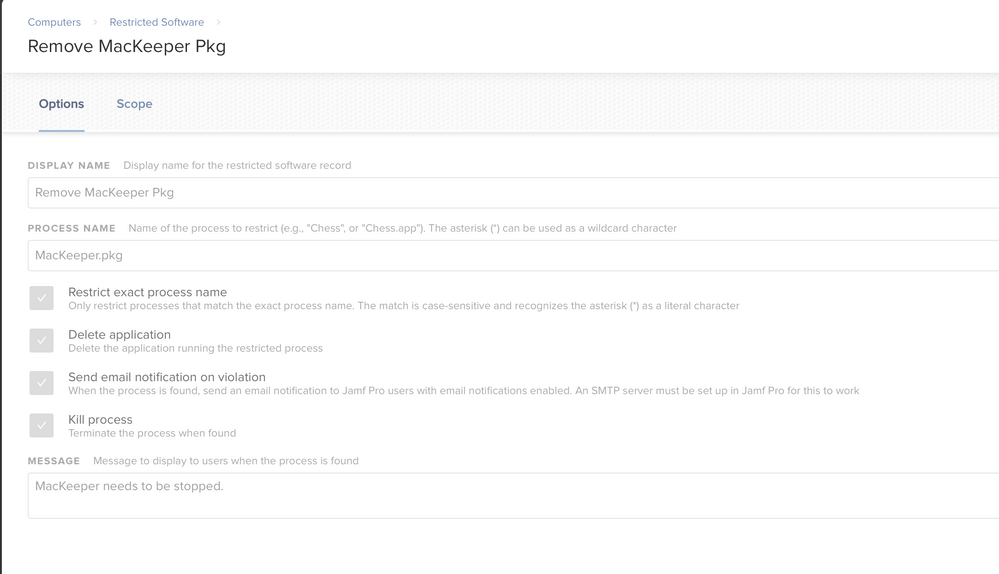
If you don't know what this is it's a nasty app that a lot of Mac users download. I would like to remove this file anytime it gets downloaded on a Mac. I need it to scan the users whole home folder. I have created a restricted app in JAMF, but it doesn't seem to work more than once.
Example file names:
MacKeeper.pkg
MacCleaner*
MacKeeper.app
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2018 09:57 AM
Are you deploying any kind of anti-virus software? I know for a fact that Sophos detects and blocks MacKeeper.
Also, why are you blocking the running of "MacKeeper.pkg"? In my experience, this is not what Kromtech has been calling their installer. Lately, they have been naming it "MacKeeper.version.number.pkg". The latest, which I just checked, is called "MacKeeper.4.5.10.pkg".
However, MacKeeper is also distributed through a huge network of nefarious sites and many of them rename the installer something else, so your mileage may vary on this one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2018 12:03 PM
We do have Sophos Cloud AV the security admin who manages says he can't block it (which I doubt is true). I just want to cover all .pkg or .app with MacKeeper in the name.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2018 12:34 PM
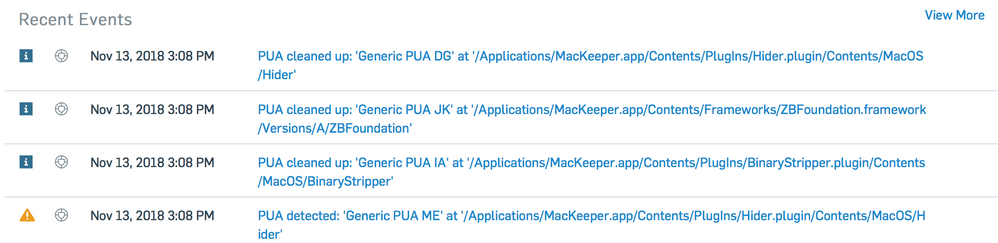
Not sure what to tell you. Here is Sophos Cloud detecting MacKeeper on a machine this morning.
And I didn't do anything special in my Sophos Cloud console. It's been detecting (and blocking most) PUPs for awhile now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2018 01:12 PM
Ok thanks I'll pass this on
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2018 01:22 PM
also like Damien said. Why are you blocking the pkg?
I'd suggest downloading it and figuring out what the binary is inside the app bundle. Then block that. Or blocking MacKeeper* but unchecking restrict exact process name.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2018 05:46 PM
Don't forget the user education aspect: no, you can't stop them from doing every single &^$&%!&^%# thing, but you can always at least communicate best practices: if it looks sketchy, it probably is; don't install 3rd-party extensions if you don't absolutely need them; Adobe Flash will be maintained by IT and available via Self Service, etc etc. Malware is a teachable leadership moment.
Malwarebytes and DetectX Swift are also options for endpoint security, although DetectX is only remediation, not active threat protection. (The Swift version, when licensed, has a command-line tool.)
You can also check for "MacKeeper" results inside ~/Library/Caches/, ~/Library/LaunchAgents/ and ~/Library/LaunchDaemons/. That may only show you past installations, but that could still be a useful follow-up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-14-2018 08:27 AM
I second @boberito. We use a wildcard (with asterisks on both ends of MacKeeper) and uncheck "restrict exact process name" and haven't had any issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-14-2018 08:30 AM
And right there is why I’m troubled at giving end users admin rights...MacKeeper and fake Flash Players!!
We keep Flash up to date but people install the garbage anyway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-14-2018 08:42 AM
Fake flash can sort of be installed without admin rights. I’ve seen it a lot at schools where kids aren’t admins. It doesn’t do much since it doesn’t have access to anything other than that account but still will deliver pop ups and ads and nonsense.