- Jamf Nation Community
- Products
- Jamf Pro
- Re: Changing FileVault key types (IRK to PRK)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Changing FileVault key types (IRK to PRK)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
02-23-2016
03:22 PM
- last edited on
03-04-2025
04:38 AM
by
![]() kh-richa_mig
kh-richa_mig
I got dropped into a sticky situation and need some help strategizing...
I'm trying to work out a system for getting a client's entire fleet (about 4,000 computers globally) to switch from an institutional FV2 key, to escrowed personal keys. There is currently a single management account on each machine, but some of the machines don't have that account enabled for FV2; on those particular machines, only the employee's account is enabled. Additionally, the password for that management account can be any one of many permutations of the management password, and there is no way to know for sure which one it is for any given machine.
I'm pretty sure I can solve the problem for the unknown passwords, as well as the problem for FV2 on the computers that have the management account enabled. I have a bash script that will reset the password for that account on all machines that need it. I can also use fdesetup to change keys on the systems that have the management account FV2 enabled (I believe). What I can't figure out is: how am I going to change the recovery key type AND enable the management account on computers that don't have the management account enabled?
The three strategies I can think of:
1. somehow use the institutional key and expect in a bash script to get past the fdesetup prompt to unlock the hard drive. (I haven't figured out how to do this yet)
2. prompt the logged-in user to enter their password into a branded OSAscript or jamfhelper dialog box and pass that to expect. (Infosec will never let me do this.)
3. manually enable the management account on all machines that don't have it enabled, then use the Casper policy to change the recovery key type
Is there any other way to do this? Am I overthinking this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2016 06:23 AM
Curious to hear how you tackle this just for the sake of knowledge (not going through this myself). Tagging the insightful @rtrouton to hear his thoughts on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2016 09:34 AM
thanks bpavlov!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2016 11:08 AM
The best solution I can think of is something like #2, which is unfortunate because you indicated your Infosec folks would not go for it. The general idea is described here:
https://github.com/homebysix/misc/tree/master/2015-01-27%20MacBrained%20Reissuing%20FileVault%20Keys
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2016 11:13 AM
Thanks Rich, I probably should've bugged Elliot directly. :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2016 11:17 AM
@definition Are these machines already in the JSS, AND did the original FV process get pushed through the Casper, or were they encrypted outside of Casper?
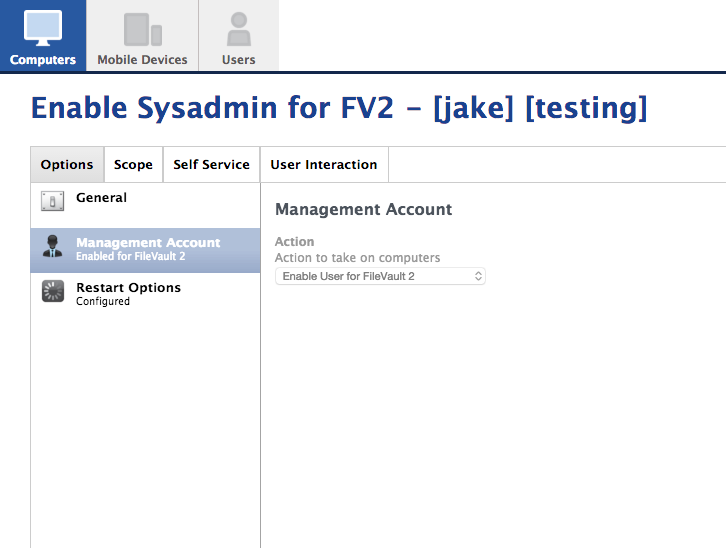
If they were encrypted via Casper, then adding the management account to FV shouldn't be that difficult. It can be done via a policy that simply enables the management user for FileVault:
Once you've done that, changing the FV keys I believe can also be done via a Casper policy, although I'm not 100% on this since you're looking for escrowed personal (individual) keys.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2016 11:32 AM
@stevewood, That's a good question. I would like to assume the machines were encrypted via Casper, but I can't be positive since I've only just started working with this fleet. It's possible that the previous admin scripted FV2 for many of the computers.
When I do try using a policy to enable on a test computer, I get "Error adding user to FileVault: Added users failed error."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2016 11:34 AM
@definition with that error, I would assume that they were not encrypted with Casper, which makes life more difficult. I'm with @rtrouton that @elliotjordan method is probably your best bet.