Microsoft has released Company Portal 5.2401.2 with support for Platform SSO.
Users with SSO profiles receive a pop-up requesting registration with Azure Account to synchronize the local Mac password.
Has anyone had this experience?
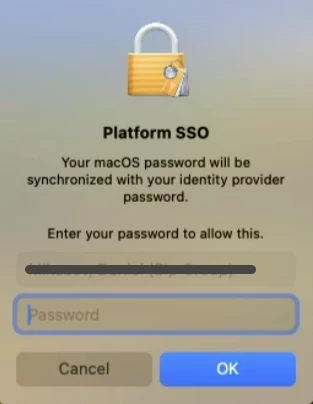
Microsoft has released Company Portal 5.2401.2 with support for Platform SSO.
Users with SSO profiles receive a pop-up requesting registration with Azure Account to synchronize the local Mac password.
Has anyone had this experience?

Best answer by rabbitt
For anyone following this topic, we have some remediation documented at https://www.jamf.com/blog/entra-id-platform-sso-device-compliance/ [link updated 4APR2024]
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.