- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2022 12:50 PM - edited 03-03-2022 12:53 PM
I'm trying to deploy FortiClient 7.0.2, and I have some questions about order of operations and whether this is going to cause trouble on specific OS versions. I still have some more testing to do but it seems to work on the one I tried, but maybe it was a fluke. I can post configs as necessary, but I suspect that they aren't needed for these questions as it's more about how these functions work.
I have a script that grabs the file from our server and installs it. That works. I need to get curl to fail out of the script if the download fails, but I haven't looked into it yet so I'm sure I can find a way.
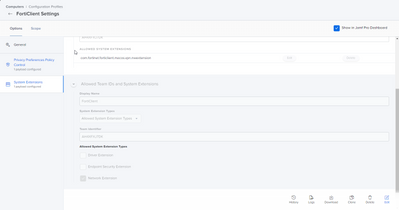
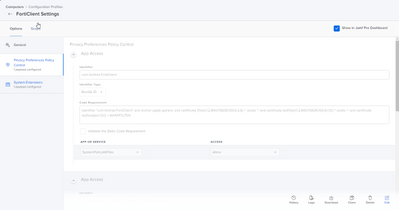
Unfortunately though, FortiClient needs users to make tons of changes to System Prefs. Full Disk Access, requests for VPN connections, and request for System Extensions.
I used PPPC to grab those Full Disk Access settings from an install and make a config profile.
- Will it cause a problem if I deploy those before the policy for the install, when the filepaths and apps don't exist yet? It seems to be working this way currently, but I don't see those settings in the System Prefs Privacy panel. Are they hidden because they're installed this way?
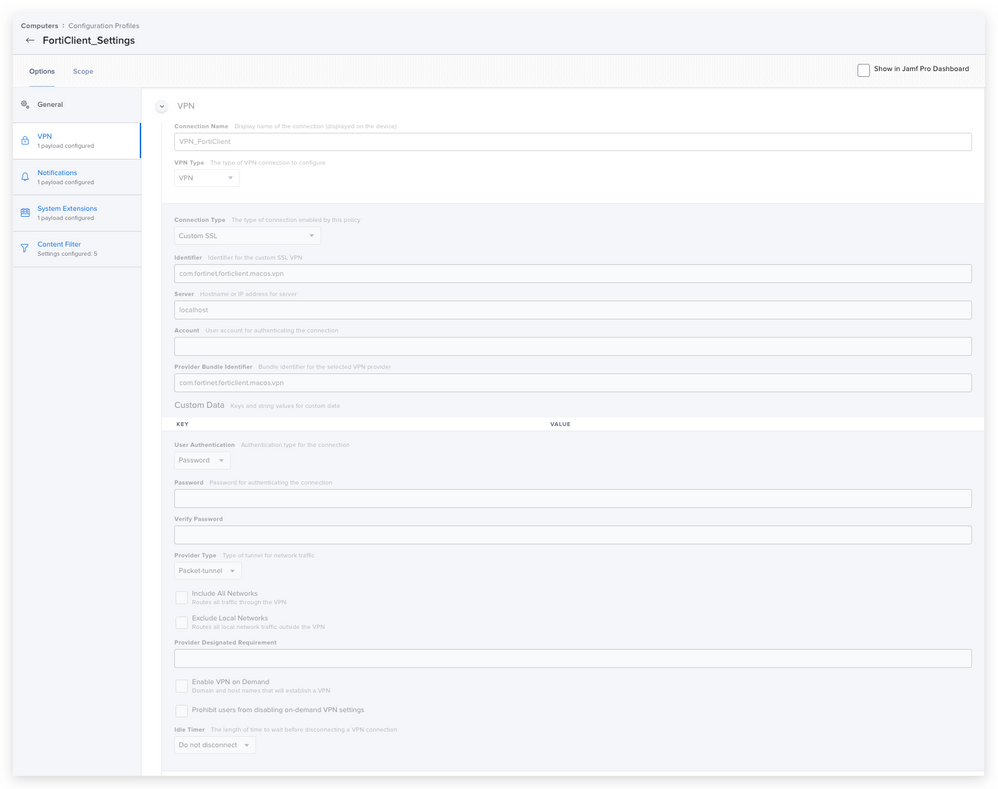
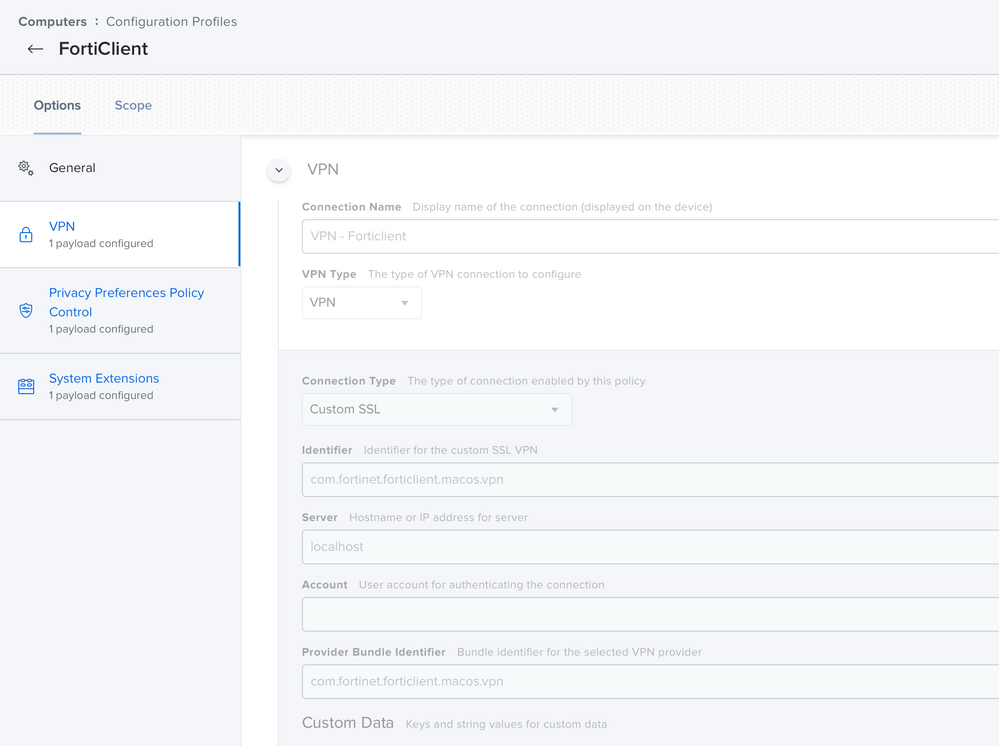
I have a blank VPN being deployed in the same config profile using com.fortinet.forticlient.macos.vpn in the Custom SSL settings (someone else on here suggested this solves that issue if you deploy it first). I haven't tested this, but supposing it works I don't have any questions about it since I know it needs to go on first.
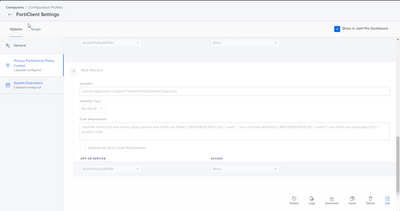
System Extensions is the only other thing I'm worried about. I added them to this same config profile, and I think they're correct.
- Will they work if they're installed before the app is?
I believe these work for Big Sur. However, I've noticed, specifically, Catalina doesn't add the one program to Full Disk Access and you end up needing to search for it. Of note, that program is in the PPPC as "com.fortinet.forticlient.macos.antivirus" instead of the filepath. I suspect this is fine, but I don't know.
Sorry, I know this is a lot, but I want to make sure I'm not missing something, especially since I've never worked with these functions of configuration profiles before. Specifically the System Extensions and the Privacy settings.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-14-2022 02:48 AM
Hi guys
here are the configuratios, which are working for me
except the PPPC settings, which are not working on the new m1 MacBooks with monterey. I am awaiting some help from our security partner or Forti as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2022 01:05 AM
Hi,
First, forget about version 7.0.2 and take the latest release 7.0.3. In the latest release a lot issues from 7.0.2 are solved. Also on the M1 MacBooks and for Monterey.
I'm in the process right now to finish the configuration profiles. The only one i am missing is the network extension.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2022 07:34 AM
Can you post your config profile when done? I need to set this up as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2022 08:38 AM
I was unaware 7.0.3 is out now. I'll look into that. I agree with @kryan though, if you get your configs figured out would you mind posting them?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2022 06:51 AM
any luck with the config profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-06-2022 01:03 PM
@Jacek_ADC& anyone else who may be able to help
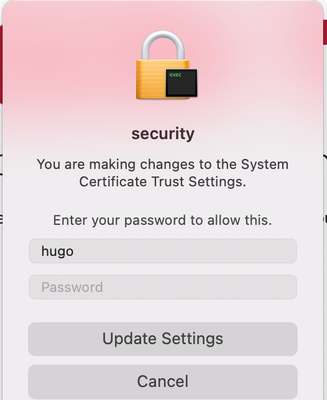
Hello, on 7.0.3 now, I've added the Certificate to a configuration profile but I still get this pop-up, is this apart of the post-install script? How did you resolve this pop-up? I can't seem to dial it in.
Looking for a Jamf Managed Service Provider? Look no further than Rocketman
________________
Virtual MacAdmins Monthly Meetup - First Friday, Every Month
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-14-2022 02:48 AM
Hi guys
here are the configuratios, which are working for me
except the PPPC settings, which are not working on the new m1 MacBooks with monterey. I am awaiting some help from our security partner or Forti as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-30-2022 12:04 PM
it's all works except for this any idea?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-30-2022 10:40 PM
Hi,
I just received an official statement from our partner which works with fortinet. So the statement from fortinet is, that no official way is possible to install fortinet without user interaction.
From my side I need to test everything once again. I just changed my enrollment script for the macbooks, so fortinet client will be installed after the jamf notify process after the restart. This works very fine. At the moment I wan't find any time for testing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-10-2023 03:19 AM
with updated EMS you should be able to export the certificate and deploy it via Jamf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-15-2022 12:22 PM
Hello,
Could you share with us where you got the details to create the configuration profiles? My company is about to start using FortiClient v7.0.5 and I can't find any information about how to create these profiles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-24-2022 03:59 AM
Are you able to update existing installs? that is the problem I'm having, when the client is installed it won't update
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-30-2022 10:43 PM
I never had issue until now to install the new client over the old one. This is the easiest way for us to upgrade the major versions without issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2022 09:26 AM - edited 08-31-2022 09:48 AM
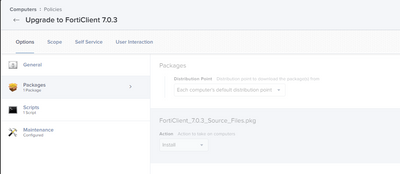
We have in-place upgrade issues as well. We're using the free version. What I've found is that you need to run the uninstaller for the previous version first, then install the new one. I've adapted the build workflow created by @mickl089 over in this thread. I package up the Forticlient .mpkg and the vpn.plist from a machine with the connection settings in composer, then I deliver the files to a temp directory and use the script to install (after) the package and connection settings:
#!/bin/bash
#James Mahalek, University of Calgary
#Stops all running FortiClient processes
killall FortiClientAgent
killall FortiClient
#Initiates silent uninstall of current Forticlient
/Applications/FortiClientUninstaller.app/Contents/Library/LaunchServices/com.fortinet.forticlient.uninstall_helper
#Run FortiClient 7.0.3 Installer
installer -verboseR -pkg "/private/tmp/FortiClient_7.0.3_Source_Files/FortiClient 7.0.3.mpkg" -target /
#Copy vpn.plist from tmp to FortiClient config folder
cp /private/tmp/FortiClient_7.0.3_Source_Files/vpn.plist "/Library/Application Support/Fortinet/FortiClient/conf/"
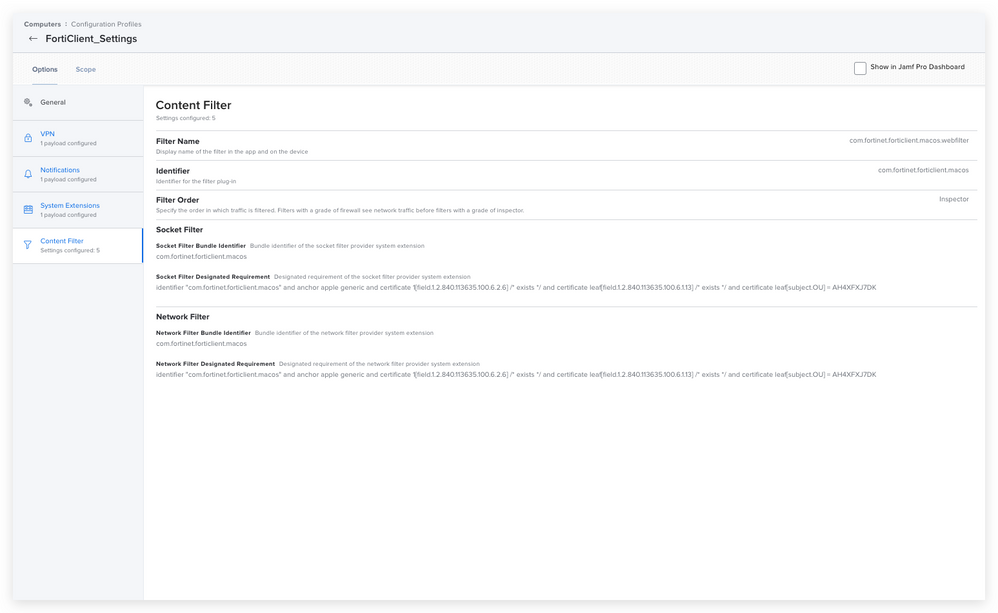
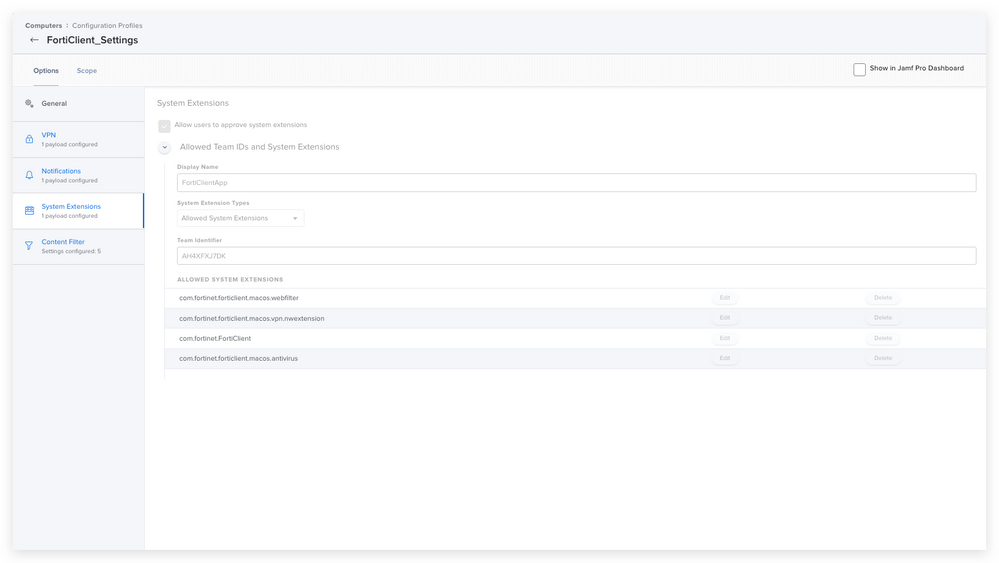
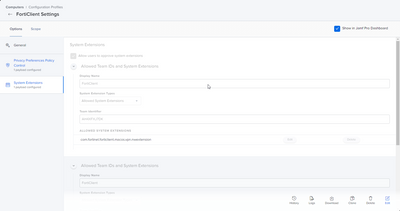
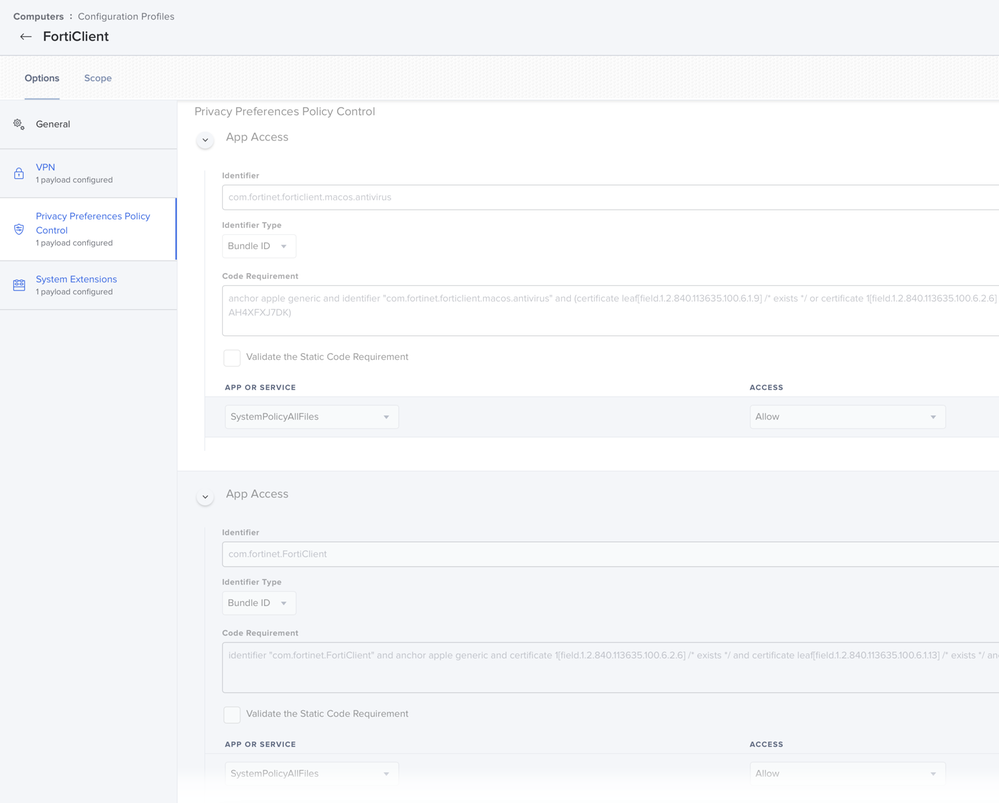
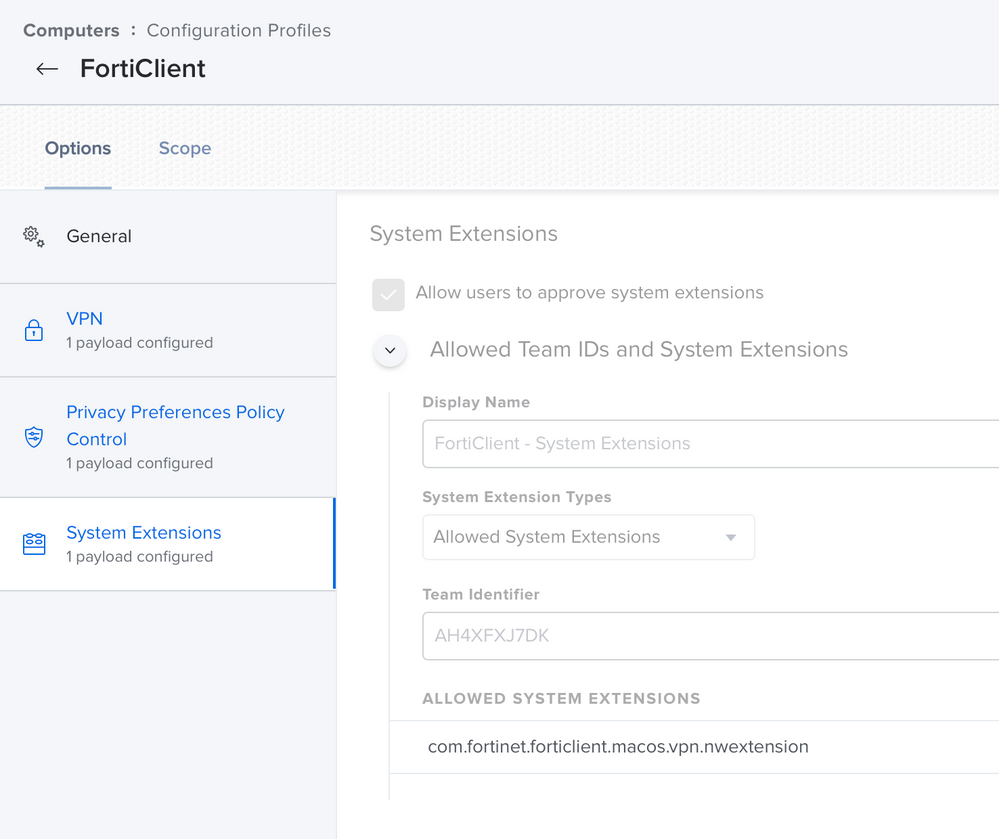
We also deploy the FortiClient settings for PPPC and System extensions to any device with FortiClient installed (hence the maintenance option in the install), and those are similar to the solution in the thread. We do use the free version, and only the VPN, so only the nwextension is necessary (see below). hint: One can use the following command in terminal to derive the Team and Bundle IDs for the system extension if you ever have to create these for an app.
systemextensionsctl list
Also, don't forget the PPPC settings!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2022 02:32 PM
@Jacek_ADC thanks a ton for these screenshots, definitely helped me get started! Have you made any further progress since this implementation? Currently, I'm running into an issue where the profile is creating a whole new VPN config but upon pushing FortiClient 7.0.3 'install.mpkg', it creates a new VPN config and asking to 'Allow' FortiTray. Any thoughts on that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2022 10:35 PM
Hi, your welcome. I invested a lot of time for testing :)
At the moment I am waiting for the 7.0.6 version which should solve a lot of issues.
So for the moment I stopped testing and deploying the forticlient.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-24-2022 02:31 PM
I know this is a bit late, but would you recommend reaching out to FortiClient's support team? I have pre-packaged installers from them, but the settings do not seem to be embedded. It's like I might as well have gotten the installer from a direct link on their site. And the administrator's guide is not really accurate from what I've experienced. I sincerely appreciate any help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-05-2022 04:20 AM
going through same popup issue, any help ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-05-2022 02:48 PM
I put it together from the suggestions on this thread and this one:
https://community.jamf.com/t5/jamf-pro/quot-fortitray-quot-would-like-to-add-vpn-configurations/m-p/...
I only get the two pop-ups to install the certificates to the keychain. I tried to automate this but I could not figure it out, so we're gonna live with that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 11:01 AM - edited 08-12-2022 11:02 AM
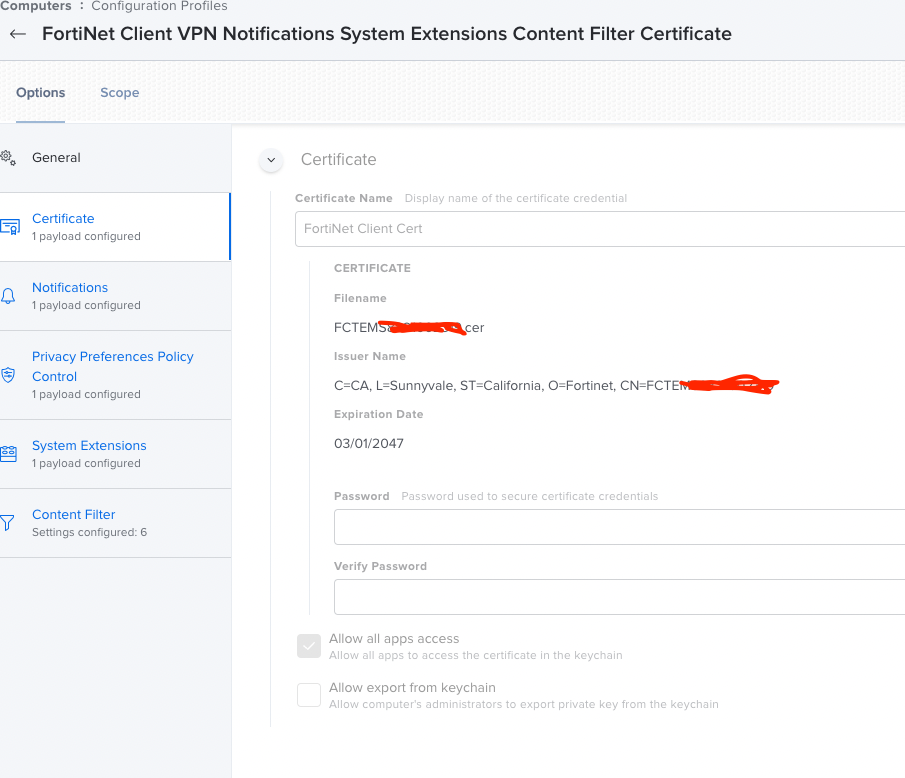
@JDaher , will be checking through your screenshots to see if it helps to setup the same way on my end, I did see you mentioned the certificate you need to manually install/receive prompts, I was actually able to automate this:
- Install FortiClient via DMG
- Export the FCTEXXXXXXXXXXXX.cer from Keychain Access Manager (make sure it's set to "Always Trust")
- Add/upload the cert via configuration profile and scope to the macs where FortiClient will be pushed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-21-2022 10:41 AM
Thanks. I tried this before and it didn't work for me, it didn't install the certificate. Also, in our case there are two certificates that need to be installed. Both go into Keychain > Login.
I may give this another try at some point. But right now I'm good with asking the users to approve the installation of the certificates. Thanks again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-27-2023 10:44 AM
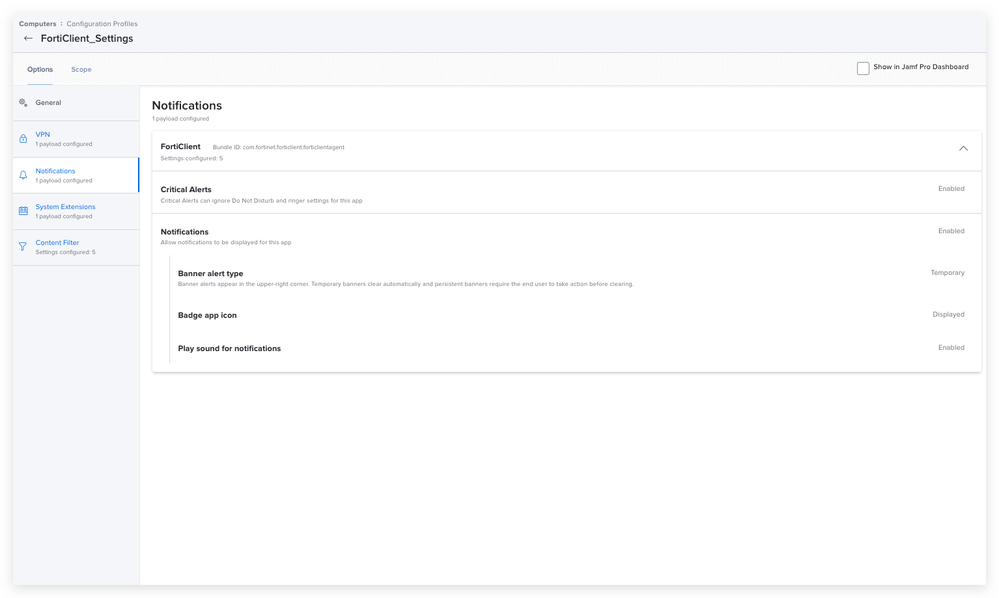
Can you tell me the Bundle ID you used for the Notifications payload here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-27-2023 10:54 AM
@kevin_v
com.fortinet.forticlient.forticlientagent
Looking for a Jamf Managed Service Provider? Look no further than Rocketman
________________
Virtual MacAdmins Monthly Meetup - First Friday, Every Month
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-27-2023 10:58 AM
Thank you. Seeing inconsistencies with people still getting the prompt to allow FortiClientAgent notifications, even with the config profile applied. Sounds like a Jamf PI or something though...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-06-2022 09:56 PM
Hi Guys
We are are already on 7.0.7 which has solved the dns resolving issue the client had since version 7.0.0
So we install the FortiClient on the machines in our prestage notify process. FortiClient is installed after the notify process is done and a few settings are done and triggered with a dummy file. This works flawless.
We have our own forti ems system and are starting now to testing the update procedure directly with the ems server and not with jamf.
I will test the next few days the setting with the certificate and the added pppc keys in this thread and will inform you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-21-2022 06:03 AM
Did you have any issues with allowing full disk access to it with PPPC, Ive tried but it doesnt seem to be working on my m1s
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-21-2022 10:35 AM
I set up full disk access using the PPPC payload in the configuration profile in Jamf, and that works for me. See the screenshot I posted here on 8/5
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2022 10:52 AM - edited 09-21-2022 10:53 AM
I assume the config profile is installing? Maybe check your identifiers and code signatures for errors, and remember to add in an identifier and code signature pair for fctservctl2, as well. Example here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-28-2022 12:24 PM
I am currently working on this same thing
I see in the FortiClient 7.0.7 directory on the support site they have an intune and jamf .mobileconfig - has anyone tried simply importing that?
separate from that I was attempting to use fcconfig to import the config and despite it saying its "finished" it doesn't have it... https://community.fortinet.com/t5/Fortinet-Forum/Library-Application-Support-Fortinet-FortiClient-bi...
mobileconfig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-27-2023 01:56 PM
Yes, this worked best for me over making my own default VPN profile, PPPC, and extension allowance. (Initial install 648 from Jamf School, upgrading to 707 from EMS.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-14-2022 10:03 AM
Has anyone had any performance issues with 7.0.7.0245 on 12.6?
We're using Forticlient VPN free app versus the EMS version
Tunnel all versus split tunnel
Seems that as time progresses, latency grows on VPN (fine if disconnected) but only until you "shutdown" the app and re-open does it go back to the expected speed.
Has anyone else had that experience?
-Adam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-29-2022 06:27 AM
Fortinet has a Jamf mobile config for the Forticlient that you can download and import into Jamf. Check out their site where you download the Forticlient. Works perfectly.
Found it in Fortinet's Jamf Deployment guide.
To configure profiles on Jamf Pro:
Log in to Jamf Pro. Go to Computers > Configuration Profiles.
Download the FortiClient_<version.build>_macosx.Jamf.mobileconfig sample configuration profile file:
Go to Fortinet Services & Support > Firmware Images.
From the Select Product dropdown list, select FortiClientMac.
On the Download tab, go to FortiClientMac > Mac > v7.00 > 7.0. Select the latest FortiClient version.
Download the FortiClient_<version.build>_macosx.Jamf.mobileconfig sample configuration profile file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2023 05:45 AM
Just some infos from my side and testing.
So we are testing 7.2.0 now on our Macbooks with ventura.
It seems that the 7.0.7 and also the 7.2.0 not solved the dns resolving issue.
The licensing has also changed with the latest version on the ems itself.
So we tried also to use the config and the guide from Forti. But we wasn't able to use the guide from forti and i was not able to do the steps with the cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-27-2023 07:34 AM
Updated deployment guide
when I install during setup, it installs correctly. when I do it from self service, the pkg is blocked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-15-2023 04:39 AM
Hi all,
Any new regarding the FortiClient Agent prompt?
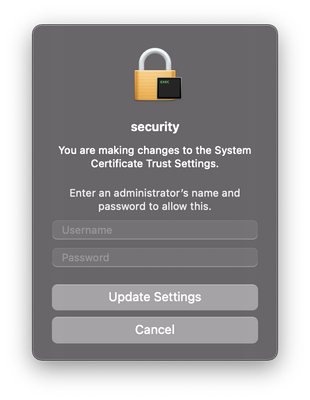
I have applied the config profile for macOS and everything is working as expected, but while the Intel macs install the app silently, the ARM ones get the "FortiClientAgent - You are making changes to the System Certificate Trust Settings" and asks for an admin authentication.
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-17-2023 12:28 PM
This is the same behavior we see. Not only do we see it when it first installs, but it also pops up from time to time. Our devices are currently on v7.0.7, but we just got the green light to upgrade to v7.2. I will build a new configuration profile using this document as a guide. It's a document upgraded this month: https://fortinetweb.s3.amazonaws.com/docs.fortinet.com/v2/attachments/139d51b8-9d11-11ed-8e6d-fa163e...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-27-2023 07:30 AM
Hi,
We managed to solve it in the meantime.
Our AV is Microsoft Defender, and we noticed, after several complaints of random URL blocks of our users, that the root cause was the FortiClient Web Filter.
We had already the MS Defender Web Filter active, and it seems it is not compatible with FortiClient.
Basically, after the Network team disabled it because of the issues reported above, I noticed that the prompts stopped appearing for both ARM and intel CPU devices.
We are still contacting FortiClient Support via ticket to validate if this makes any sense, but at least reporting for you guys, this might help..
Best regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-13-2024 01:53 AM
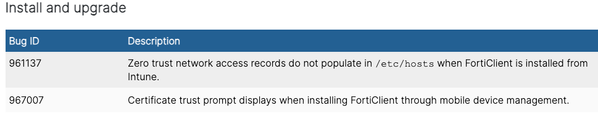
Regarding the certificate prompt... It looks like the issue is not there anymore with FortiClient 7.0.11. Please, see the documentation:
ref. https://docs.fortinet.com/document/forticlient/7.0.11/macos-release-notes/510031/resolved-issues
We did some testing since Friday and the issue didn't occur indeed so seems to be fixed.