- Jamf Nation Community
- Products
- Jamf Pro
- Re: Deploying Palo Alto Traps
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Deploying Palo Alto Traps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
05-15-2017
05:59 PM
- last edited on
03-04-2025
08:42 AM
by
![]() kh-richa_mig
kh-richa_mig
Hi guys,
Anyone know where is the plist for Traps Settings or way to set up the settings at all?
Been scanning for plist and any config file to set up the settings but couldnt find any.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-14-2017 11:26 AM
Palo Alto Traps For Mac is not like a standard application.
Here is where the Palo Alto Traps For Mac installs on the local computer:
However within Traps for Mac Client Agent, there are no static/local configurations. The specific location where there are configurations which is in config folder is synced with the Palo Alto Server that manages the client. So if you are updating these xml files, it will get over written when the Traps client checks in with the server. The only configurations that you can edit during installation time is the Palo Alto Traps Server address Traps Client should initially connect (server.xml) to which is located in the install zip file provided by the person that manage your Palo Alto Servers:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-08-2017 03:40 PM
Has anyone deployed this properly with JAMF?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-08-2017 08:08 PM
Yes, I have the Traps for Mac working with jamf. There are 2 options that you can use to deploy traps with jamf.
- Option 1 - Create a custom package that lays down the installer, .version file, and custom xml file (custom client settings to set traps server addresses) in a static location on the clients computer along with a postinstall script that runs the install via the command line then put this into a policy.
- Option 2 - Create policy with the following
- a custom package that lays lays down the installer, .version file, and custom xml file (custom client settings to set traps server addresses) in a static location on the clients computer
- script that triggers the install via the command line
I prefer the pkg with postinstall script because if we have to manually install traps, the experience is the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-09-2017 11:37 AM
Thought I would add to my original response since I had to make documentation for my company on how to build this installer:
Prerequisites
- Traps for Mac Installer from console. Usually comes in a ZIP file.
- Custom XML file provided by Traps Administrator with organization server addresses in xml format
Process
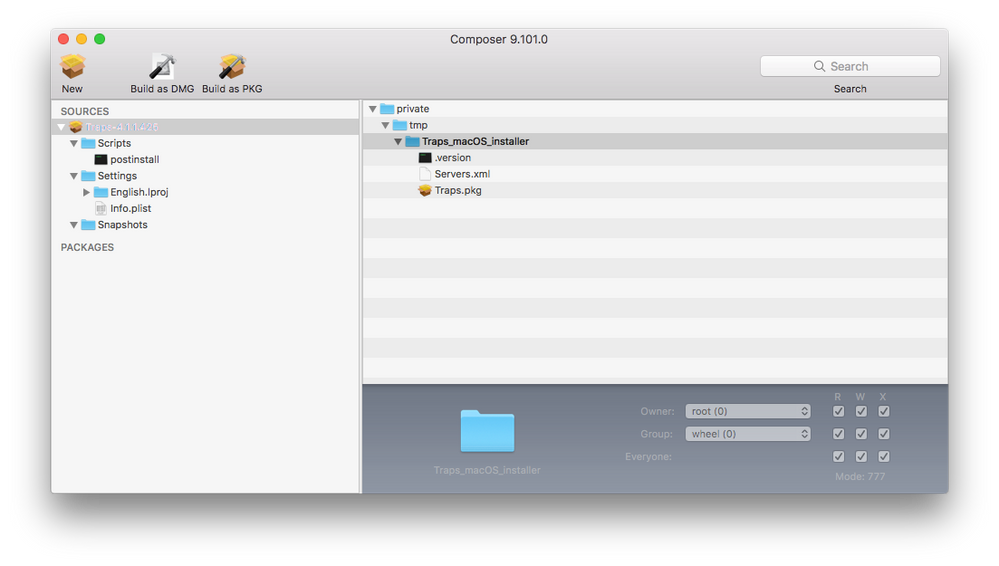
1. Place Traps installer, .version, xml file in a folder named Traps_macOS_installer and move folder to a temporary location on your computer. I usually use /tmp (/private/tmp). This way it will be removed at next restart.
2. Open Composer.
3. Create a new package by dragging and droping the Traps folder located in your temporary location into composer.
4. Go to the Scripts folder within your new Traps Source Package in Composer and create a postinstall script.
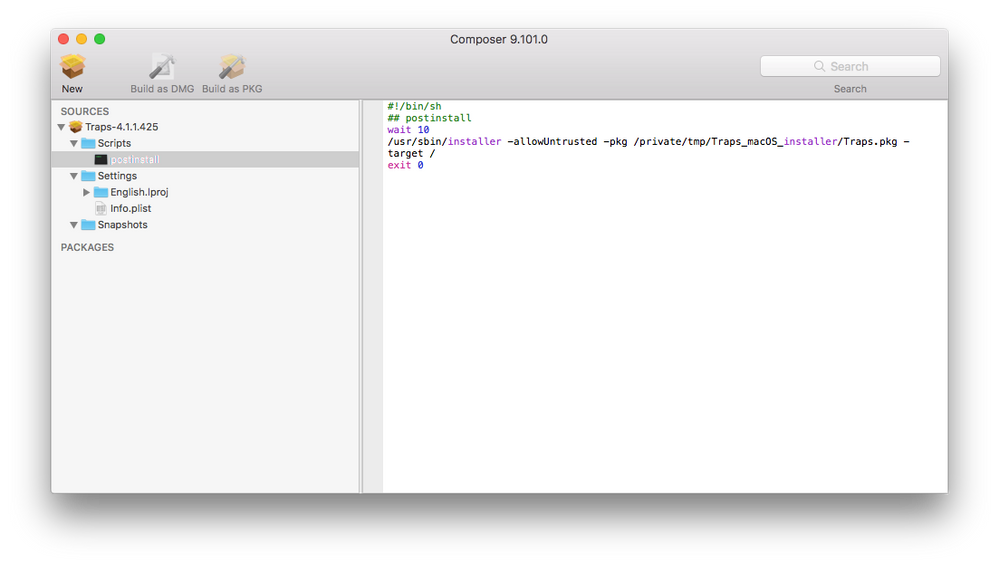
- Enter the following as shown in screenshot:
#!/bin/sh
## postinstall
wait 10
/usr/sbin/installer -allowUntrusted -pkg /private/tmp/Traps_macOS_installer/Traps.pkg -target /
exit 05. Build as PKG file since you have setup the postinstall script other wise the script will be stripped from the compiled installer/dmg.
Note: As long as you keep the Traps_macOS_installer consistant and all the file names are the same then you will just need to updated the .version file and traps.pkg file and recompile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2022 04:15 PM
I know this is an old post, but I have been trying without success getting the Composer created package to deploy. It seems that even though I have the package created exactly the same as yours in Composer (save for the filenames), Jamf is not deploying it to the /private/tmp/ folder, plus the script is erroring out stating that the Certificate is untrusted, to use the -allowUntrusted flag in the script...I absolutely am using it in the postinstall script!
Jamf support sent my ticket to their engineers, but I figured you folks might have some ideas for me to try in the mean time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2022 08:22 PM
Save yourself the trouble and just upload the zip file right into Jamf Pro / Jamf Admin. No need to package, it will just work as is. The zip file contains a package and your company config. Add the zip file like you would a package to your policy and you're done.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-18-2022 09:12 AM
I tried that and for some reason the install still failed. What I ended up doing was making a DMG file in Composer and adding the postinstall script (as a script in Jamf Pro) to run after things were copied to the endpoint. That worked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-18-2022 02:54 PM
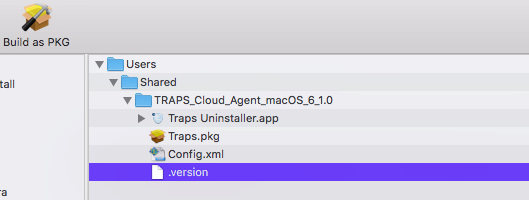
Depends on the failure I guess. Your admin should have supplied a zip with these files:
Config.xml
Cortex XDR Uninstaller
Cortex XDR.pkg
The zip deployment has worked for us without issue, so might be other factors at play. I would review the deployment guide top to bottom, including any changes to config profiles and the various different considerations for macOS versions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-18-2022 03:02 PM
I've uploaded the zip as is using Jamf Admin and deployed it out in my policy. Installs just fine. I should note that I'm using the signed Unified Configuration Profile that the vendor provided. That's deployed to all my Macs before I deploy out the package.
Only weirdness I'm seeing is after Cortex v7.6 is installed a couple days later it get's disabled somehow and the network content filter prevents Cisco AnyConnect from connecting to VPN. My Security Team has opened a ticket with the vendor on it. I should say that if I move Cortex.app from Applications to the Trash it unloads all the System Extensions disabling the Network Content Filter and AnyConnect works without issues. Seen this on 3 Macs so far on Jamf Pro Cloud server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-19-2022 12:21 AM
We also have some issue's with Cortex 7.5.1 and even the lastest 7.6.0
Cortex deploying to the machine works fine and also we use the unified configuration policy to the machine. But... on INtel machines no problems only on the new M! pro/max machines all internet connections will be blocked by the Cortex Network filter.
Strange thing is when we reboot with wifi enabled and only Ethernet connected the internet works fine. After enabling Wifi the connection still works but somehow the ethernet adapter will switch to 169.254.x.x. address and even the wifi connection will be enabled but no internet connection at that time.
Did some several tests and found out that a complete new machine with no mdm enrollment also has this same problem.
We contacted the vendor and they also did a remote desktop session to see what happens.... But the problem still exists for almost 5 weeks now after sending spindumps and complete log files.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-18-2022 03:17 PM
Yep, was using the zip file that had those three files and a hidden 4th file, version.xml I believe. I also used all of the configuration profiles from the vendor...It would install, but wouldn't catch the config file, so Cortex was greyed out. Once I made it into a DMG with a separate script to launch the installer, then it worked. I was even using all the same files from the zip.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-09-2017 02:36 PM
Thank you so much! I was almost on the right track to do so with packages.app instead of composer. I didn't think about using Composer in this way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-11-2017 12:39 PM
@matin Thanks for sharing, worked perfectly and saved me some time!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-28-2018 10:23 AM
Such a good post. Thanks man.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2018 09:18 AM
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-17-2018 10:28 AM
Hey,
Thanks so much for this article, its super helpful. Where do I find the .version file? Also is Config.xml the new Server.xml?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-17-2018 02:55 PM
The following files are create from the Traps Console. Unfortunately, I do not have access and these files are provided to me by my IT Security Team:
- .version
- Servers.xml
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-31-2018 02:01 PM
Thank you @matin ! Issue right now is that Gatekeeper seems to be preventing the extension from running, which borks the install initially. Do you have any advice on how to disable or enable this app from running in Gatekeeper? A little cloudy on the process.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-11-2018 10:06 AM
@mm13 - I think you are referring to User Approved Kernel Extension Loading. My company has a hybrid of mac hardware that have been imaged via Apple DEP and QuickAdd/Jamf Imaging. We manually authorize the User Approved Kernel Extension via Security and Privacy > General tab and manually approve the User Approved MDM via profiles. For Apple DEP and Jamf 10, we are whitelisting these Kernel Extension via Configuration Profile. Hope that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-15-2018 04:38 PM
thanks @matin you have saved me a whole load of time ! much appreciated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-07-2018 01:32 PM
@matin Thank you for all your information. It's been a great deal of help. I did get stuck on the Kernel Extension via Configuration Profile. I did look at the links you provided, however, I can't seem to figure out how to create the profile and upload it into Jamf. We are not using a Mac Server. I do apologize since I'm really new to Jamf and Apple products in general.
All the documentation I've been reading through referred to using Profile Manager, which, appears to only be available on MacOS Server? Any tips you have will be helpful. FYI, I created a package following your instruction above and found that it would download locally to the Mac, however, never installed. Again, I suspect that the Kernel Extension Loading is what prevented that, even though nothing prompted about allowing it. In the private mp folder I see it there, however, it has a red circle with a line in the circle (similar to a hyphen).
Whatever help you can lend will be greatly appreciated. Thanks again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-07-2018 11:34 PM
@bcbackes - If you are using jamf (like I am), you would use the built in options to create a white list configuration profile in Jamf as described by @rtrouton article Whitelisting third-party kernel extensions using profiles. You would need to scrolling down the bottom of the article on how to create one in Jamf Pro.
Note, You must be running Jamf Pro 10.3.1 or higher I think for these configuration profile options to be available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-15-2018 06:50 PM
Thanks @matin ! That was my issue all along. I'm running Jamf Pro 10.0.0. We are in the process of migrating our server and updating Jamf, however, we are not there yet. I've just setup a DEV Server and installed the latest Jamf Pro 10.7.0. I found the "Approved Kernel Extensions" you were talking about. I'm excited to test this out. Thanks again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-25-2018 04:57 PM
@matin Hello, I'm running Jamf 10.7 and have setup the Kernel Extension via Configuration Profile. I followed your instructions above as well. Palo Traps does install automatically, however, it doesn't appear to have any of the server settings in it.
I did verify that the "Servers.xml" is present with the Traps.pkg and the version file. I did create the postinstall script using the settings below:
!/bin/sh
postinstall
wait 10
/usr/sbin/installer -allowUntrusted -pkg /private/tmp/Traps_macOS_installer/Traps.pkg -target /
exit 0
I've packaged this as a PKG using Composer and uploaded this to the Jamf DP. I created a Policy to deploy this to all computers (doing this in my Dev environment). It deploys out when the computer checks in, however, after it installs and I open the Traps Console, there isn't anything in there. If I try to check-in I get an error. I'm not sure what I'm missing. Any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-30-2018 03:08 PM
@bcbackes - Is the target client a DEP computer, user-enrolled computer or QuickAdd/Casper imaging client? Can you also verify that the target client MDM Profile is approved? This is required for the Kernel Approved Configuration Profile to deploy properly to macOS 10.13 or above clients. However, Traps for Mac install process sounds like all the components installed on the target system fine. Traps just cannot connect initially to the Traps Server. I would suggest trying the installation process on a 10.12 target client or below to verify the process.
Note, We are still utilizing the process that I wrote out in this document for 10.13 however we had to add Palo Alto to the kernel white list. Note, after the initial installation the client may require a restart.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-20-2018 06:35 PM
Just to follow up with everyone. I did get Traps to install correctly and contain all our server information. I've even tested using @matin's suggestion on making the package name generic (versionless). Then, I drop in the new pkg, save it in Composer, then, upload it using Jamf Admin. I've deployed out newer versions to existing installations and found that they upgrade without issues. I've even created an uninstaller that seems to work just fine.
Thanks for all the help!!! This was my first successful package that I've created in Composer!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-25-2019 06:16 AM
EDIT- Nevermind I just noticed it was a hidden file!
Hi Everyone,
So our zip folder does not contain a .version can anyone confirm this is the new normal with version 5 or am I missing something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-31-2019 12:23 PM
So I was struggling in just about every way to get this working. Both using composer and also the solution shared by Martin.
I decided to get have a zoom meeting with Palo Alto and wanted to share my findings and what got it working for me so others don't go through my pain.
Anywho, I am not sure if its a new thing or what, but you can literally drag the Zip file into JAMF Admin and create a new policy to deploy the Zip. As long as you have the right whitelist information done its as smooth as any other deployment. Blew my mind it was that easy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-31-2019 05:52 PM
Oh wow, I came to this page after googling for Jamf palo alto traps and i was the OP.....
I managed to get it working and just couldnt remember this thread...
Here how i got it working.
FYI, this is for the Cloud version and should be the same as ESM Version.
Composer - Put the Installer under /Users/Shared
Post install Script
#!/bin/bash logFile="/Users/Shared/Traps_Install.log"Check for Log file
if [ -f $logFile ]; then echo "$(date)" >> $logFile echo "Log Present" >> $logFile else touch $logFile echo "$(date)" >> $logFile echo "Log file Created" >> $logFile fiInstall the package
echo "Installing Traps Package..." >> $logFile /usr/sbin/installer -pkg "/Users/Shared/TRAPS_Cloud_Agent_macOS_6_1.0/Traps.pkg" -target / echo "Package installed..." >> $logFileLaunch Traps Service
echo "launch Traps plist..." >> $logFile sudo launchctl load /Library/LaunchDaemons/com.paloaltonetworks.trapsd.plistRemove installer file
sudo rm -rf "/Users/Shared/TRAPS_Cloud_Agent_macOS_6_1.0" echo "deleting Traps folder" echo "complete" >> $logFile
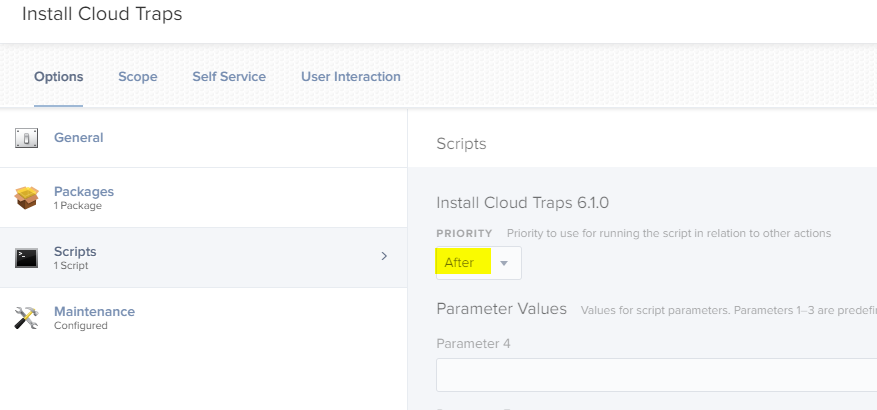
My Policy
Extension Attribute
#!/bin/bash if [ -f /Library/Application Support/PaloAltoNetworks/Traps/version.txt ]; then version=$(cat /Library/Application Support/PaloAltoNetworks/Traps/version.txt | tail -1) echo "<result>$version</result>" else echo "<result>Not Installed</result>" fi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
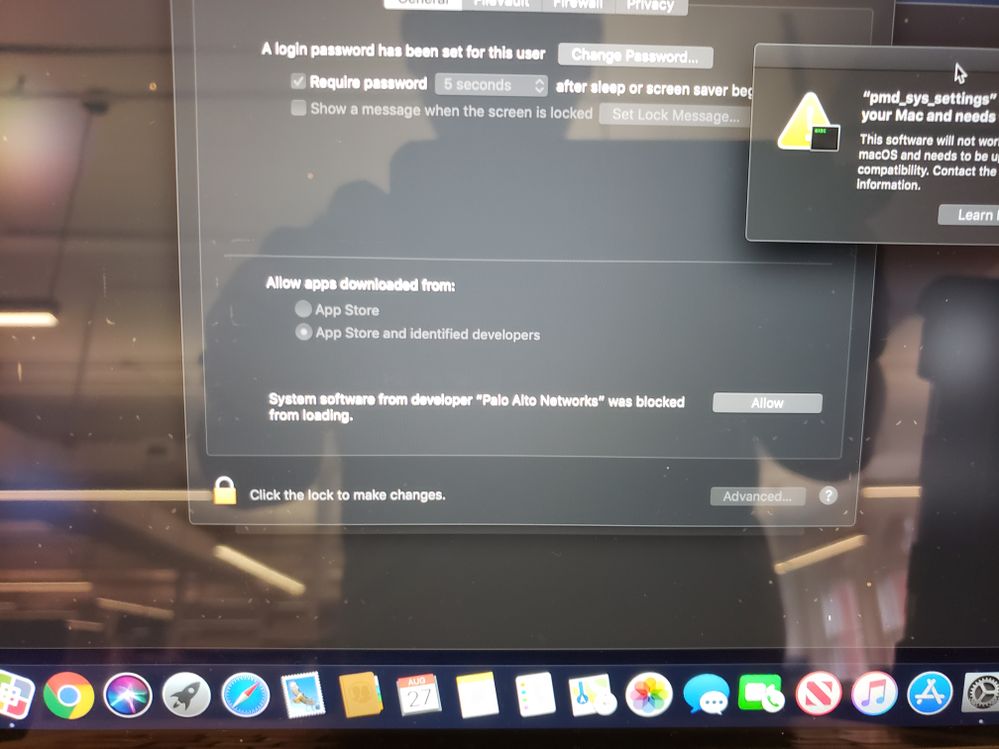
Posted on 08-27-2019 09:19 AM
Hi, just wanted to post in this thread to see if anyone was able to resolve the issue when deploying (using Matin's steps of making a custom package in Composer) and getting a System Extension blocked pop-up for Security & Privacy. It pops up and but still allows the install to take place. What am I doing wrong that causes the pop-up?
I have the below Configuration Profile payload for Approved Kernel Extensions that is pushed before I run the policy to install the software.
Approved Team ID
DISPLAY NAME
Palo Alto Traps
TEAM ID
PXPZ95SK77
Approved Kernel Extensions(Optional) Approve the following bundle IDs only
DISPLAY NAME KERNEL EXTENSION BUNDLE ID
com.paloaltonetworks.GlobalProtect.gplock
com.paloaltonetworks.GlobalProtect.gpsplit
com.paloaltonetworks.traps-agent
com.paloaltonetworks.kext.pangpd
com.paloaltonetworks.driver.kproc-ctrl
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-27-2019 09:30 AM
@villap5 Add Traps to an Approved Extensions Configuration Profile.
See this list for the Team ID and other information regarding Extensions.
https://docs.google.com/spreadsheets/d/1IWrbE8xiau4rU2mtXYji9vSPWDqb56luh0OhD5XS0AM/edit#gid=1070689416
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
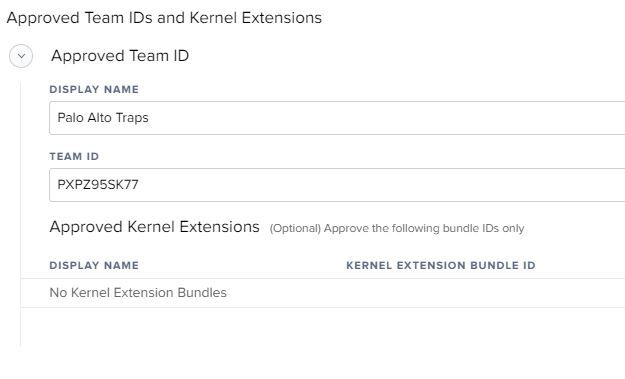
Posted on 09-25-2019 05:43 AM
@villap5 I only have the Team ID entered. I don't have anything listed under the Optional Bundle IDs. The Bundle IDs, I believe, would only allow those particular things. I've added a screenshot of my Config Profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-05-2019 02:09 PM
Has anyone been able to get a PPPC setup for Traps? When I tested our current policy on Catalina I had to approve installation of an extension and then "allow" notifications. I would like to avoid any need for user approval of the extenision and I want all users to get notifications from Traps by default
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-05-2019 02:13 PM
@cputnam My "Approved Kernel Extensions" Config Profile I used from Mojave works in Catalina. That includes Traps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-05-2019 04:42 PM
Thanks Redwings - I will compare your AKE to mine and see if there is something different.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-07-2020 10:05 PM
Has anyone done a Jamf upgrade or Palo Alto console agent upgrade to a machine sitting at loginwindow and see it fail? I'm seeing it fail and then the agent is removed altogether! Doesn't happen if a user is logged in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-08-2020 01:19 PM
@davidhiggs I've just tested this myself. Mac is running Mojave 10.14.6 and Traps 6.1.0. I made sure my Mac was at the login screen with no one else logged in. Added it to the scope for my new version package in QA (Cortex 7.0.2 - name change from Traps to Cortex). I used Jamf Remote to run a "sudo jamf policy" command to the Mac to kick it off. I checked the logs and it shows as installed. I confirmed that Cortex 7.0.2 installed successfully when I logged into the Mac.
Just so you know, I have my policy set to Reoccurring Checkin and Once Per Computer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-08-2020 07:13 PM
@bcbackes that's interesting, this is what i'm doing too. Are you dragging the agent update as is (zip file) into Jamf and deploying that? or repackaging as suggested above? I've done both and get the same result. macOS install.log has some information i'll be reviewing with Palo Alto soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-10-2020 06:39 AM
@davidhiggs I did repackage it with Composer. The reason for that is I'm moving the Uninstaller.app to a hidden location of my choosing so the average end user can't uninstall it. Here's what I'm doing:
- Unzip the contents. I place the entire unzipped content folder into the /tmp directory - with the exception of the Uninstaller.app.
- The Uninstaller.app I place in /var/folderIcreated for safe keeping.
- I pull those two things into my Composer package: the folder that contains the installer located in tmp and the uninstaller located in /var/folderIcreated.
- Package it up and load it into Jamf Admin.
- Create my policy and deploy it out.
This works like a charm for me. I suppose I could create a script to run afterwards that moves the Uninstaller.app to my desired location as well, however, I have everything right where I want it with this package and no need to create a script to run. Then for the next version I just go into composer and remove the old version files and place the new versions in there. Rinse and Repeat.
NOTE: I do change the ownership and permissions on the Uninstaller.app to Root:Wheel 754
Let me know if you have any questions.