- Jamf Nation Community
- Products
- Jamf Pro
- Deploying Palo Alto Traps
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Deploying Palo Alto Traps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
05-15-2017
05:59 PM
- last edited
a month ago
by
![]() kh-richa_mig
kh-richa_mig
Hi guys,
Anyone know where is the plist for Traps Settings or way to set up the settings at all?
Been scanning for plist and any config file to set up the settings but couldnt find any.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-16-2020 10:48 AM
@bcbackes , @matin or anyone , do you know how to remove the notification so it won't be displayed after successful installation? I'm using newer version of Traps. I'm using Composer and Configuration Profile to Approve Kernel Extension
update : Fixed using https://github.com/Jamf-Custom-Profile-Schemas/jamf-manifests/blob/master/macOS%20Notifications%20(com.apple.notificationsettings).json , thanks @talkingmoose
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-16-2020 01:43 PM
@cbanfield0818 dragging the zip file straight to Admin worked like a charm.
I've been deploying to Catalina machines and I have the Configuration profile to allow Palo extension and another config profile to allow Full Disk Access for Authorized, pmd, and trapsd.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-28-2020 12:32 AM
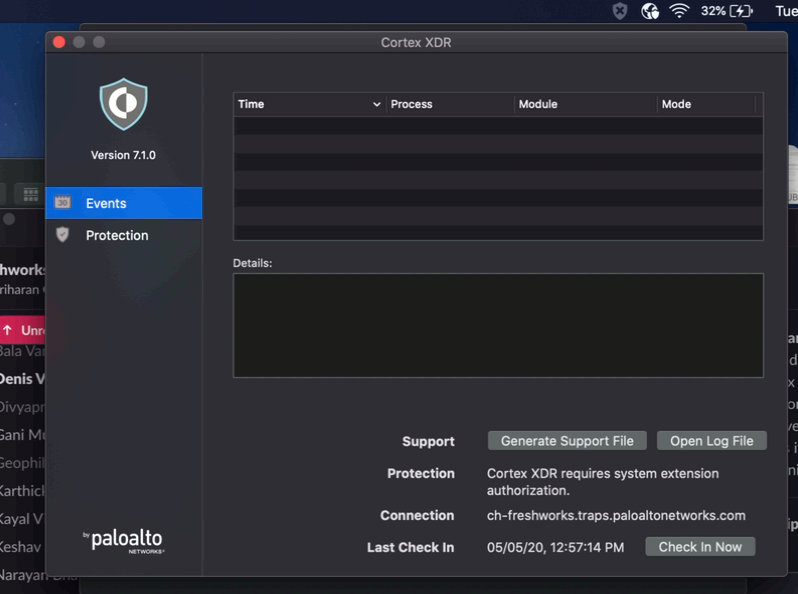
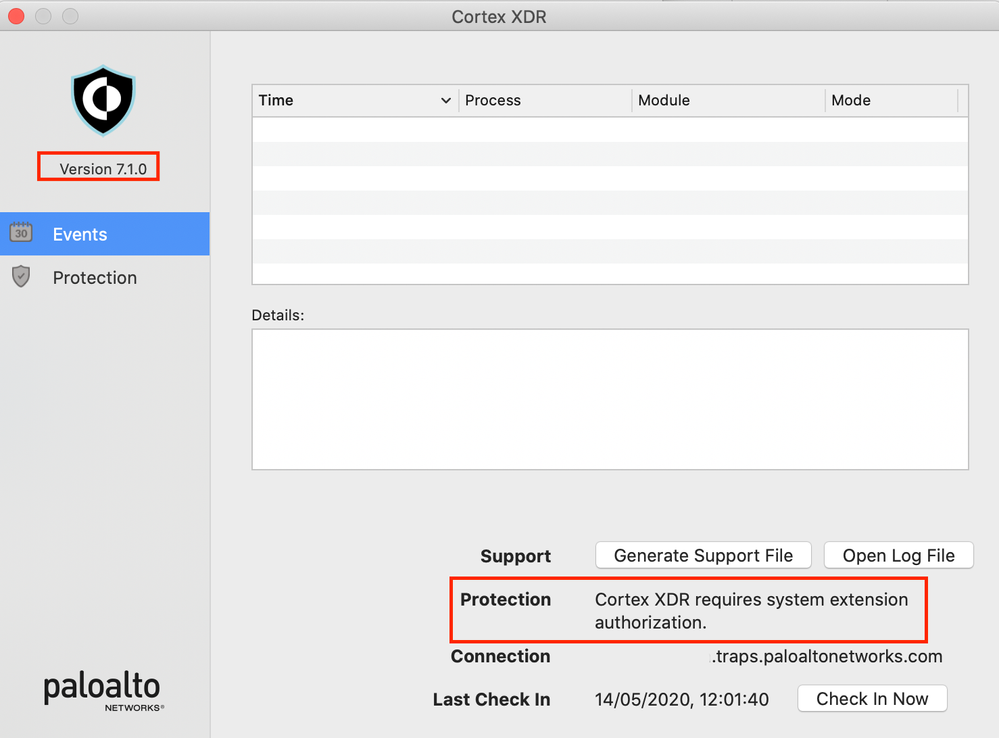
@bcbackes Looks like I hit a known issue, addressed with v7.1.0. I'm about to test and see if it's fixed.
Heads up for everyone else - major changes in 7.1.0. New system extension approval needed and changes to PPPC, I assume no more kernel extension. Make sure you have these in place before pushing the update. They even have a Jamf deployment guide now: https://docs.paloaltonetworks.com/cortex/cortex-xdr/7-1/cortex-xdr-agent-admin/cortex-xdr-agent-for-...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-28-2020 01:02 AM
Also, anyone that wants to use a Patch definition, I've got one in Community Patch under macmacintosh. Because of recent changes since v4-6 in 7.x and 7.1.x, it needs an EA to lookups which of 3 agents might be installed on the system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2020 01:03 AM
Documentation on Palo Alto's page for 7.1.0 is wrong and missing full disk access for the system extension needed for macOS 10.15. Seems they have confused settings relevant for 10.14 and below and 10.15 and higher. Have fed this back for clarification.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2020 04:25 AM
In my office most of the users facing the same after upgrading into 7.1.0 it requires full disk access pop up for every time and i have read the PA support article https://docs.paloaltonetworks.com/cortex/cortex-xdr/7-0/cortex-xdr-agent-admin/cortex-xdr-agent-for-mac/install-the-cortex-xdr-agent-for-mac doing manually for the machines one by one, do we able to automate this process from JAMF?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2020 04:42 AM
@udhayakumar on that page, select v7.1 for newer info, but some of it is incorrect. What macOS versions are you deploying to?
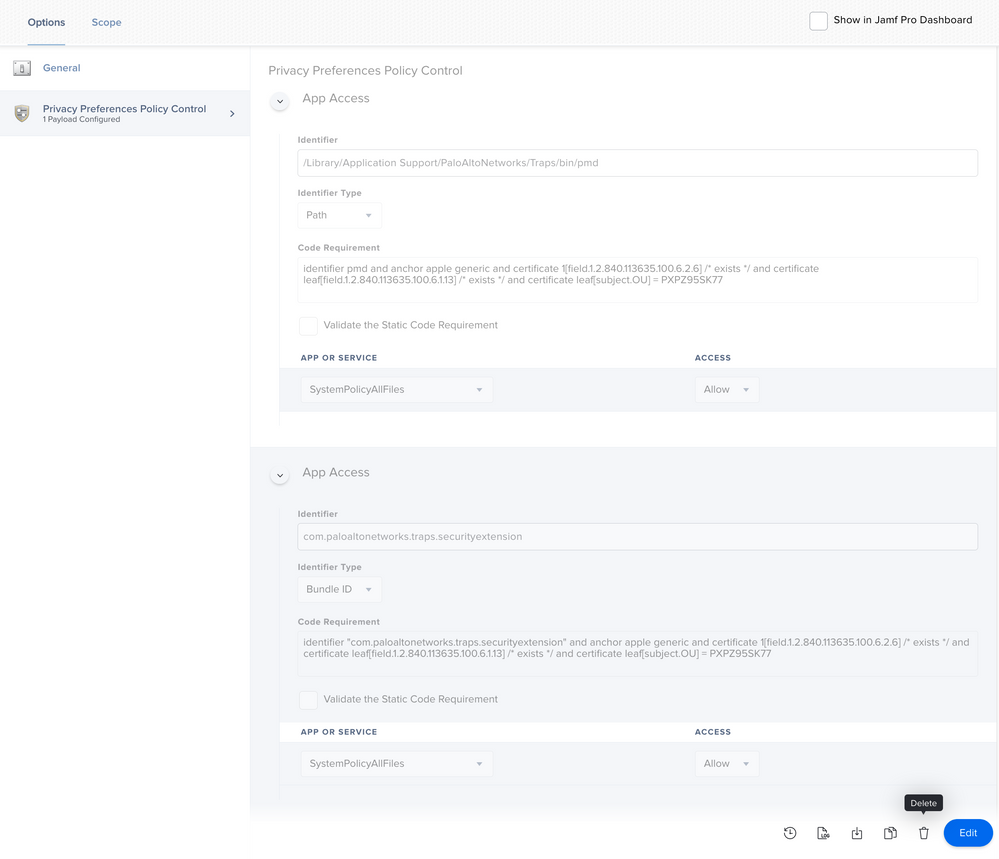
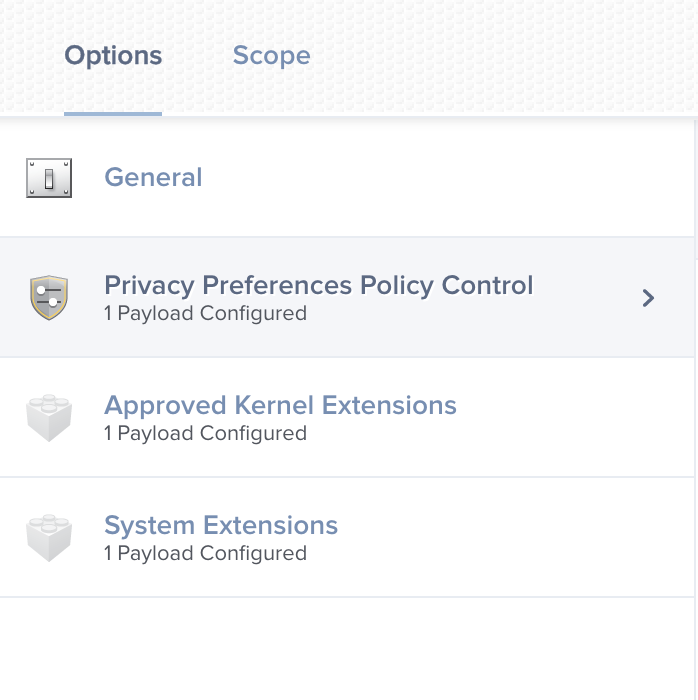
For macOS 10.15, the missing information is to add the following PPPC config profile:
Identifier:
com.paloaltonetworks.traps.securityextensionIdentifier Type: BundleID
Code Requirement:
identifier "com.paloaltonetworks.traps.securityextension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = PXPZ95SK77App or Service: SystemPolicyAllFiles, Access: Allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2020 07:12 PM
I haven't been using a PPPC at all. I still have my original KEXT for Traps deployed to my Macs and haven't ran into any issues with deploying out Cortex.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2020 11:23 PM
@bcbackes Seems strange to me if it's working on macOS 10.14+ as Full Disk Access is required for Traps/Cortex to work correctly, unless you're asking the user to add that permission in manually?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2020 11:30 PM
Hi David Higgs,
I have initiated the up-gradation from XDR portal directly to all the computers and on my org minimum users only having the Mac os 10.15 most of the peoples are in the older version only, so it will work all the Mac OS version right?
If I added in the securityextension in PPPC does it automatically allows the full disk access to everyone?
Regards,
Udhaya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2020 11:43 PM
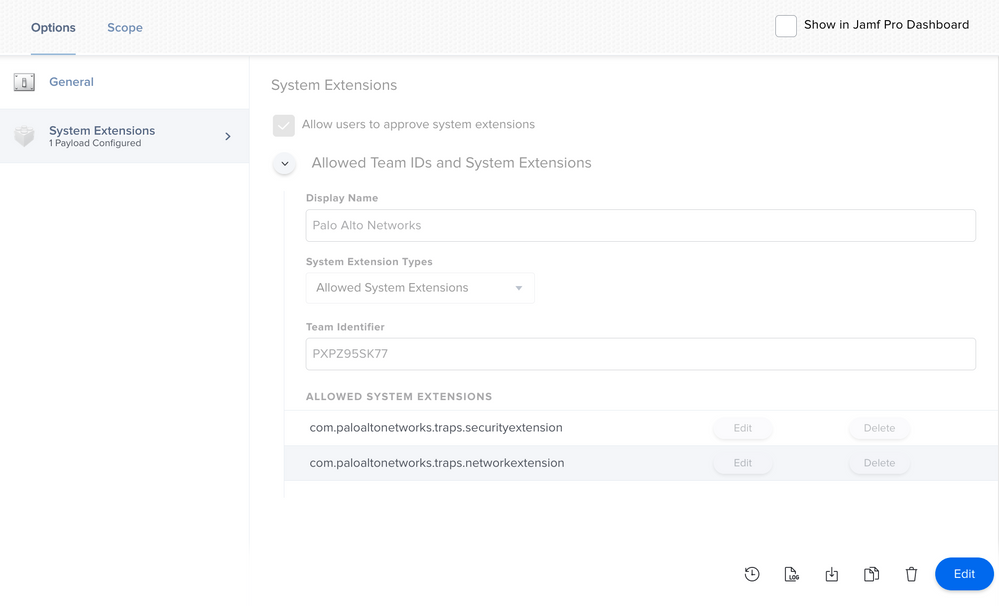
Add the System Extension config profile. I would scope to machines that are running 10.15+ and UAMDM is Yes.
Add the PPPC config profile. I would scope to machines that are running 10.15+ and UAMDM is Yes.
The setup for macOS 10.14 will be different so just keep that in mind Palo Alto haven't made it clear what those settings are, but I would use the information for 6.1.x or 7.0.x. Those settings should still work in addition to what i detailed above. Cortex may fix itself on macOS 10.15 if you've already deployed 7.1.0, I haven't tested that yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2020 11:51 PM
@davidhiggs Thanks for your reply i have enabled all the above steps only i have to enable the security extensions. Let me add and try hopefully it will work.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2020 08:12 PM
After contacting support, they have corrected their page: https://docs.paloaltonetworks.com/cortex/cortex-xdr/7-1/cortex-xdr-agent-admin/cortex-xdr-agent-for-...
Be warned, the document has curly quotes in the config and this will cause a failure. Change to straight quotes. I found this in the section recently added for AppleEvents.
Supposedly this covers all macOS versions. The System Extension is only supported with macOS 10.15.4 and above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-04-2020 11:50 PM
@davidhiggs today I have upgraded the latest version to all the Mac users, but most of the users getting the error to allow the application manually but I have added the team ID already but. why its asking the user to allow the application manually? can you guide me on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-05-2020 12:05 AM
@udhayakumar You really need to follow that website carefully, and you should be ok. Here are notes I kept after discussions with Palo Alto and doing testing:
Kernel Extension Config Profile
macOS 10.14.6 - 10.15.3 - Needed
macOS 10.15.4+ - Not needed
Note: Kernel extension can be whitelisted for macOS 10.14.6-10.15.3 with UAMDM approved. You could include 10.15.4+ and it should be harmless.
System Extension Config Profile
macOS 10.14.6 - 10.15.3 - Not needed
macOS 10.15.4+ - Needed
Note: System extension can be whitelisted for macOS 10.15.4 with UAMDM approved. You could include 10.15+ and it should be harmless.
PPPC Config Profile
macOS 10.14.6-10.15.x - Needs PPPC whitelisting.
Note: The System Extension and ‘pmd’ daemon need full disk access. The agent needs full disk access and AppleEvent permissions.
Retiring old PPPC Config Profile
When Palo Alto Traps/Cortex is upgraded to 7.1.0, you do not need whitelisting for ‘trapsd’ and ‘authorized’, but they are still needed if the machine hasn’t upgraded yet. To get around this issue, create a Smart Group which includes machines running 7.1.0 or higher. Add this as an the exclusion to your old PPPC config profile.
Eventually the number of machines using this config profile should reduce greatly. Will need to retire this config profile at some point.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-05-2020 06:01 AM
@davidhiggs if I have a common PPPC configuration for all the versions does harm the laptop? also now i am upgrading the cortex version from 7.0.1,7.0.2 to 7.1.0, in this, the cortex is again asking to allow the application manually. The Team id and Buddle ID i have updated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-05-2020 07:22 PM
You're missing Step 4 from the Palo Alto article for deploying v7.1.0, which is PPPC. You need this. No harm to the computer, just deploy to your problem/testing machine first to make sure you've got it setup correctly. Feel free to reach me on @macmacintosh on MacAdmins Slack if you still get stuck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-07-2020 10:36 PM
@davidhiggs If I apply the configuration changes now, do all the machines get enabled automatically, and also if all the exiting installed machines if the cortex is disabled does it get enabled automatically?
The configuration I created all in a single configuration only does this create any issues?
Regards,
Udhaya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2020 12:42 AM
@davidhiggs Can you help me on this, I can't able to reach you in slack.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2020 11:39 AM
test comment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2020 06:50 PM
@udhayakumar you can include in one config profile no problem. the config on their page has now been correctly updated, so please check again for any issues: https://docs.paloaltonetworks.com/cortex/cortex-xdr/7-1/cortex-xdr-agent-admin/cortex-xdr-agent-for-mac/install-the-cortex-xdr-agent-for-mac-using-jamf.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-14-2020 11:50 PM
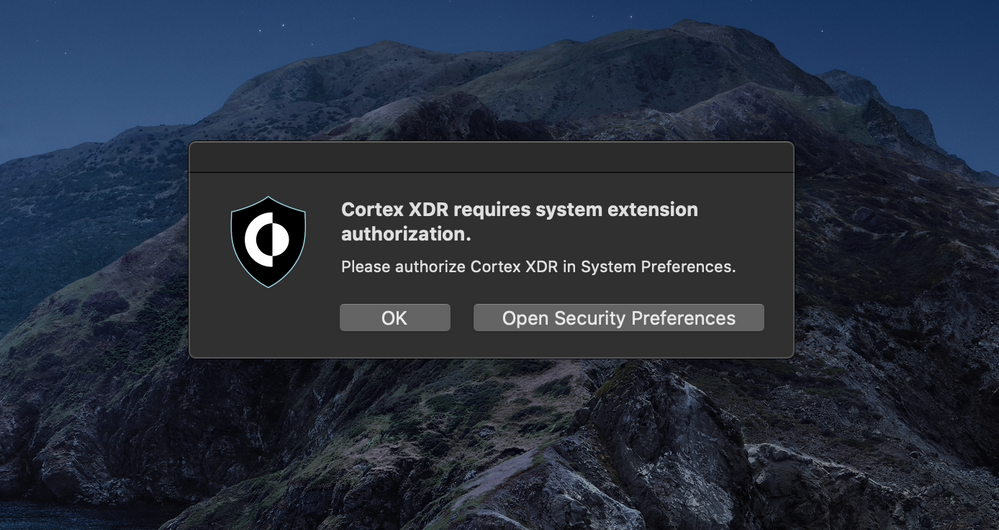
@davidhiggs When i deploy the 7.02 version with this configuration policy settings everthing works fine. But when we push the new update to 7.1.0 we get the following extension block.
Before this update everything was set to enabled and seems working fine.
Do you know if 7.1.0 needs more authorization.
The config policy works ok on 7.0.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-15-2020 12:10 AM
@Rappange Indeed it does. the move from 7.1 from 7.0.x was bigger than the change from 6.1.x to 7.0.x.
I'd take a fresh look at the new config requirements. Since 7.1.0 they now include information for Jamf setup on their website. go here: https://docs.paloaltonetworks.com/cortex/cortex-xdr/7-1/cortex-xdr-agent-admin/cortex-xdr-agent-for-...
They don't detail what's changed for each OS, but if you read above you'll see my own breakdown after some testing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-15-2020 12:13 AM
I created the Configuration Policy as described but somehow it keeps blocking and its driving me nuts :D.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-25-2020 07:58 AM
I have the same issue with the version 7.1.0 -- Cortex XDR requires system extension authorization. Also, I investigated that the application v. 7.02 has kproc_ctrl.kext in the /Library/Extensions/ folder. Now the app v.7.1 hasn't it, but we have two newest kexts bundles: com.paloaltonetworks.traps.securityextension and com.paloaltonetworks.traps.networkextension. However, I can't understand where the bundles are located
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-25-2020 05:51 PM
@osokhan They aren't kext bundles and not treated the same. You'll be adding them as system extensions via their bundleid so location won't matter. But if you're interested, they're inside the application in /Applications. If you follow the v7.1 guide linked above, you'll have no troubles. I've verified the original errors have been fixed by Palo Alto and working correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-27-2020 02:13 AM
I have followed the guide, and while it has worked for most endpoints, and all the tests I have made on a recently wiped machine, we are still facing issues in some cases, for example, when upgrading to Cortex to 7.1 from a previous version or upgrading from Mojave to Catalina: it is still prompting to allow the system extension.
I have triple checked the guide, created a separate profile with all payloads in a single config profile to apply to the affected machines, and still nothing, the prompt will not go away until manually approved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-27-2020 02:25 AM
@JBauza interesting to hear, I haven’t seen this in my small testing and deployment so far. I do have a concern with machines upgrading to Catalina from Mojave, I believe there are some race conditions to be mindful of in that scenario when it comes to config profiles. If I have some time I’ll do a test with a clean Mojave machine with 7.0.2, upgrade to 7.1.0 then upgrade to Catalina.
I am currently investigating a very small number of machines that seem to be causing the machine slow down or lock up, I think this might be due to kext cache issues but still very early to tell at this stage.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-27-2020 05:56 AM
I will try a couple of more things, but I will most likely end up contacting PaloAlto support.
If it can be of interest, all issues we've seen have been on Catalina machines, it's been working fine for Mojave.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-27-2020 06:15 AM
I tried to install the Cortex 7.1 with the profile based on the Palo Alto manual (https://docs.paloaltonetworks.com/cortex/cortex-xdr/7-1/cortex-xdr-agent-admin/cortex-xdr-agent-for-mac/install-the-cortex-xdr-agent-for-mac-using-jamf.html#install-the-cortex-xdr-agent-using-jamf), but I am still in need to allow the system extensions. I hadn't had the macOS 10.15 Catalina upgrade from 10.14. However, I made the uninstall v.7.0.2 before attempts at v.7.1 installation. I made recreation of the profile a few times, but the manual doesn't work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-28-2020 06:18 AM
We have pushed the Cortex 7.1.1 update on one of the affected machines, and it has solved the issue. Everything in Jamf is configured as per PaloAlto's procedure (https://docs.paloaltonetworks.com/cortex/cortex-xdr/7-1/cortex-xdr-agent-admin/cortex-xdr-agent-for-mac/install-the-cortex-xdr-agent-for-mac-using-jamf.html)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-28-2020 08:25 AM
The new agent came out. 7.1.1 today! Looks like the update resolved the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-28-2020 05:22 PM
Great to hear! I didn't see any bug fixes in the release notes, I wonder if deployment of an updated systemextension reset the issues some of you were having. I'll be pushing 7.1.1 too just in case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-04-2020 08:30 AM
Hello guys, can you help me with one problem? I successfully managed to create pkg and all privacy extensions in profiles. But I am unable to deploy this pkg to mac os. When I manually install this pkg on mac it perfectly installs and load config. But when deployed - it shows no error but won't install at all. Other pkg deploy works fine.
Thank you for help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-22-2020 09:45 PM
Hi @user-kVZEFdADCC Download a zip file from the Cortex portal and upload the ZIP file to create a package. And then you can scope it to a device and check.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-06-2021 07:05 AM
Does someone have a macOS kernel panic -- mac is crashing after wake up from sleep? The Cortex XDR is 7.2.2 which includes the Cortex XDR network interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-10-2021 05:48 PM
Hi @osokhan
yes we have also faced this issue and we have reached out PA support team and they suggested we upgrade the OS to 11.1. But it's not easy to upgrade the OS like that so there is another workaround is available so please raise a ticket to the PA team they will give you the Jason file to disable the Network Extension permission from Cortex end.
We identified there is an issue with Apple Mac network extension. The issue is not completely fixed in the 7.2.2 and it only provides a partial fix. Apple is working on to fix the issue(it is an apply code issue, not our XDR code issue) and the target version is macOS 11.1(which is still in beta). To workaround the issue for now, please disable the Cortex network preference for the time being.
The Bug ID is CPATR-11830 which you could track in the release note in the future.
Thank you and Best regards,
Regards,
Udhaya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-21-2021 05:23 PM
Hello Here and @davidhiggs
Does anyone tested for M1 Mac's because i have applied a config profile to allow the bundle ID to Approve Kernal but it's not working we have to enable it manually for the application to be enabled? did anyone faced such an issue, does anyone have the solution.
Regards,
Udhaya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-21-2021 06:17 PM
@udhayakumar Don't have an M1 to see. Kext shouldn't be used or needed? Should all be system extensions from now on. It's possible the installer isn't smart enough to stop it being put on the system though. Even if the kext was still used, Palo Alto would have to recompile it for ARM (I doubt they will) and you would also have to enable kext loading from recovery too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-21-2021 09:09 PM
@udhayakumar just got my hands on an M1. No issues installing 7.2.2 with the same config profiles I was using for Big Sur/Intel machines. No kproc_ctl.kext installed to /Traps/bin folder that I can see