- Jamf Nation Community
- Products
- Jamf Pro
- Re: Deploying Thycotic Privilege Manager 10.8.19
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Deploying Thycotic Privilege Manager 10.8.19
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-10-2020 09:38 AM
Vendor-provided Overview
Thycotic Privilege Manager is an endpoint least privilege and application control solution for Windows and Macs, capable of supporting enterprises and fast-growing organizations at scale. The two major components are Local Security and Application Control. Using Privilege Manager, administrators can automatically discover local administrator privileges and enforce the principle of least privilege through policy-driven actions. Those policy-driven actions include: - blocking, elevating, monitoring, allowing - application quarantine, sandbox, and isolation, - application privilege elevation, and - endpoint monitoring Continue reading … See also Privilege Manager 10.8 Customer Demo
macOS Agent Installation
Agent installation is well documented and straight forward, however "it will take 15-30 minutes for newly installed agents to register in Privilege Manager." (As of this writing, the vendor's link to Terminal Commands to speed up the process appears to be broken.)
I found the new MacOS Agent Utility Preference Pane provided users too much information, so I disable it as part of the Jamf Pro policy to install / upgrade via Files and Processes > Execute Command (even though the vendor's screenshot features our very own @grizzly660fan).
/bin/mkdir -pv /Library/PreferencePanesDisabled ; /bin/mv -v /Library/PreferencePanes/ACSAgent.prefPane /Library/PreferencePanesDisabled/ACSAgent.prefPane
Also, the suggested How to Recover an Unresponsive macOS Endpoint procedure doesn't lend itself to automation; we're using Thycotic Privilege Manager Agent Kickstart.sh instead.
Configuration Profiles
Approved Kernel Extensions
- Approved Team ID
- Display Name:
Thycotic Software - Team ID:
UJDHBB2D6Q
- Display Name:
Privacy Preferences Policy Control
- App Access
- Identifier:
com.thycotic.privilegemanagergui - Code Requirement:
anchor apple generic and identifier "com.thycotic.privilegemanagergui" and (certificate leaf[field.1.2.840.113635.100.6.1.9] / exists / or certificate 1[field.1.2.840.113635.100.6.2.6] / exists / and certificate leaf[field.1.2.840.113635.100.6.1.13] / exists / and certificate leaf[subject.OU] = UJDHBB2D6Q) - App or Service
- Accessibility: Allow
- AppleEvents: Allow
- Receiver Identifier:
com.apple.systemevents - Receiver Code Requirement:
identifier "com.apple.systemevents" and anchor apple
- Receiver Identifier:
- SystemPolicyAllFiles: Allow
- Identifier:
Jamf Pro Scripts & Extension Attributes
Queries the macOS Thycotic Privilege Manager Agent for various settings, saves the results to the user's Desktop as an HTML file, which is then opened in Safari.
If the testAgentConnection function results in a failure, the kickstartAgent function executes settmsserver -serverUri ${thycoticURL} -installCode ${agentInstallCode} in an attempt to resolve the connection failure.
Scripts
Thycotic Privilege Manager macOS Agent Information
- While troubleshooting new installations of the macOS Thycotic Privilege Manager agent, I found myself frequently having to leverage
agentUtil.shasrootto see exactly which policies had been applied before realizing I had neglected to add the new test machine to my testing Resource group. - The HTML file includes hyperlinks to the policies in the Thycotic Privilege Manager console.
Thycotic Privilege Manager macOS Agent Diagnostics
- More robust version of Thycotic Privilege Manager macOS Agent Information
- Leverages
settmsserver -serverUri ${thycoticURL} -installCode ${agentInstallCode}to kickstart the agent - The HTML file includes hyperlinks to the policies in the Thycotic Privilege Manager console.
Thycotic Privilege Manager Agent Kickstart
- Simplified version of Thycotic Privilege Manager macOS Agent Diagnostics
- No HTML output
- Used as a remediation for Thycotic Health Check Extension Attribute
Extension Attributes
Thycotic Privilege Manager Machine ID
- Returns the Thycotic Privilege Manager Machine ID GUID
Thycotic Privilege Manager Health Check
- Validates access to
${thycoticURL}PrivilegeManager/# - Validates access to
${thycoticURL}Agent/AgentRegistration4.svc - Attempts to
updateclientitems
Please see GitHub for customization instructions.
Thycotic Privilege Manager Agent Kickstart Jamf Pro Policy
- Add the Thycotic Privilege Manager Agent Kickstart script
- Add the Thycotic Privilege Manager Health Check Extension Attribute
- Create the Thycotic Health Check Failure Smart Group:
- Criteria: Thycotic Health Check
- Operator: like
- Value: FAIL
- Create the Thycotic Privilege Manager Agent Kickstart policy
- General
- Display Name: Thycotic Privilege Manager Agent Kickstart
- Trigger: Recurring Check-in
- Execution Frequency: Ongoing
- Scripts
- Thycotic Management Agent Kickstart
- Number of Kickstart Checks
- Thycotic Agent Install Code
- Thycotic Management Agent Kickstart
- Scope
- Thycotic Health Check Failure
- General
Additional Reading
- Labels:
-
Application usage
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2021 07:49 AM
Thank you for posting this, saved me some time figuring out the PPPC and AEK. One note:
The PPPC was failing for me, I changed the Code Requirement portion to this to get it to work:
identifier "com.thycotic.privilegemanagergui" and anchor apple generic and (certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UJDHBB2D6Q)- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-16-2024 01:27 AM
Hi There,
bumping this great thread (thank you for creating it!), as I'm trying to configure PPPC FDA for Privilege Manager Security as explained here: https://docs.delinea.com/online-help/privilege-manager/agents/macos/mdm-profiles.htm
But it doesn't work.
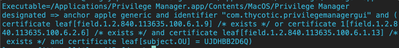
What they recommend to do is to enter the following code requirement in the config profile:
anchor apple generic and identifier "com.thycotic.acsd" and (certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = UJDHBB2D6Q)As you see the identifier (com.thycotic.acsd) differs from the one listed in this JN article.
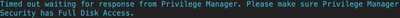
When I need to run any sudo command, it will eventually time out waiting for Privilege Manager Security to get the FDA granted:
I tried also with the code listed in this page but no luck.
When checking the team ID of the app located at /Applications/Privilege Manager.app, I get the one listed in this JN article:
None anyway will work.
I can't seem to find the "Privilege Manager Security" that they mention in their official documentation.
Do you happen to know anything about this?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-16-2024 03:14 AM
Happy New Year, @trull_sengar!
You may wish to reach out to Delinea technical support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-16-2024 04:16 AM
Hello @dan-snelson
Happy new year to you too!
I tried and got stuck on different bureaucracies, reason why I tried to ask here as well :-)
I'll try again though.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-15-2024 04:23 PM
Hi @trull_sengar I am also working on Delinea Privilege Manager and having the same issue. Did you ever get this resolved?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-18-2024 04:40 AM
Hi @afleming ,
I had still the issue with the agent version 11.4.1.
I now downloaded the latest version (12.0.0 from here), and confirm that it works perfectly.
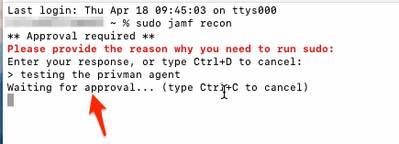
I was able to test without any issues policies such as:
- Require justification and approval when running a sudo command (see below - waiting for approval)
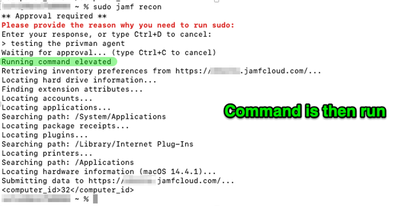
- And after approval
I have no longer experienced the issue I described in my initial post, after I installed the latest version of the agent.
Let me know if this works for you too.