Hello all,
I would like to deploy FireEye Agent using Jamf on all of our Mac.
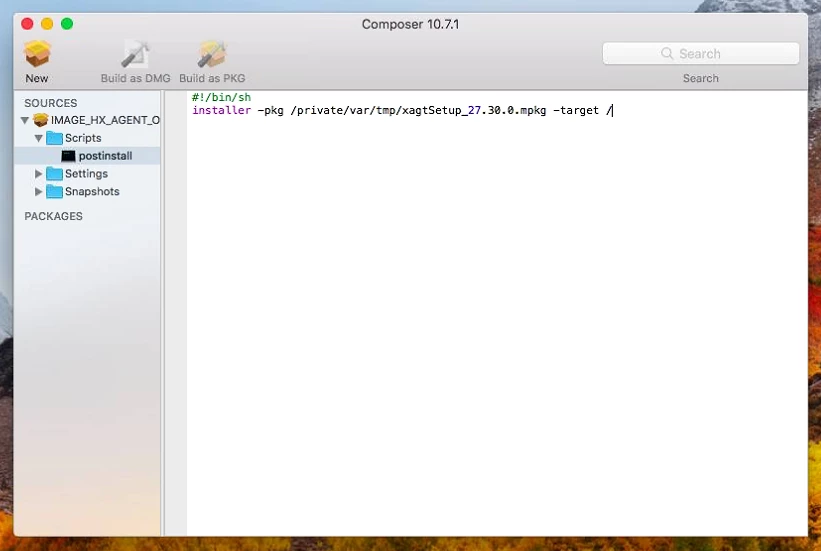
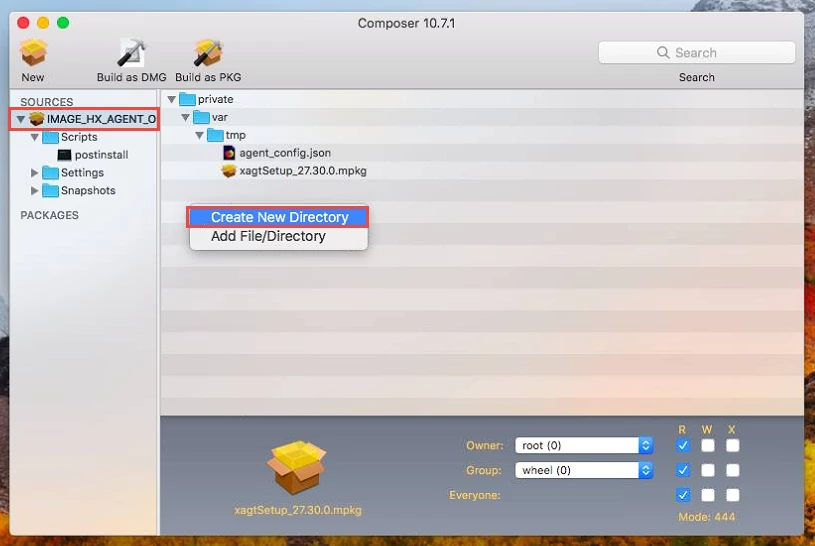
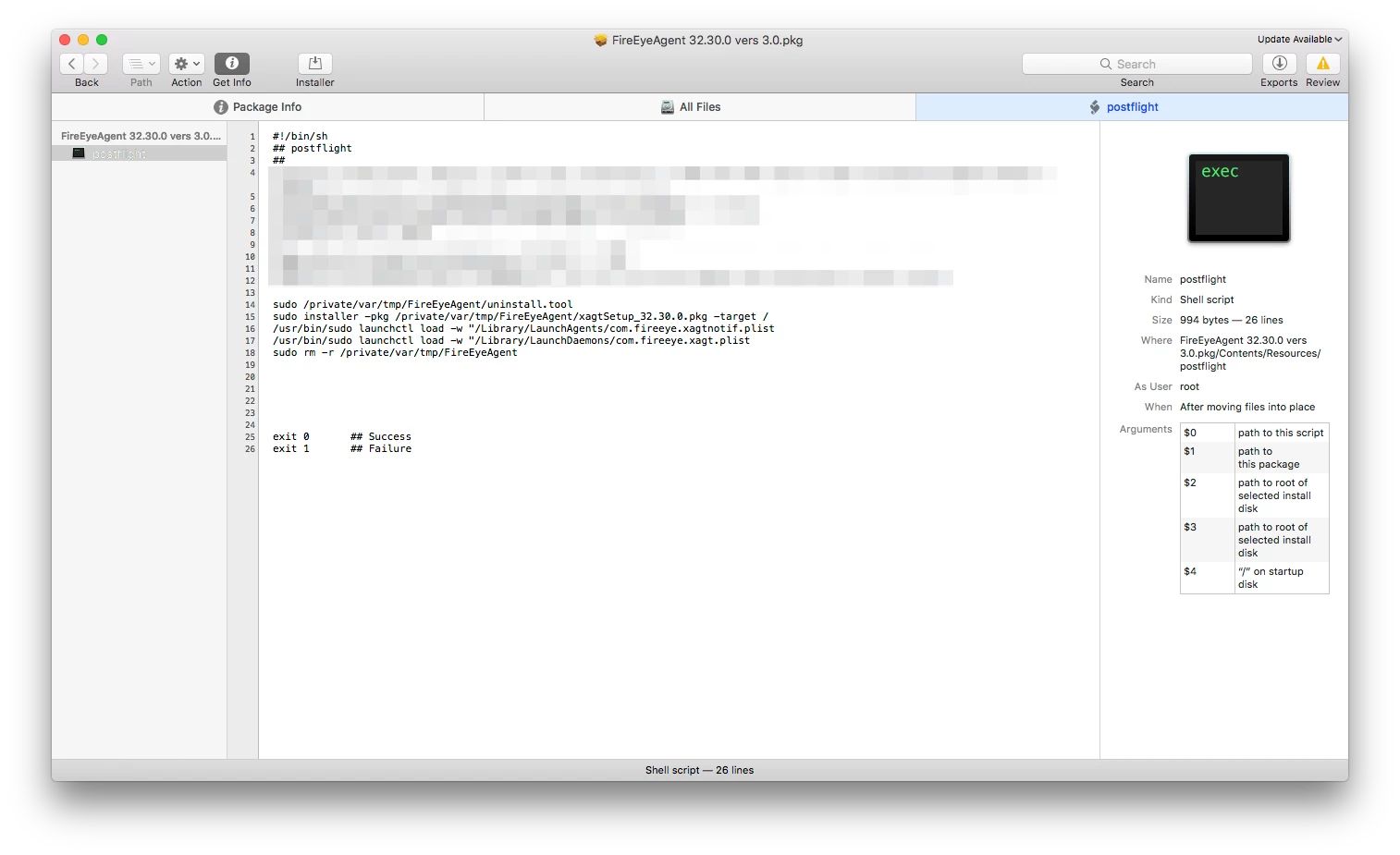
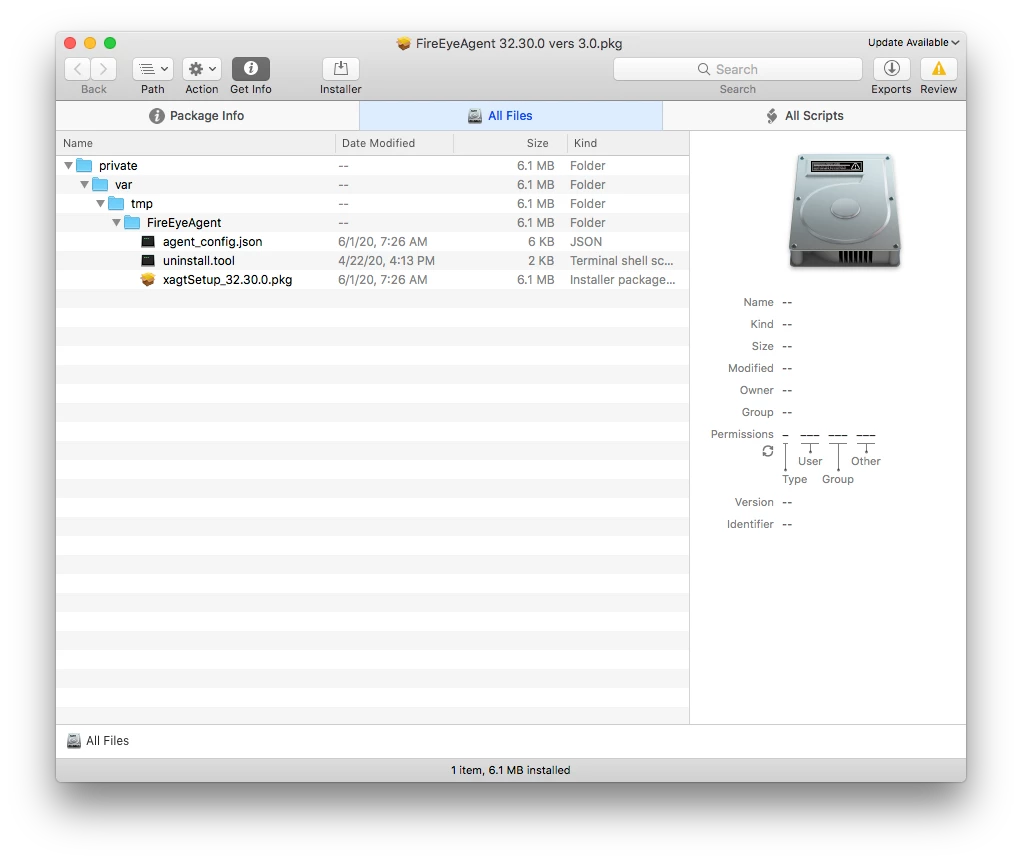
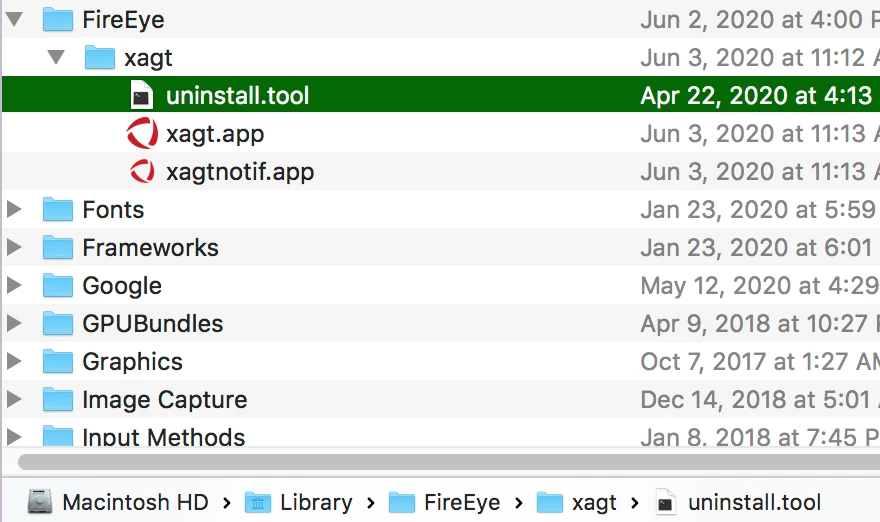
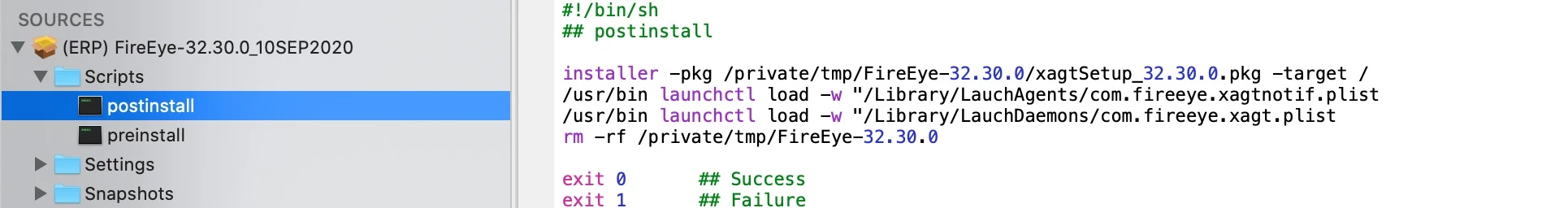
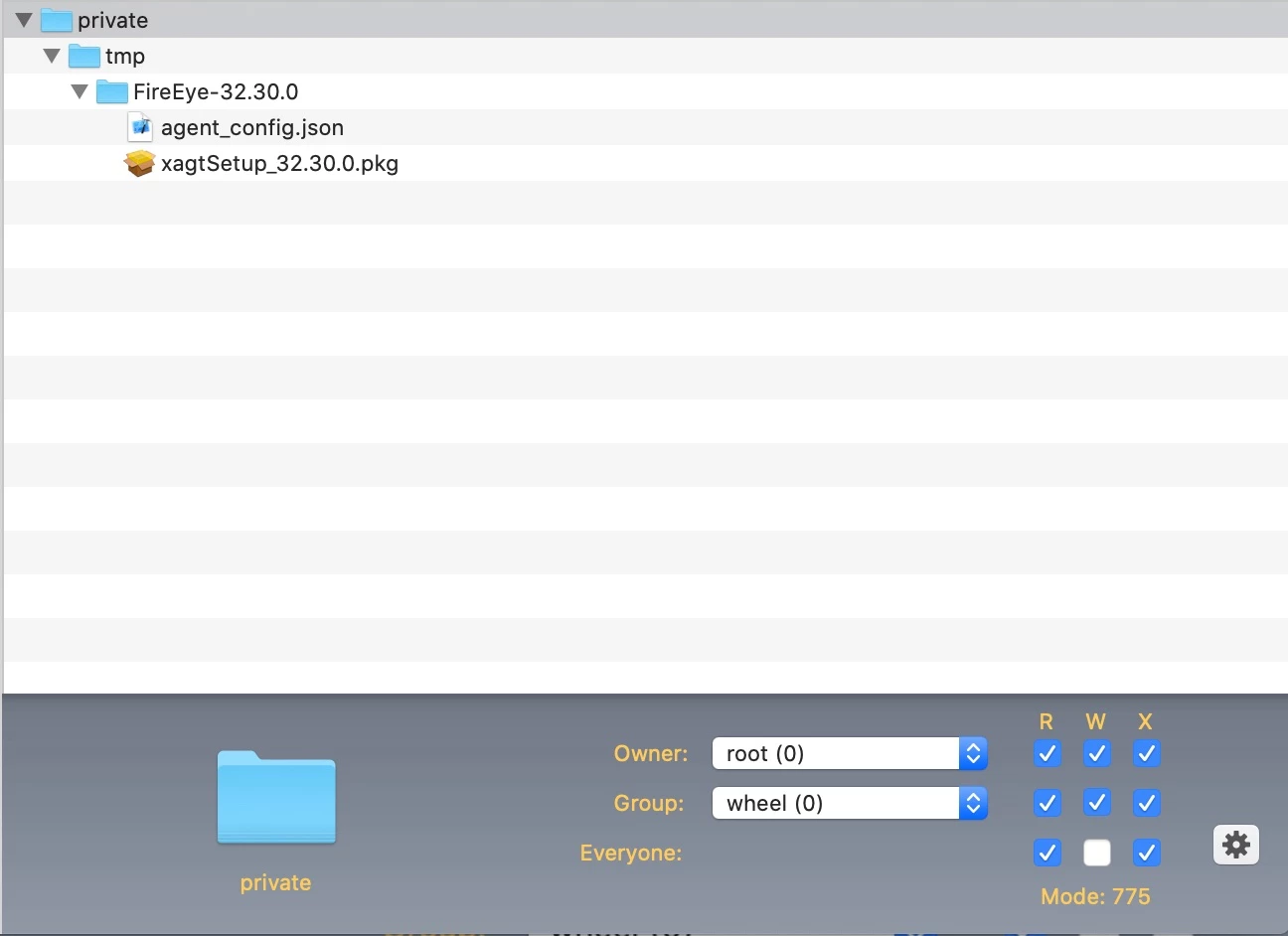
We have a FireEye.DMG that integrates a .json and the .pkg file.
Do you know how can i integrate the .json in the deployment?
Should i repack the .pkg and integrate the .json using COMPOSER then i could add a postscript ?
Sincerely,