Essentially I have an enrollment script that calls on the custom trigger "FV2" to run, all using jamfhelper.
During DEP enrollment, user needs to auth to Okta then create a local account using setup assistant. That user is an admin.
However, based on my current settings, the hidden management account gets the secure token and does not pass it off to the account created during setup assistant.
That poses a problem as now users can see the name of the hidden account, and its also kinda ugly. Secondly, without a secure token i have to push a script that uses osascript to have the user auth to get the token.
The goal, if possible is to keep the management account hidden, though that seems more and more impossibly as thats the account needed to auth to FV2 if a user is termed.
I also dont want to pester users to auth to osascript to enter their creds as its understandably sketch.
Here is my prestage enrollment
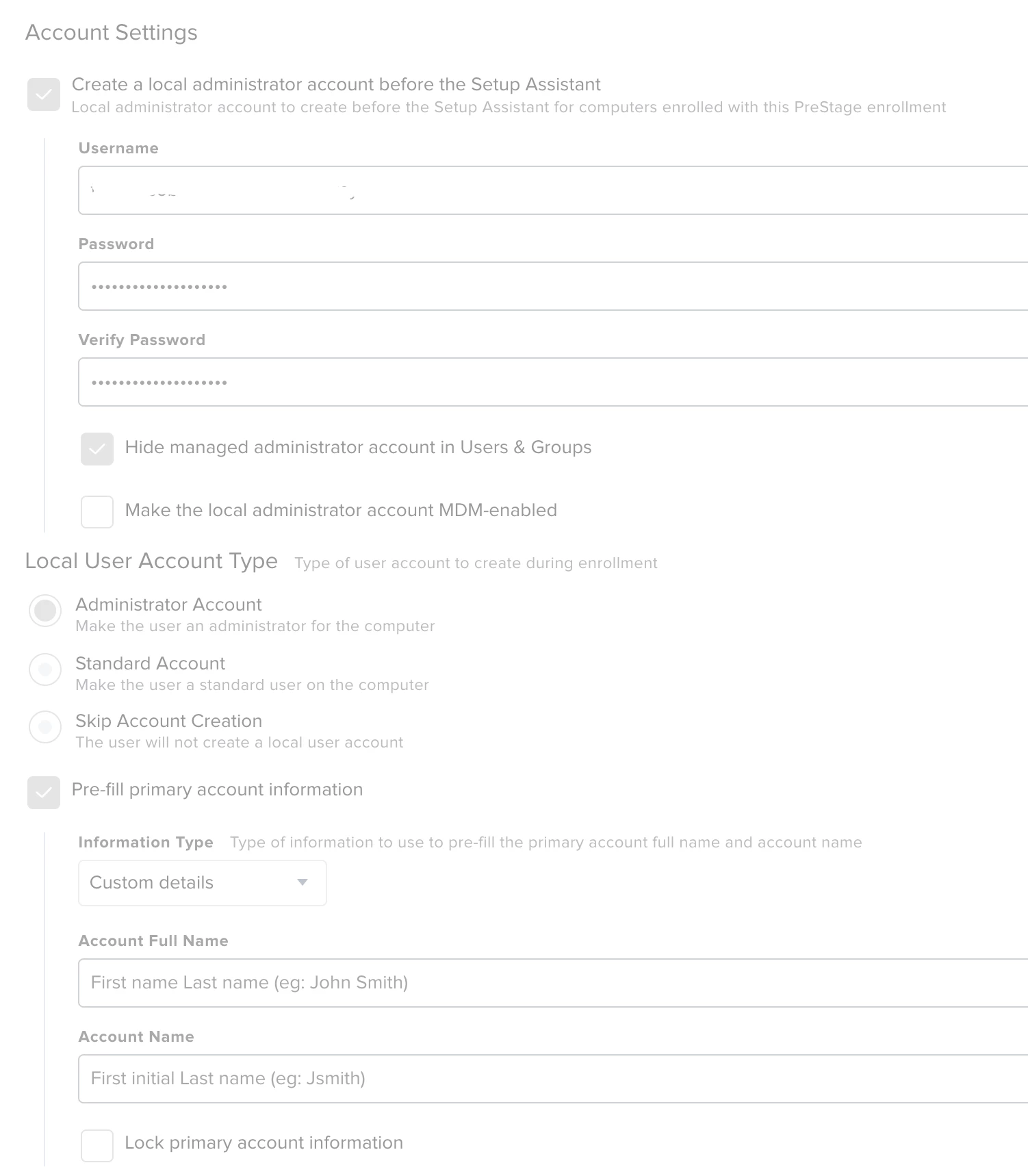
unsure if i need to check "Make the local admin account MDM enabled" or not
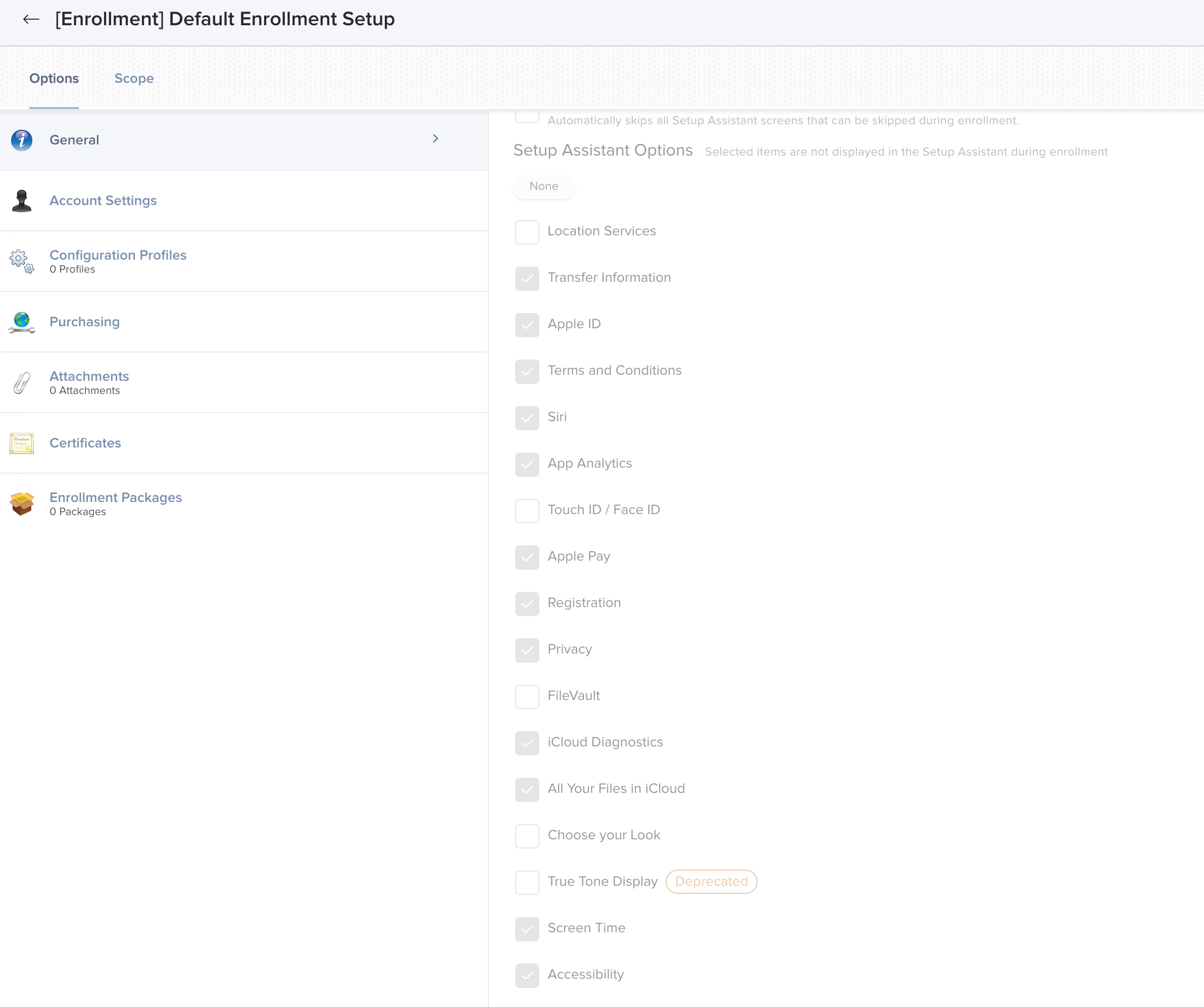
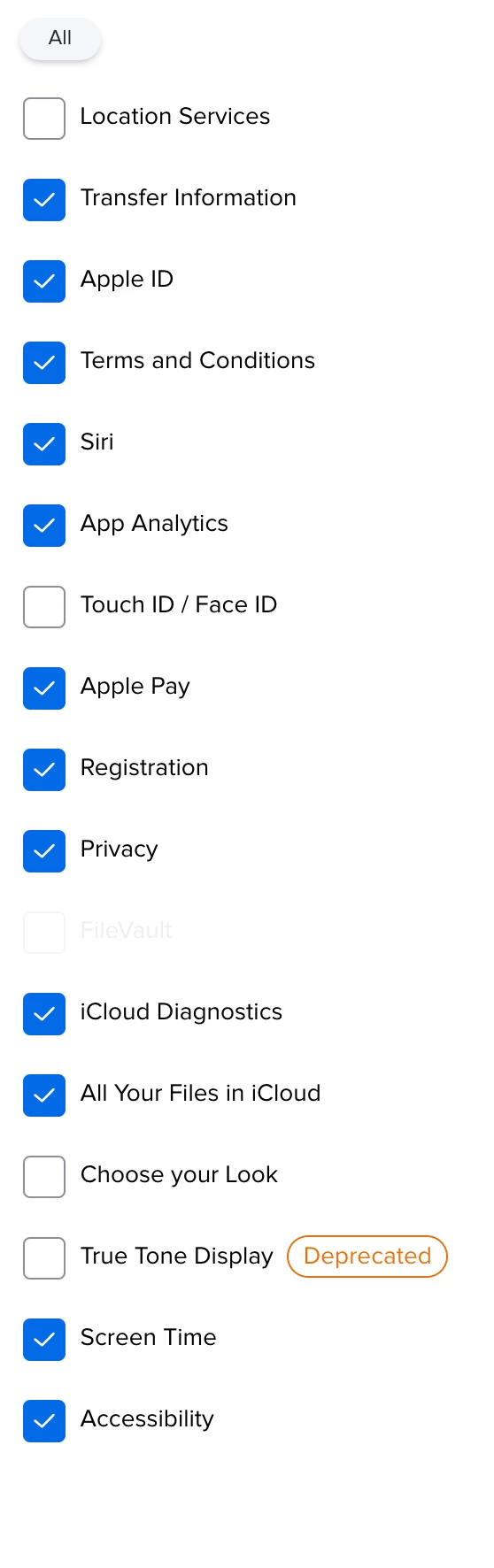
Additional oddity is that Filevault is shown as an option to skip in prestage but NOT editable/selectable when i edit the page
FV2 policy
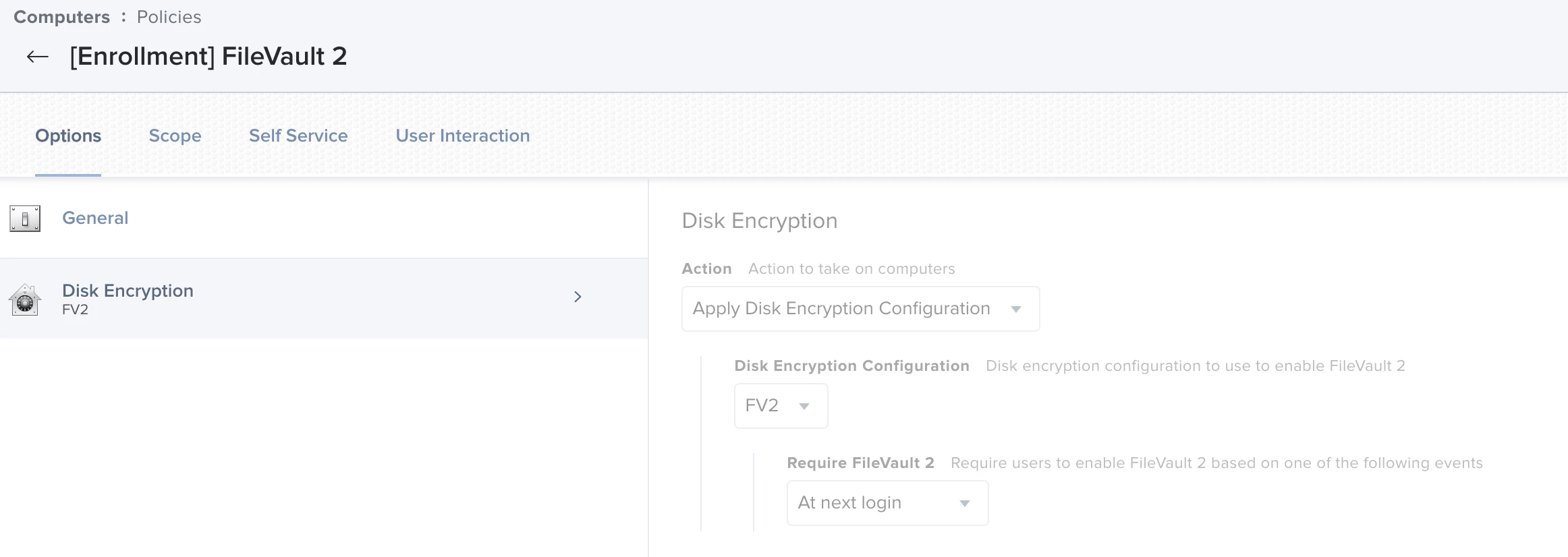
FV2 config
Any ideas on what I could be missing?
The worst part is that it seemed to be working when the old script called on DEPNotfify but I have since changed to jamfHelper so that I rely more on native apps.
Based on everything I've seen here, it looks to be correct and should work accordingly, but when i look at new hires and also the FV2 log:
- hidden management account is FV2 enabled
- FileVault 2 Enabled Users: tdyyXxxxxxXXXXXXXXX
- Disk is not encrypted
- The admin (setup assistant user) isnt on the enabled users
- Bootstrap token is no escrowed to server for any of our devices, working or not
- securetoken is DISABLED for the user
- Logs from the only FV2 enrollment show
Executing Policy [Enrollment] FileVault 2
FileVault is Off. Deferred enablement appears to be active for user '$USER'.



