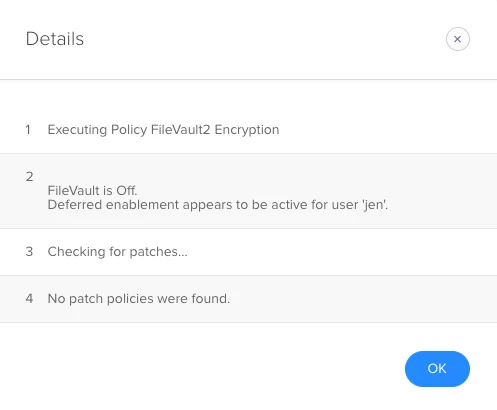
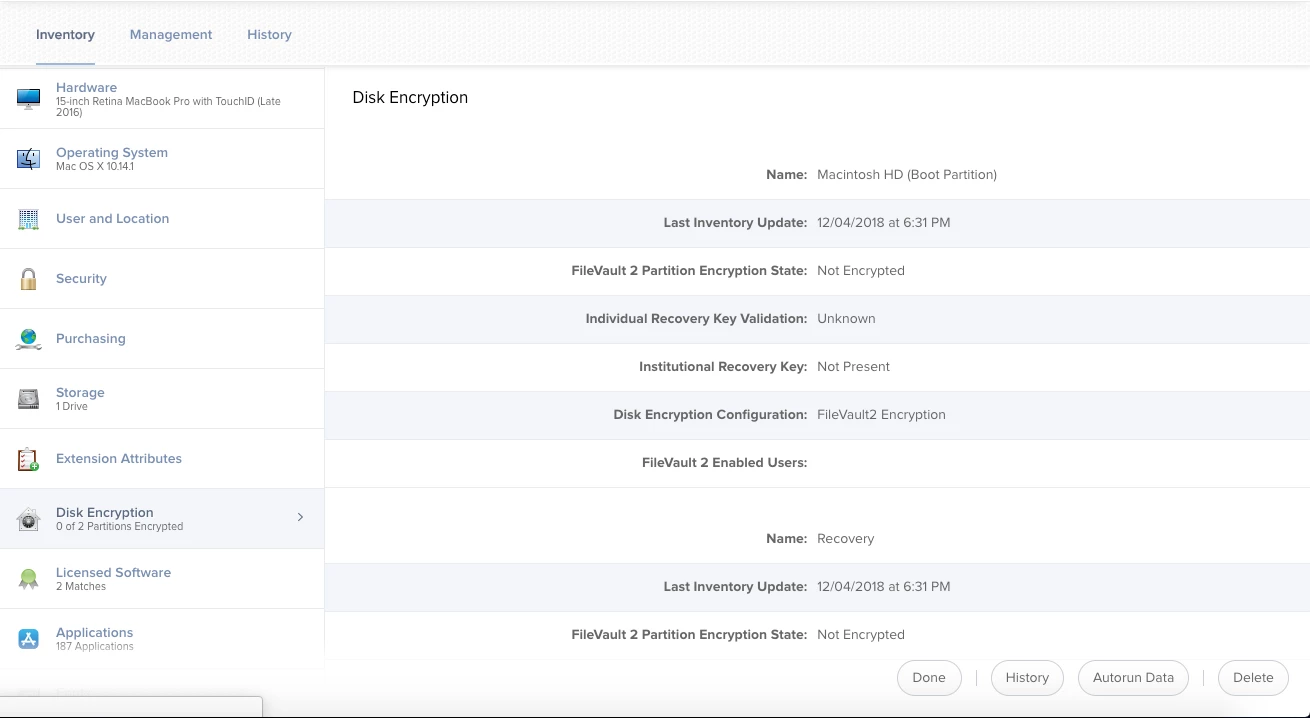
On some of our Macs when running the FileVault2 Encryption policy it seems like it successfully runs but when you check the logs you see it says "FileVault is off, deferred enablement appears to be enabled for active user: username"
Ive flushed the policy, tried to run it logged in as a different admin account, get the same message. Happening randomly on MacBooks running High Sierra or Mojave.
Any suggestions on how to resolve?
Question
FileVault2 deferred enablement
 +4
+4Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.