- Jamf Nation Community
- Products
- Jamf Pro
- Re: How to configure JAMF/CS to provide Full Disk ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2022 10:05 AM - edited 02-11-2022 10:27 AM
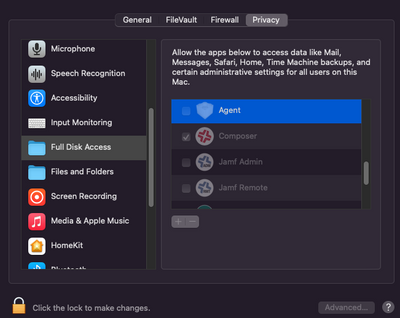
We currently are trying to setup Crowdstrike Falcon to deploy to all of our end users. We are running into an issue with the Configuration profile we setup for falcon (guide provided by CS) where it's not providing FDA access to the Agent. It places the Agent in the FDA area in System Prefs -> Security & Privacy -> Privacy -> Full Disk Access but it leaves it unchecked.
Does anyone know a solution to getting this checked with JAMF?
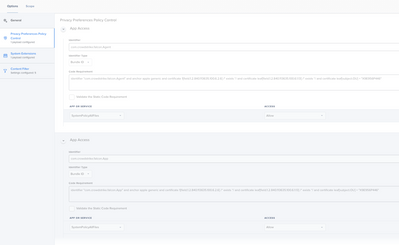
Here is a screenshot of what I'm referring to:
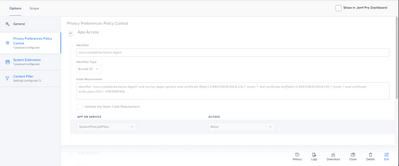
Please find screenshots of our current config profile for Falcon in JAMF below:
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2022 12:51 PM - edited 04-01-2022 12:55 PM
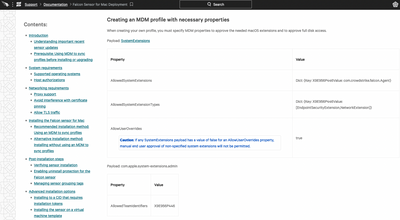
Documentation on how to create the profiles:
https://supportportal.crowdstrike.com/s/article/ka16T000000wwxpQAA
Additional documentation on how to create a profile for KEXTs (you'll want to make both config profiles following the above doc, but for the Intel, include these steps in that profile as well, or create a separate profile for KEXTs alone for the Intel, but still create two separate profiles for M1 and Intel from the first article.): https://supportportal.crowdstrike.com/s/article/ka16T000000wwxuQAA
Extra documentation
How to package Falcon sensor for Mac Installer for Jamf deployments: https://supportportal.crowdstrike.com/s/article/ka16T000000wwydQAA
How to license the Falcon sensor for Mac for Jamf Pro using a script: https://supportportal.crowdstrike.com/s/article/ka16T000000wwxzQAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-11-2022 10:55 AM
When pushing a profile to provide FDA, it will not always put the check box there, but understand that FDA has been provided.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2022 11:03 AM - edited 02-11-2022 11:04 AM
We aren't receiving alerts in our CS console for sample detections. We receive these alerts when the Checkbox is ticked for the CS Falcon agent. When unticked, those alerts do not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-11-2022 11:03 AM
Another nice-to-have in your config profile is allowing notifications for com.crowdstrike.falcon.UserAgent.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
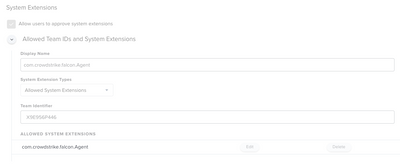
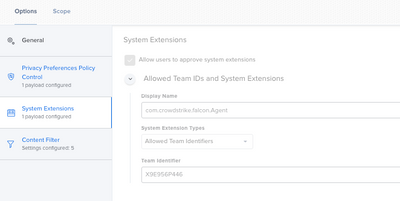
Posted on 02-14-2022 07:37 AM
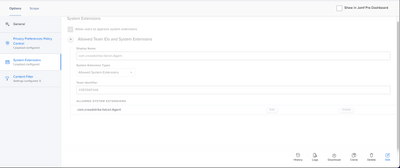
Hi, you're missing a couple of System Extension settings from Crowdstrike guide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2022 08:29 AM - edited 02-14-2022 08:31 AM
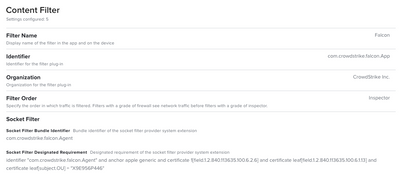
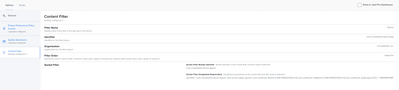
The guide has been updated. The only System Extension approval needed is your middle one.
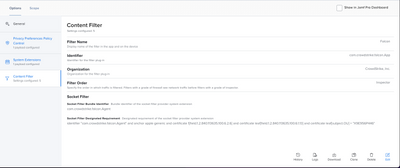
Content filter settings are also required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-14-2022 10:14 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-14-2022 10:37 AM
Unfortunately, their documentation doesn't all align at the moment.
I would go with this which was just updated last week.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-28-2022 12:28 PM
Hi there, we're using the exact same configuration that you are but we're having some crashing issues, do you happen to run a vpn on your devices? as soon as we install global protect, our devices start crashing overnight.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-02-2022 03:37 PM
We've seen some crashing as well. At this point, we believe it is tied to the combination of running CrowdStrike along with an app called AirServer. We haven't seen any problems that trace back to GlobalProtect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-14-2022 12:29 PM
The current issue we are experiencing is that CS terminal test commands are not being successfully pushed/detected in our CS console and we believe the cause is related to FDA not being ticked for the CS agent.
We noticed that when the Agent is ticked off (in the System Prefs -> Security & Privacy -> Privacy -> Full Disk Access area) in system preferences, these commands do successfully get pushed/detected in the CS console.
Some of the commands we are using to test are:
bash crowdstrike_test_critical
bash crowdstrike_test_high
bash crowdstrike_test_medium
bash crowdstrike_test_low
etc
If FDA is still granted despite not being ticked off in system preferences, why are we having this issue with these test commands not generating alerts in our console?
Is there another way to get FDA ticked/enabled through a config profile in JAMF?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 03:15 PM - edited 03-11-2022 03:22 PM
Hi all.
Just got off of a long call with CrowdStrike and you will never see the "Agent" box checked in the "Security and Privacy" and that has to do with the MDM and Apple's Full Disk Access security, however that doesn't mean that the Agent and the CS Sensor still does not have Full Disk Access to your machine. If you find where you are still not getting events reporting in, here is the fix: 1) Re-run the profile to all your machines 2)Flush all your Crowdstrike install policy logs to your machines. This will not re-install the Sensor on your machines but will force two things to happen. It will force the System Extension to reactivate on the machine and the Sensor to reactivate on the machine. You should see this in Activity monitor if it is done correctly. 
bash crowdstrike_test_low
on a test machine.
This should give you a sample detection on your CS console to look at.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-01-2022 12:25 PM
Just wanted to provide an update. We received an updated doc from Crowdstrike which actually worked. Theres so many different docs out there so its super confusing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-01-2022 12:44 PM
Nice! Where can we find this Doc, or did you get it from their Support folks? Does it have a name or some version number we can reference when asking for it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2022 12:51 PM - edited 04-01-2022 12:55 PM
Documentation on how to create the profiles:
https://supportportal.crowdstrike.com/s/article/ka16T000000wwxpQAA
Additional documentation on how to create a profile for KEXTs (you'll want to make both config profiles following the above doc, but for the Intel, include these steps in that profile as well, or create a separate profile for KEXTs alone for the Intel, but still create two separate profiles for M1 and Intel from the first article.): https://supportportal.crowdstrike.com/s/article/ka16T000000wwxuQAA
Extra documentation
How to package Falcon sensor for Mac Installer for Jamf deployments: https://supportportal.crowdstrike.com/s/article/ka16T000000wwydQAA
How to license the Falcon sensor for Mac for Jamf Pro using a script: https://supportportal.crowdstrike.com/s/article/ka16T000000wwxzQAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-01-2022 12:58 PM
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-01-2022 01:01 PM
No problem! Just wanted to also note that you will not see the FDA box checked but CS still does have FDA access nonetheless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-27-2022 12:12 PM
Hello All
I created a configuration profiles exactly the same as the instruction; however, it shows Pending in the logs. Does anybody know what the issue is? Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-27-2022 12:15 PM
I'm testing with M1 MacBook Air
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2022 09:33 PM
I am still having issues with getting Agent and Falcon.app in Privacy to be ticked for FDA. I also want to confirm what everyone is saying here. Are you all saying that FDA is allowed for both Agent and Falcon.app even though it is not showing in Privacy for FDA. I am looking at the Zero Trust Assessment in CrowdStrike and I am getting an alert that it does not detect FDA for CrowdStrike. I checked and saw my PPPC matches what has been suggested by CS, JAMF, and the screenshots here. Is anyone still having problems?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-19-2022 01:01 PM
I'm still having problems. The full disk access box is not checked. In the full disk access section, it is said that full disk access is required for both "Agent" and "Falcon". When I send the configuration file to the clients, only the object named "Agent" comes. However, the full disk access box is not checked. I haven't seen anyone able to fix this problem. The object named "Falcon" never comes to the full disk access section. Is there anyone who can solve this problem? I've looked at both the Crowdstrike and Jamf forums but haven't found a solution. Some here are saying that Falcon actually has the FDA, even if the full disk access box is unchecked. How could this be? This explanation makes no sense to me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2022 02:23 PM - edited 07-19-2022 02:24 PM
There are a number of apps that are correctly managed and don't show it in the GUI.
If you have it setup properly, I'd not worry about it. It's been stated in most places I'm frequenting that this is how it is and it is as well in my environment...no issues that we've found.
IF this isn't to your liking, open a case with Falcon and have them work with you.