How to enable FileVault 2 through JSS and add FileVault users with a single command line without using a plist file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
06-23-2015
09:45 PM
- last edited on
03-04-2025
04:40 AM
by
![]() kh-richa_mig
kh-richa_mig
At my current client, a challenge we had to overcome was to build an image that is as automated and zero touch for the user as possible, which included enabling FileVault 2 and then automatically enabling not only the user that will be using the workstation to login, but also FileVault enabling the workstation admin account and JSS Management account.
I won't go into the finer points of the decision making process, but what worked for us was to create a Disk Encryption policy in JSS using an institutional recovery key, and then set the Require user to enable FileVault 2 "At next login". I'm sure most of you know that this will enable FileVault 2, set the recovery key to an institutional key you've created and know, and automatically enable the next user that logs into the device as the FileVault 2 user, which in most cases is hopefully the user that will be using the system.
The benefit to this is that you obviously file vault encrypted the drive, and setting the user that will be using the hardware as the file vault user without needing to know his or her password, and in a fully automated manner that doesn't require any user input or knowledge of what FileVault is or how to set it or what password to set. Simple and elegant.
I'm not going to go into detail on how to create an institutional key for FileVault 2, and I hope you already know the reason why creating one would be beneficial for you, and make your life much easier, but if you need a good white paper on how to create the institutional key, I recommend Der Flounder's blog, as its pretty much the authority on anything FileVault related.
The next challenge is obviously how do you then next add other FileVault users to be able to log into the system? For us it was simple, because the only account we didn't already know the password to was the user that would be using the system, So now its just a matter of using the standard fdesetup -add command to add the additional users to FileVault, which included the local workstation admin account, and the JSS Management account, both of which we have the username and password.
The question then came up on how can we add these users without needing to create a plist file, which is the Apple recommended approach for various reasons, the most important being the fact that doing so will basically list the two most important accounts in your environment with their password in clear text in a file, that if you deploy to the workstation can potentially easily give access to said information to the user of the machine, which can potentially be every user with a Mac. So how do you overcome that?
You could either use the expect command to pass the password to the terminal input for the password, which many of you well know can be extremely tricky and complicated to do correctly, or you could make the plist accessible from an encrypted file share, which has its own complications. Something we were struggling with till the answer just came to me. Why not take the plist format, and pipe it to the command, that way theres no file to manage with passwords in open text. So the command we're using is as follows:
echo "<plist><dict><key>Username</key><string>user1</string><key>Password</key><string>password1</string><key>AdditionalUsers</key><array><dict><key>Username</key><string>user2</string><key>Password</key><string>password2</string></dict></array></dict></plist>" | fdesetup add -inputplist
It worked for me, and made our FileFault management a lot easier, so I thought I would share it with the community in the hopes that it works for you too.
I may be repeating something others have already figured out before, and if I am, I apologize for a repeat post, but I hope it helps some out there with your setups.
Cheers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-24-2015 05:26 AM
Nice idea, thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-24-2015 05:48 AM
Nice find with the pipe into "fdesetup add -inputplist"! Way more secure and it seems to work great in testing so far.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-24-2015 09:51 AM
I went a step further and exported it to a plist file that I parse down, and then read it into Casper as an extension attribute. This is the command to save said recovery key plist:
fdesetup enable -inputplist < /Path/to/Plist.plist -outputplist >> /Path/to/WhereYouWantRecoveryKey.txt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-15-2015 07:24 AM
Odd. The command runs fine from the command line, but when run through a Policy's Execute Command feature I get an error.
Executing Policy FileVault2 - Enable Local Users... Running command echo "<plist><dict><key>Username</key><string>dngoperator</string><key>Password</key><string>mypassword</string><key>AdditionalUsers</key><array><dict><key>Username</key><string>dngsupport</string><key>Password</key><string>mypassword</string></dict></array></dict></plist>" | fdesetup add -inputplist... sh: -c: line 0: syntax error near unexpected token `<' sh: -c: line 0: `echo "<plist><dict><key>Username</key><string>dngoperator</string><key>Password</key><string>mypassword</string><key>AdditionalUsers</key><array><dict><key>Username</key><string>dngsupport</string><key>Password</key><string>mypassword</string></dict></array></dict></plist>" | fdesetup add -inputplist >& '/Library/Application Support/JAMF/tmp/6507.tmp''
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-15-2015 07:46 AM
@cwaldrip if you are running version 9.72 you might be encountering defect (D-008699) where commands that use double-quotes aren't executing properly from the Execute Command box under the Files and Processes payload. I came across this with some lpadmin commands. I had to change all my commands to include only single quotes. While that worked for my lpadmin commands, I am not sure you could get away with doing that in this instance. You might want to log a support request with JAMF over this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-15-2015 07:49 AM
Why not just put this into a script instead of the Run Command anyway? I don't trust putting sensitive items into the Run Command field. Sometimes the stuff run from there ends up showing in the system.log. Do you really want to risk having any passwords showing up in plain text in the system.log?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
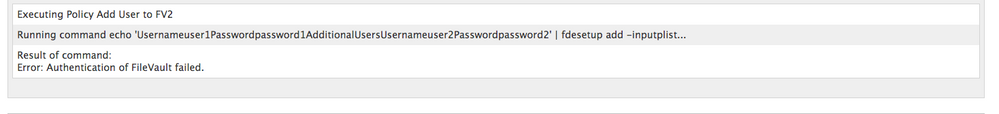
Posted on 07-15-2015 01:13 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-21-2016 01:18 PM
Hi all,
can someone explain this process to me? I currently use the JAMF script to add AD users to FV. Essentially they get prompted for a password when they login to the machine, but i've noticed incositencies.
What fields in the PLIST need to be filled out?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-03-2017 05:28 AM
Will this also work for configurations using both individual and institutional keys?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-18-2017 04:50 AM
Under 10.12.5: Anyone seeing
Running command echo "<plist><dict><key>Username</key><string>want2beadded</string><key>Password</key><string>secretpw</string></dict></plist>" | fdesetup add -inputplist...
Result of command:
Error: No users were specified. Use -usertoadd to specify a user.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-18-2017 05:39 AM
Sorry! My bad: Somehow forgot the second part of the command...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-18-2017 05:07 AM
Hi, I'm trying to run this on 10.12.6 but it keeps stating it needs root access. Is there an updated version of this script? What would I need to change if it is a version issue?
any help appreciated, cheers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-21-2020 02:04 PM
the command is corrected, use this:
#!/bin/sh
echo "<plist><dict><key>Username</key><string>user1</string><key>Password</key><string>password1</string><key>AdditionalUsers</key><array><dict><key>Username</key><string>user2</string><key>Password</key><string>password2</string></dict></array></dict></plist>" | fdesetup enable -inputplist